Why the SteelApp sale is a win-win for Brocade and Riverbed
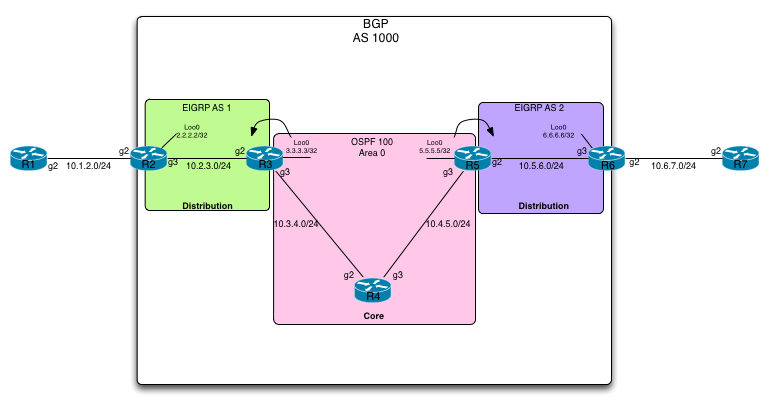
Last week, Brocade announced its intent to purchase the SteelApp product line from Riverbed for an undisclosed amount of cash. SteelApp is a virtual application delivery controller and competes most often with the likes of F5 and Citrix. Formerly known as Stingray, SteelApp came to Riverbed in the acquisition of UK-based Zeus, who pioneered the virtual ADC market. On paper, the acquisition made sense for Riverbed, as Zeus had solutions that optimized the performance of applications with a data center solution and Riverbed was a vendor that optimizes application performance over the wide area network.However, although the business unit had some early success when it was dropped into the Riverbed channel, it never really became a meaningful part of Riverbed's revenue stream. Now, after almost four years, SteelApp will become part of Brocade's business.To read this article in full or to leave a comment, please click here
 itecture (released 2008). The technology is ported to the more “Desktop” oriented CPU’s as well, so there is a good chance your notebook supports it as well. Since the Haswell architecture the nested virtualization works even better as Intel now supports VMCS Shadowing for nested VMs, which creates a data structure in memory per VM (and now supports nested VMs as well, which used to be a software effort).
itecture (released 2008). The technology is ported to the more “Desktop” oriented CPU’s as well, so there is a good chance your notebook supports it as well. Since the Haswell architecture the nested virtualization works even better as Intel now supports VMCS Shadowing for nested VMs, which creates a data structure in memory per VM (and now supports nested VMs as well, which used to be a software effort).