Symantec to acquire Blue Coat for $4.65 billion
Security company Symantec is to acquire Web security provider Blue Coat for US$4.65 billion in cash in a deal that will broaden the portfolio of security technologies the combined company can offer customers as they move to the cloud.The deal, which is expected to be closed by the third quarter, will also see Greg Clark, CEO of Blue Coat, taking over as CEO of Symantec and joining its board at the the closing of the transaction. Symantec, well-known for its anti-virus software, has been looking out for a new CEO since April after it was announced that its CEO Michael Brown was stepping down, following poor financial results. Ajei Gopal was appointed as interim president and chief operating officer.To read this article in full or to leave a comment, please click here
 Let’s PLAY!
Let’s PLAY!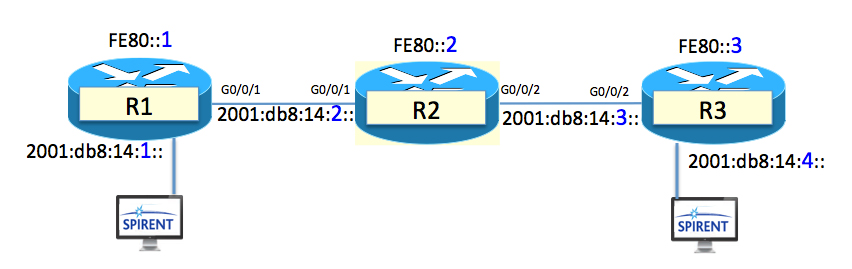


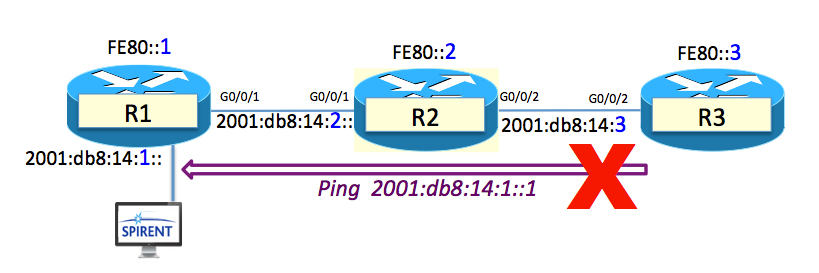
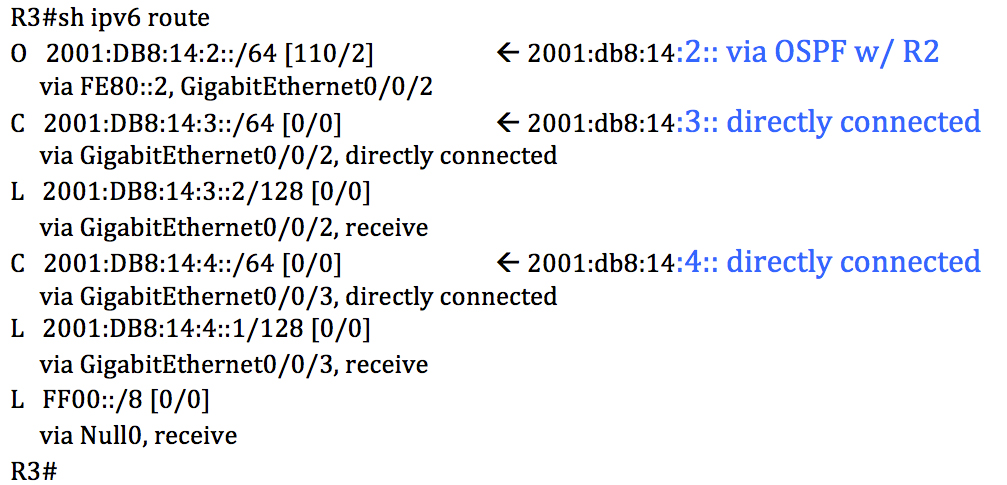


 DigitalOcean's CTO, Simplivity's latest, and more.
DigitalOcean's CTO, Simplivity's latest, and more. The plan is to automate the WAN.
The plan is to automate the WAN.