0
Intel beefs up VR ammo with Extreme Edition Core i7 chips
Intel considers virtual reality a key growth vector as it reshapes to survive in a post-PC world, and new Core i7 Extreme Edition chips will play a big role in that transition.The new chips, code-named Broadwell-E, are speed demons with up to 10 cores, a new high for Intel PC chips. Primarily for gaming PCs, the new chips will also go in desktops certified to work with headsets like Oculus Rift and HTC Vive.The Core i7-6900 series and 6800 series chips are targeted at enthusiasts looking for the latest and greatest technologies in PCs. These chips can be overclocked and unlocked, which could instantly upgrade PC performance by cranking up CPU frequency.To read this article in full or to leave a comment, please click here
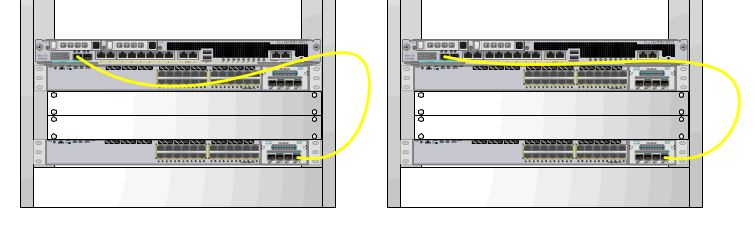 The image on the right ticks the box for me. There’s no room for a dedicated 1RU horizontal cable manager, but there is room for a zero-RU strain relief bar (as seen below). The result is a relatively neat cabling job. It’s no work of art, but it’s functional.
The image on the right ticks the box for me. There’s no room for a dedicated 1RU horizontal cable manager, but there is room for a zero-RU strain relief bar (as seen below). The result is a relatively neat cabling job. It’s no work of art, but it’s functional. A strain-relief bar is a cheap metal bar that you can bolt on when you rack-mount your switch. It allows you to velcro your fiber patches to the bar, taking the strain to help prevent breaks and preventing the dreaded cable droop. You should, of course, take care to ensure you don’t block access to any field-replaceable units, cards or ports on your network device.
A strain-relief bar is a cheap metal bar that you can bolt on when you rack-mount your switch. It allows you to velcro your fiber patches to the bar, taking the strain to help prevent breaks and preventing the dreaded cable droop. You should, of course, take care to ensure you don’t block access to any field-replaceable units, cards or ports on your network device.