0
Not Tor, MIT’s Vuvuzela messaging system uses ‘noise’ to ensure privacy
As privacy of The Onion Router (Tor) network comes into question, MIT researchers say they have devised a secure system called Vuvuzela that makes text messaging sent through it untraceable and that could be more secure than Tor when it comes to hiding who is talking to whom.While it’s not ready for prime time, the messaging system makes it extremely difficult for attackers to find out which connected users are communicating with which others or whether they are sending or receiving messages at all, the researchers say in “Vuvuzela: Scalable Private Messaging Resistant to Traffic Analysis”.To read this article in full or to leave a comment, please click here
 The company is contributing its code to the open source community.
The company is contributing its code to the open source community. Huawei shares the high points of the 2015 OPNFV Summit in a featured video summary. Watch now!
Huawei shares the high points of the 2015 OPNFV Summit in a featured video summary. Watch now! With the holiday season in full swing, it's only fitting that we continue to spread cheer, joy and a faster Internet around the world. To start the season we begin in Canada with NHL rivals Montreal and Vancouver, our 70th and 71st points of presence (PoPs) globally. Montreal and Vancouver, the 2nd and 3rd largest Canadian metropolitan areas, respectively, join our existing PoP in Canada's largest,
With the holiday season in full swing, it's only fitting that we continue to spread cheer, joy and a faster Internet around the world. To start the season we begin in Canada with NHL rivals Montreal and Vancouver, our 70th and 71st points of presence (PoPs) globally. Montreal and Vancouver, the 2nd and 3rd largest Canadian metropolitan areas, respectively, join our existing PoP in Canada's largest, 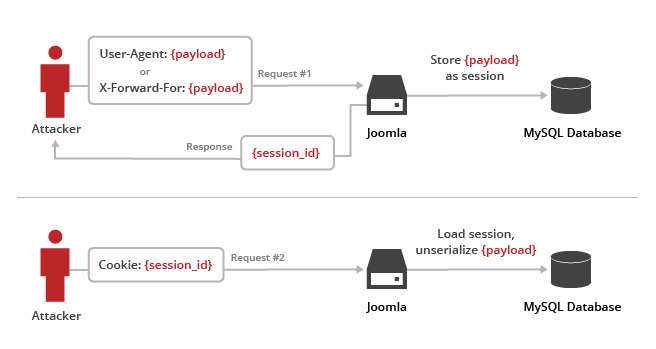
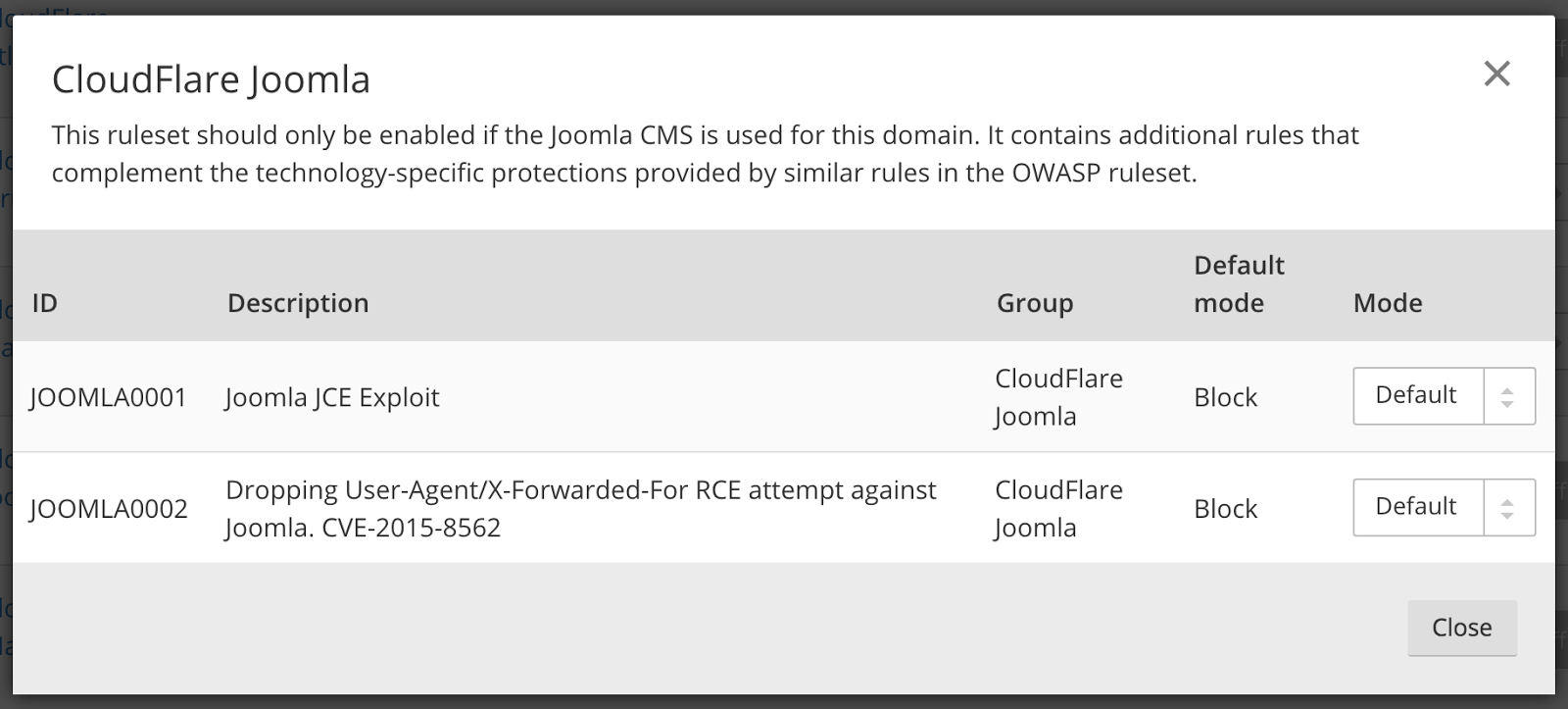
 Brocade's Robert McBride & Vikram Singh answer DemoFriday questions. Read for more insights on how to simplify vCPE management.
Brocade's Robert McBride & Vikram Singh answer DemoFriday questions. Read for more insights on how to simplify vCPE management.
