Edge Computing in Networking
The post Edge Computing in Networking appeared first on Noction.
The post Edge Computing in Networking appeared first on Noction.
I wanted to include a few examples of BGP bugs causing widespread disruption in the Network Security Fallacies presentation. I tried to find what happened when someone announced beacon prefixes with unknown optional transitive attributes (which should have been passed without complaints but weren’t) without knowing when it happened or who did it.
Trying to find the answer on Google proved to be a Mission Impossible – regardless of how I structured my query, I got tons of results that seemed relevant to a subset of the search words but nowhere near what I was looking for. Maybe I would get luckier with a tool that’s supposed to have ingested all the world’s knowledge and seems to (according to overexcited claims) understand what it’s talking about.
I wanted to include a few examples of BGP bugs causing widespread disruption in the Network Security Fallacies presentation. I tried to find what happened when someone announced beacon prefixes with unknown optional transitive attributes (which should have been passed without complaints but weren’t) without knowing when it happened or who did it.
Trying to find the answer on Google proved to be a Mission Impossible – regardless of how I structured my query, I got tons of results that seemed relevant to a subset of the search words but nowhere near what I was looking for. Maybe I would get luckier with a tool that’s supposed to have ingested all the world’s knowledge and seems to (according to overexcited claims) understand what it’s talking about.
It’s roundtable time at the Hedge! Eyvonne Sharp, Tom Ammon, and I start the conversation talking about the SONiC open source NOS, and then wander into using open source, build versus buy, and finally complexity in design and deployment.
Thanks for listening–if you have an idea for a Hedge episode, would like to be a guest, or know someone you think would be a good guest, let one us know!
 Show topic from Network Break Episode 423
Show topic from Network Break Episode 423
 Show topic from Network Break Episode 423
Show topic from Network Break Episode 423
On today's Day Two Cloud podcast we talk through out-of-band management network design with sponsor ZPE Systems. If your idea of OOB management is a jump box and some terminal servers, there’s a lot more to the story when you bring automation tooling into the picture. We'll learn how ZPE gear works and talk with customer Vapor IO about using ZPE gear in its edge compute sites.
The post Day Two Cloud 188: Out-Of-Band Management And Infrastructure Automation With ZPE Systems (Sponsored) appeared first on Packet Pushers.
We could have a long, thoughtful, and important conversation about the way AI is transforming the world. …
Cerebras Smashes AI Wide Open, Countering Hypocrites was written by Timothy Prickett Morgan at The Next Platform.


Over the past 24 hours, Cloudflare has observed HTTP DDoS attacks targeting university websites in Australia. Universities were the first of several groups publicly targeted by the pro-Russian hacker group Killnet and their affiliate AnonymousSudan, as revealed in a recent Telegram post. The threat actors called for additional attacks against 8 universities, 10 airports, and 8 hospital websites in Australia beginning on Tuesday, March 28.
Killnet is a loosely formed group of individuals who collaborate via Telegram. Their Telegram channels provide a space for pro-Russian sympathizers to volunteer their expertise by participating in cyberattacks against western interests.
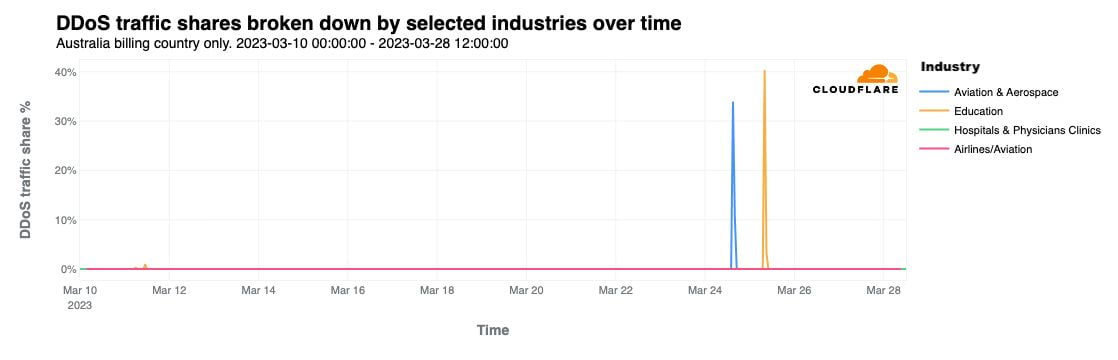
This is not the first time Cloudflare has reported on Killnet activity. On February 2, 2023 we noted in a blog that a pro-Russian hacktivist group — claiming to be part of Killnet — was targeting multiple healthcare organizations in the US. In October 2022, Killnet called to attack US airport websites, and attacked the US Treasury the following month.
As seen with past attacks from this group, these most recent attacks do not seem to be originating from a single botnet, and the attack methods and sources seem to vary, suggesting Continue reading
SPONSORED: Ransomware may currently be the biggest bogeyman for cybersecurity pros, law enforcement, and governments, but it shouldn’t divert us from more traditional, but still very disruptive threats. …
DDoS DNS attacks are old-school, unsophisticated … and they’re back was written by Martin Courtney at The Next Platform.
An ipSpace.net subscriber sent me this question:
I am on job hunting. I have secured an interview and they will probably ask me about VxLAN BGP EVPN fabrics. If you have some time, it would be a great help for me if you could tell me 1 or 2 questions that you would ask in such interviews.
TL&DR: He got the job. Congratulations!
An ipSpace.net subscriber sent me this question:
I am on job hunting. I have secured an interview and they will probably ask me about VxLAN BGP EVPN fabrics. If you have some time, it would be a great help for me if you could tell me 1 or 2 questions that you would ask in such interviews.
TL&DR: He got the job. Congratulations!
Disaggregation means a lot of things, but the one thing that it most certainly does not mean is that every little thing in a system necessarily has to be smashed apart and then put back together in a composable ways. …
Enfabrica Converges Extended Memory And I/O Down To One Chip was written by Timothy Prickett Morgan at The Next Platform.