Day Two Cloud 193: Should You Get A Cloud Networking Cert?
On today's Day Two Cloud we explore cloud networking certifications. Who do these certs make sense for? Which clouds should you focus on? What do certifications typically cover? Where do third-party devices such as firewalls and load balancers fit into the certification picture? If you're an old-school CLI jockey coming into cloud networking, how should you approach concepts such as Infrastructure as Code (IaC)?Day Two Cloud 193: Should You Get A Cloud Networking Cert?
On today's Day Two Cloud we explore cloud networking certifications. Who do these certs make sense for? Which clouds should you focus on? What do certifications typically cover? Where do third-party devices such as firewalls and load balancers fit into the certification picture? If you're an old-school CLI jockey coming into cloud networking, how should you approach concepts such as Infrastructure as Code (IaC)?
The post Day Two Cloud 193: Should You Get A Cloud Networking Cert? appeared first on Packet Pushers.
How HPC and Amazon EC2 Hpc6a Instances Are Accelerating Engineering Innovation
Sponsored Feature: The transformative power of modern engineering is nothing short of extraordinary. …
How HPC and Amazon EC2 Hpc6a Instances Are Accelerating Engineering Innovation was written by Martin Courtney at The Next Platform.
Silent Hosts in EVPN Fabrics
The Dynamic MAC Learning versus EVPN blog post triggered tons of interesting responses describing edge cases and vendor bugs implementation details, including an age-old case of silent hosts described by Nitzan:
Few years ago in EVPN network, I saw drops on the multicast queue (ingress replication goes to that queue). After analyzing it we found that the root cause is vMotion (the hosts in that VLAN are silent) which starts at a very high rate before the source leaf learns the destination MAC.
It turns out that the behavior they experienced was caused by a particularly slow EVPN implementation, so it’s not exactly the case of silent hosts, but let’s dig deeper into what could happen when you do have silent hosts attached to an EVPN fabric.
Silent Hosts in EVPN Fabrics
The Dynamic MAC Learning versus EVPN blog post triggered tons of interesting responses describing edge cases and vendor bugs implementation details, including an age-old case of silent hosts described by Nitzan:
Few years ago in EVPN network, I saw drops on the multicast queue (ingress replication goes to that queue). After analyzing it we found that the root cause is vMotion (the hosts in that VLAN are silent) which starts at a very high rate before the source leaf learns the destination MAC.
It turns out that the behavior they experienced was caused by a particularly slow EVPN implementation, so it’s not exactly the case of silent hosts, but let’s dig deeper into what could happen when you do have silent hosts attached to an EVPN fabric.
AMD Says AI Is The Number One Priority Right Now
When it comes to an economy, you get what we collectively expect. …
AMD Says AI Is The Number One Priority Right Now was written by Timothy Prickett Morgan at The Next Platform.
Community Spotlight series: Calico Open Source user insights from Saurabh Mishra
In this issue of the Calico Community Spotlight series, I’ve asked Saurabh Mishra from Vodafone to share his experience with Kubernetes and Calico Open Source. Let’s take a look at how Saurabh started his Kubernetes journey and the insights he gained from Calico Open Source.
Q: Please tell us a little bit about yourself, including where you currently work and what you do there.
I am working as a DevOps Manager with Vodafone Group. I am responsible for managing Kubernetes and cloud-based environments. I’m particularly interested in all things related to cloud, automation, machine learning, and DevOps.
Q: What orchestrator(s) have you been using?
Kubernetes.
Q: What cloud infrastructure(s) has been a part of your projects?
Amazon Elastic Kubernetes Service (EKS) and Google Kubernetes Engine (GKE).
Q: There are many people who are just getting started with Kubernetes and might have a lot of questions. Could you please talk a little bit about your own journey?
Kubernetes is a fully open-source project. It’s purposely designed this way so it can work with other open-source tools to create continuous improvements and innovations. In our team, we are using Kubernetes in non-production and production environments to run and manage critical Continue reading
Take Ansible validated content to the next level with Event-Driven Ansible
.png?width=1200&height=675&name=Validated%20content%20with%20event-driven%20ansible%20twitter%20(1).png)
Cloud computing has become an essential factor in IT transformation and business innovation. The highly dynamic nature of cloud environments, where new resources are constantly being added and removed, poses new challenges. One of the main challenges organizations face is the lack of visibility into the cloud environment. As cloud computing continues to grow in complexity, it can be challenging to keep track of all the different resources and applications that make up the infrastructure. This lack of visibility can make it difficult to maintain security policies and configurations, making the infrastructure vulnerable to attacks.
In this context, another challenge is the need to maintain compliance with industry regulations and standards. Depending on the industry and location, there may be specific regulations that organizations must comply with when storing and processing sensitive data in the cloud. Ensuring compliance can be a time-consuming and costly process.
Without automation and proactive monitoring, cloud environments are difficult and complex to manage. In this context, Ansible offers a plethora of tools, such as Ansible validated content and Event-Driven Ansible, that can help you to successfully mitigate security threats while also streamlining your operations and reducing costs.
In this blog post, we will show you Continue reading
Cloudflare is faster than Netskope and Zscaler across LATAM

This post is also available in Español and Português.
Last CIO Week, we showed you how our network stacks up against competitors across several countries. We demonstrated with our tests that Cloudflare Access is 38% faster than ZScaler (ZPA) worldwide.
