0
Proxying around 5% of the Internet’s requests gives us an interesting vantage point from which to observe malicious behavior. It also make us a target. Aside from the many, varied denial of service attacks that break against our defenses we also see huge number of phishing campaigns. In this blog post I will dissect a recent phishing attack that we detected and neutralized with the help of our friends at Bluehost.
An attack that is particularly interesting as it appears to be using a brand new WordPress 0day.
A Day Out Phishing
The first sign we typically see that shows a new phishing campaign is underway are the phishing emails themselves. There's general a constant background noise of a few of these emails targeting individual customers every day. However when a larger campaign starts up, typically that trickle turns into a flood of very similar messages.
Messages like this one:
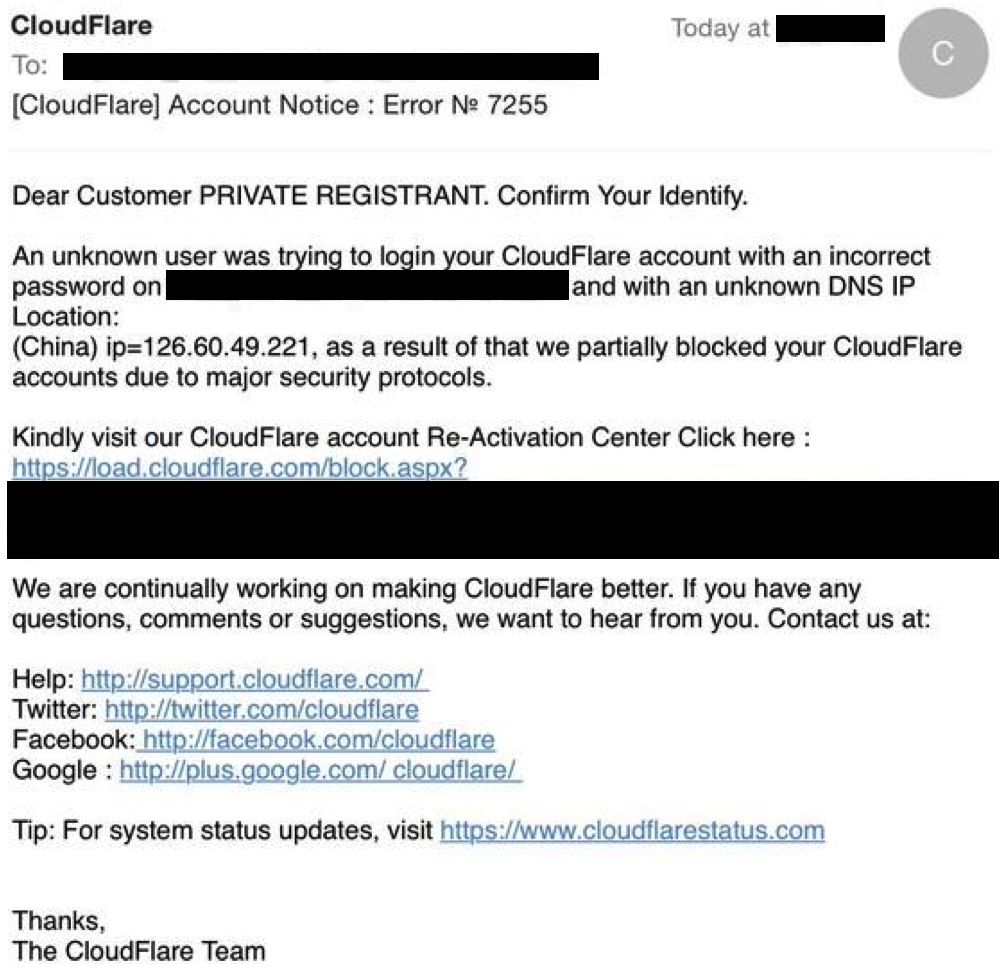 Note — We will never send you an email like this. If you see one, its fake and should be reported to our abuse team by forwarding it to [email protected].
Note — We will never send you an email like this. If you see one, its fake and should be reported to our abuse team by forwarding it to [email protected].
In terms of the phishing campaign timeline, these emails aren’t the first event. Much like a spider looking to Continue reading
 Note — We will never send you an email like this. If you see one, its fake and should be reported to our abuse team by forwarding it to
Note — We will never send you an email like this. If you see one, its fake and should be reported to our abuse team by forwarding it to  Acquire or be acquired? That's not how CEO Rami Rahim sees it.
Acquire or be acquired? That's not how CEO Rami Rahim sees it. Cloud software company Avni has shipped its first product.
Cloud software company Avni has shipped its first product.