The Chief Zero Trust Officer: a new role for a new era of cybersecurity

Setting the stage for Zero Trust

Over the last few years the topic of cyber security has moved from the IT department to the board room. The current climate of geopolitical and economic uncertainty has made the threat of cyber attacks all the more pressing, with businesses of all sizes and across all industries feeling the impact. From the potential for a crippling ransomware attack to a data breach that could compromise sensitive consumer information, the risks are real and potentially catastrophic. Organizations are recognizing the need for better resilience and preparation regarding cybersecurity. It is not enough to simply react to attacks as they happen; companies must proactively prepare for the inevitable in their approach to cybersecurity.
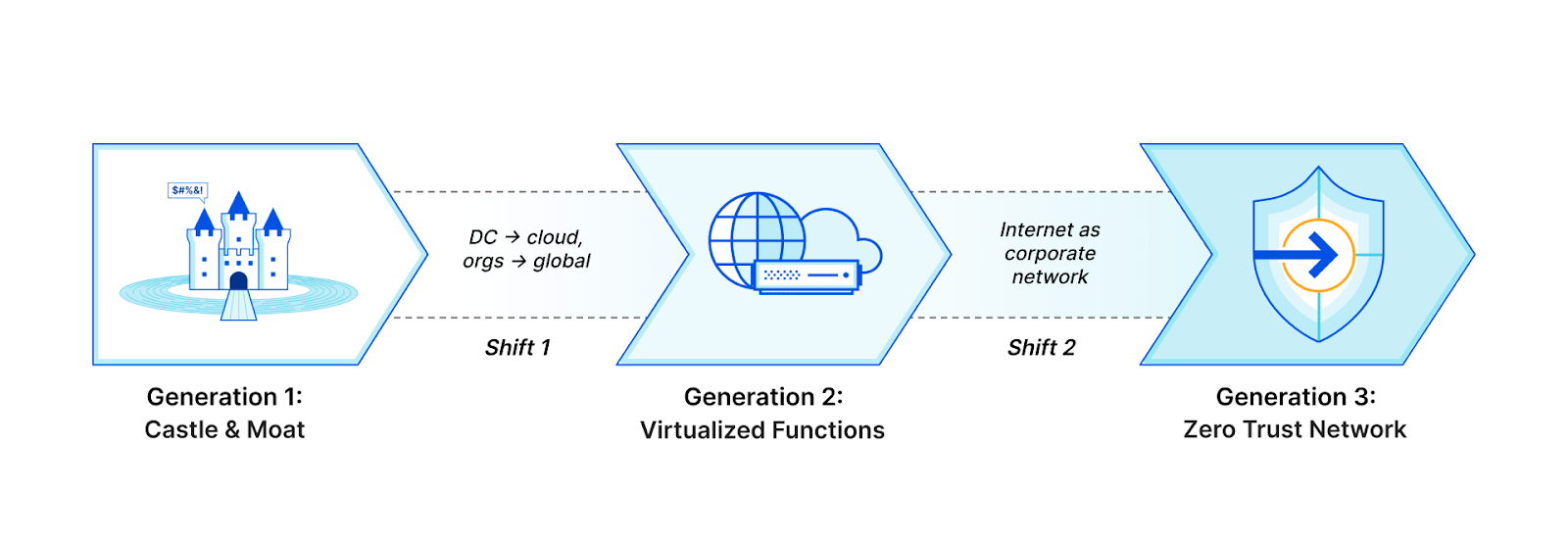
The security approach that has gained the most traction in recent years is the concept of Zero Trust. The basic principle behind Zero Trust is simple: don't trust anything; verify everything. The impetus for a modern Zero Trust architecture is that traditional perimeter-based (castle-and-moat) security models are no longer sufficient in today's digitally distributed landscape. Organizations must adopt a holistic approach to security based on verifying the identity and trustworthiness of all users, devices, and systems that access their networks and data.



 Replacing 'leaving do' with 'send forth'
Replacing 'leaving do' with 'send forth'

 The end of multi-choice answers might be in sight
The end of multi-choice answers might be in sight
 s inability to access or use its software during a ransomware attack was outside the scope of its “businessowners” policy.
s inability to access or use its software during a ransomware attack was outside the scope of its “businessowners” policy.