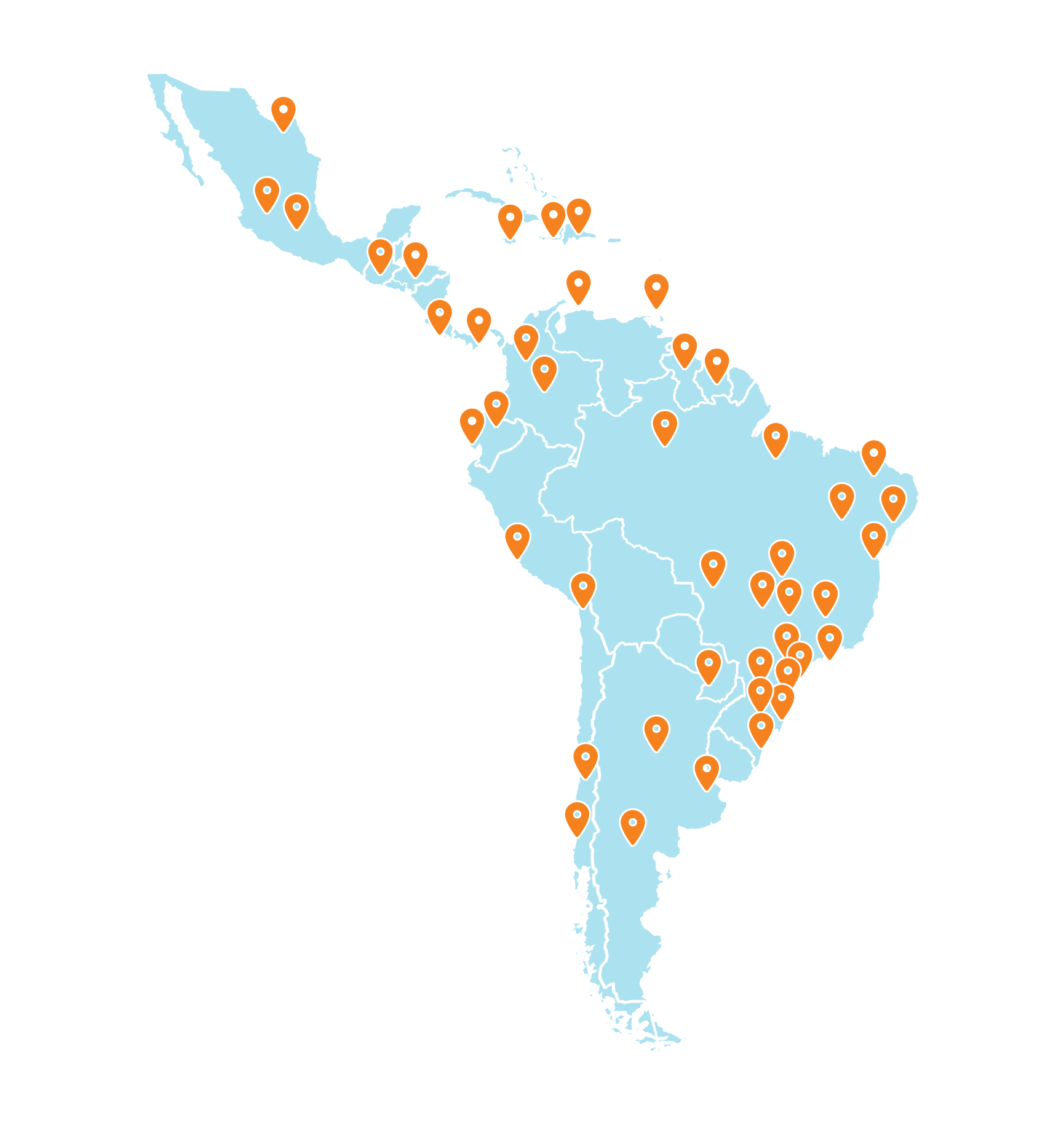
Today we wanted to focus on LATAM and show how our network performed against Zscaler and Netskope in Argentina, Brazil, Chile, Colombia, Costa Rica, Ecuador, Mexico, Peru, Uruguay and Venezuela.
With 47 data centers across Latin America and Caribbean, Cloudflare has the largest number of SASE Points of Presence across all vendors, meaning we can offer our Zero Trust services closer to the end user and reduce unwanted latency.
We’ve run a series of tests comparing our Zero Trust Network Access product against Zscaler and Netskope’s comparable products.
For each of these tests, we used 95th percentile Time to First Byte and Response tests, which measure the time it takes for a user to make a request, and get the start of the response (Time to First Byte), and the end of the response (Response). These tests were designed with the goal of trying to measure performance from an end-user perspective.
In this blog we’re going to talk about Continue reading
Small Site EBGP-Only Design
One of my subscribers found an unusual BGP specimen in the wild:
- It was a small site with two core switches and a WAN edge router
- The site had VPN concentrators running in virtual machines
- The WAN edge router was running BGP across WAN IPsec tunnels
- The VPN concentrators were running BGP with core switches.
So far so good, and kudos to whoever realized BGP is the only sane protocol to run between virtual machines and network core. However, the routing in the network core was implemented with EBGP sessions between the three core devices, and my subscriber thought the correct way to do it would be to use IBGP and OSPF.