Congrats to the Winners of the DockerCon Diversity Scholarship!
The DockerCon team is excited to announce the recipients of our inaugural DockerCon Diversity Scholarship Program! The DockerCon Diversity Scholarship aims to provide support and guidance to members of the Docker Community who are traditionally underrepresented through mentorship and a … ContinuedPacket Blast: Top Tech Blogs, May 27
We collect the top expert content in the infrastructure community and fire it along the priority queue.
Optimize Your Data Center: Ditch the Legacy Technologies
In our journey toward two-switch data center we covered:
It’s time for the next step: get rid of legacy technologies like six 1GE interfaces per server or two FC interface cards in every server.
Need more details? Watch the Designing Private Cloud Infrastructure webinar. How about an interactive discussion? Register for the Building Next-Generation Data Center course.
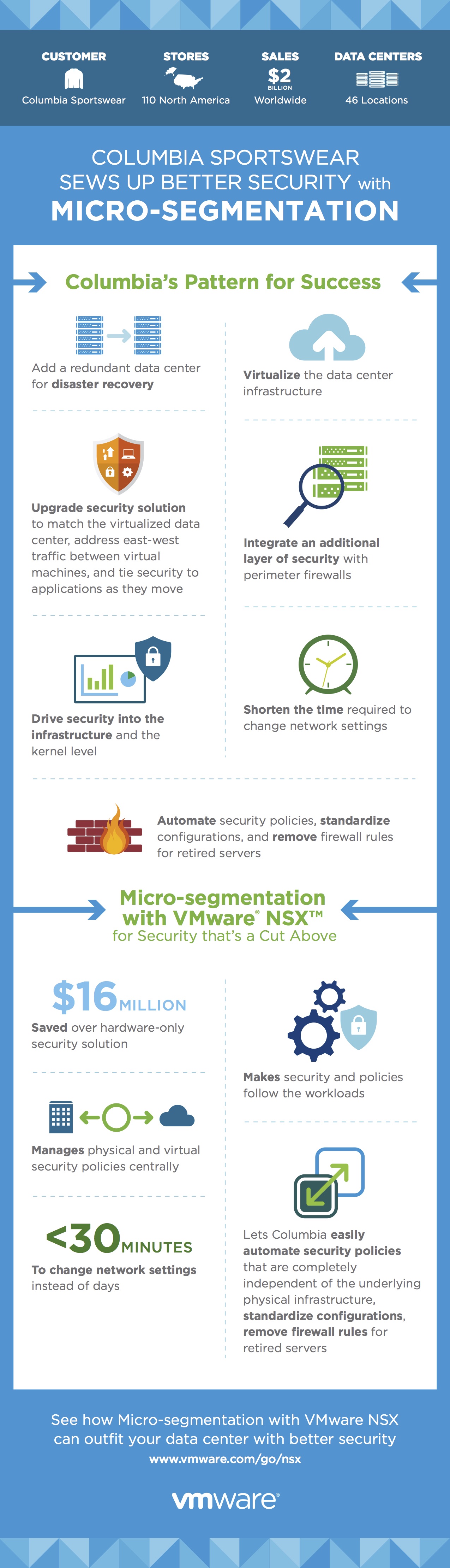
Micro-Fiber, Meet Micro-Segmentation! Columbia Sportswear Virtualizes the Network, Saves Millions
With 110 stores in North America, 46 data center locations, and $2 billion in revenue, Columbia Sportswear is constantly processing huge amounts of data—data whose security was being compromised by their inadequate hardware-defined data center.
When Columbia Sportswear virtualized their network, they not only stepped up their security; they also saved $16 million over a comparable hardware-based security approach.
Download our free ebook: Redefining Networking with Network Virtualization
How? Find out here. Follow their process step by step in the infographic below.
The post Micro-Fiber, Meet Micro-Segmentation! Columbia Sportswear Virtualizes the Network, Saves Millions appeared first on The Network Virtualization Blog.
What is MP-BGP – Multiprotocol BGP
MP-BGP (Multiprotocol BGP) is an extensions to BGP protocol. Standard BGP only supports IPv4 unicast address family, whereas MP-BGP supports more than 15 different BGP address families. RFC4760 defines the extensions for BGP protocol and states that ” in order to bring extra functionality to BGP protocol, new BGP AFI (Address Family Identifier) and BGP SAFI […]
The post What is MP-BGP – Multiprotocol BGP appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Hyperconvergence: The DIY Approach
Here's what to consider for building your own hyperconverged system.
After Cloud Deployment, What’s Next?
Enterprises should maximize their cloud investment with analytics to optimize operations.
EP06: Tech Lesson – Understanding Basic Network Traffic
In this episode of Rockstar SE Jacob Hess and Terry Kim discuss basic network traffic concepts. They break down topics such as collision domains and broadcast domains and how those concepts relate to network traffic and the world of network engineering. Join them in this Tech Lesson to learn more and don’t forget to download your free PDF!
Tech Lesson PDF: Understanding Basic Network Traffic