Infosys invests in cloud, health monitoring market
Indian outsourcer Infosys has made an acquisition in the area of cloud computing and invested in a personal health monitoring company as it tries to move into high value products and services.The transition is, however, taking time and in the financial results the company reported Friday its revenue and profit grew only slightly. The company said it faced pricing pressure in its core outsourcing business, which still largely prices its services around the number of people deployed on a customer’s project.As it expands into other markets, Infosys has agreed to pay US$120 million to buy Kallidus, a cloud-hosted platform for retailers to provide apps and other mobile content. The company also invested $2 million from its Innovation Fund in Airviz, a spinout from Carnegie Mellon University that is focused on personal air quality monitoring.To read this article in full or to leave a comment, please click here
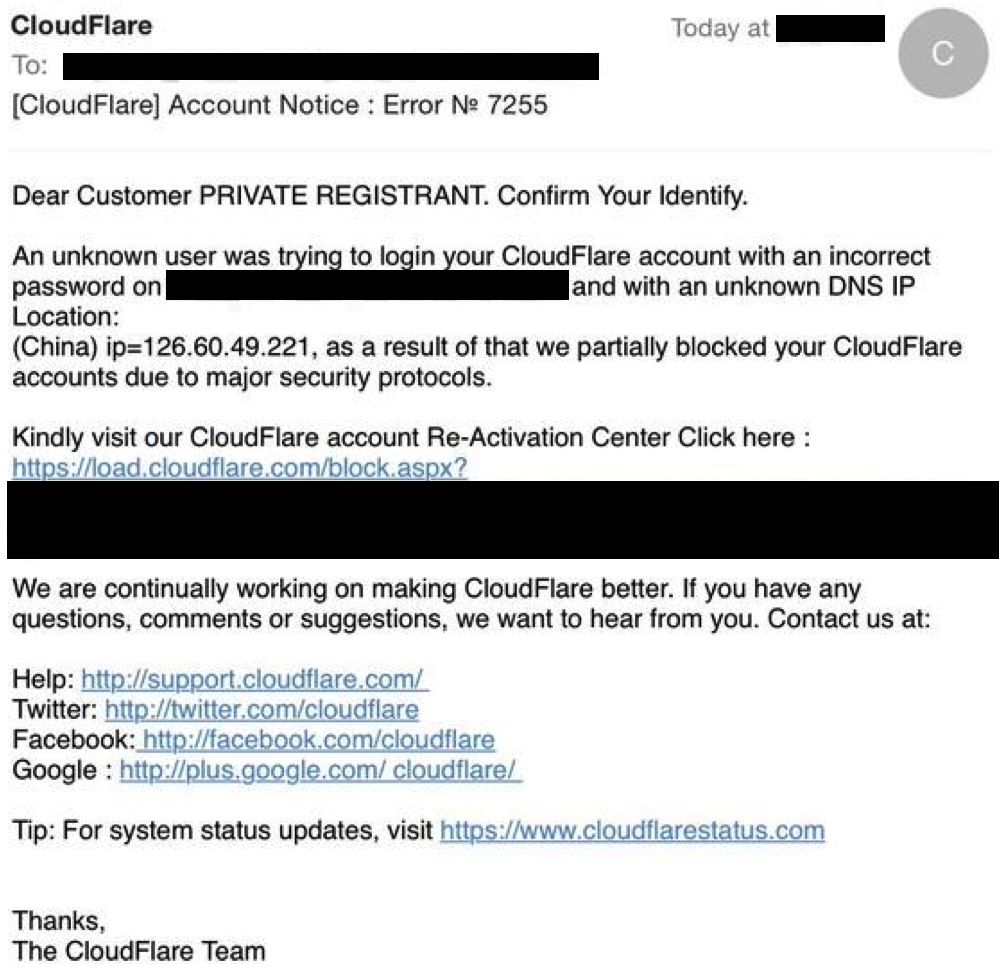 Note — We will never send you an email like this. If you see one, its fake and should be reported to our abuse team by forwarding it to
Note — We will never send you an email like this. If you see one, its fake and should be reported to our abuse team by forwarding it to  Acquire or be acquired? That's not how CEO Rami Rahim sees it.
Acquire or be acquired? That's not how CEO Rami Rahim sees it.