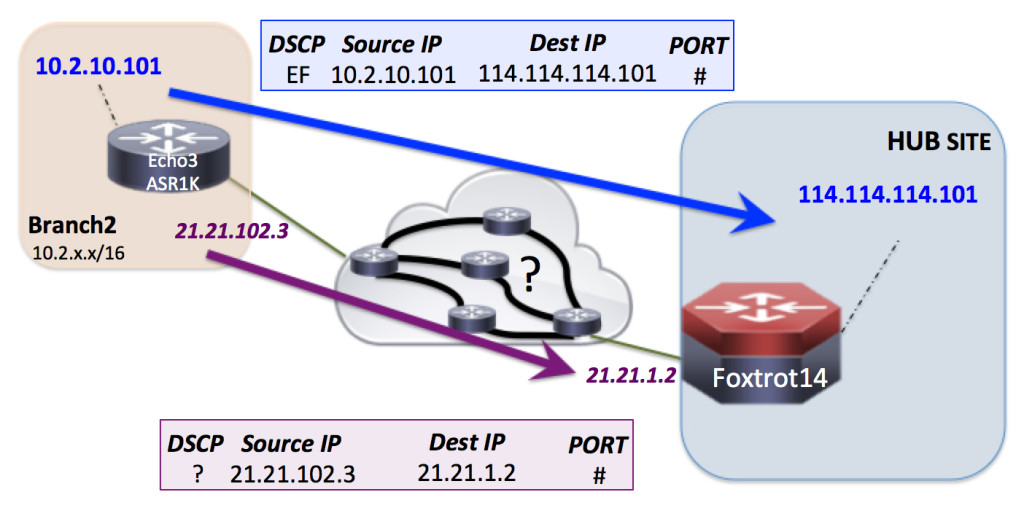
0
In two previous posts we've discussed how to receive 1M UDP packets per second and how to reduce the round trip time. We did the experiments on Linux and the performance was very good considering it's a general purpose operating system.
Unfortunately the speed of vanilla Linux kernel networking is not sufficient for more specialized workloads. For example, here at CloudFlare, we are constantly dealing with large packet floods. Vanilla Linux can do only about 1M pps. This is not enough in our environment, especially since the network cards are capable of handling a much higher throughput. Modern 10Gbps NIC's can usually process at least 10M pps.
 CC BY 2.0 image by Tony Webster
CC BY 2.0 image by Tony Webster
It's apparent that the only way to squeeze more packets from our hardware is by working around the Linux kernel networking stack. This is called a "kernel bypass" and in this article we'll dig into various ways of achieving it.
The kernel is insufficient
Let's prepare a small experiment to convince you that working around Linux is indeed necessary. Let's see how many packets can be handled by the kernel under perfect conditions. Passing packets to userspace is costly, so instead let's try to drop Continue reading
 A pre-VMworld tradition, v0dgeball is a charity dodgeball tournament that drew 16 teams eager to bean each other in the ankles.
A pre-VMworld tradition, v0dgeball is a charity dodgeball tournament that drew 16 teams eager to bean each other in the ankles.
 CC BY 2.0
CC BY 2.0  Giddy up, y'all! AWS is looking to buy, while Gigamon and RSA team up. Find out more in this week's roundup.
Giddy up, y'all! AWS is looking to buy, while Gigamon and RSA team up. Find out more in this week's roundup.