Give us a ping. (Cloudflare) One ping only.


Ping was born in 1983 when the Internet needed a simple, effective way to measure reachability and distance. In short, ping (and subsequent utilities like traceroute and MTR) provides users with a quick way to validate whether one machine can communicate with another. Fast-forward to today and these network utility tools have become ubiquitous. Not only are they now the de facto standard for troubleshooting connectivity and network performance issues, but they also improve our overall quality of life by acting as a common suite of tools almost all Internet users are comfortable employing in their day-to-day roles and responsibilities.
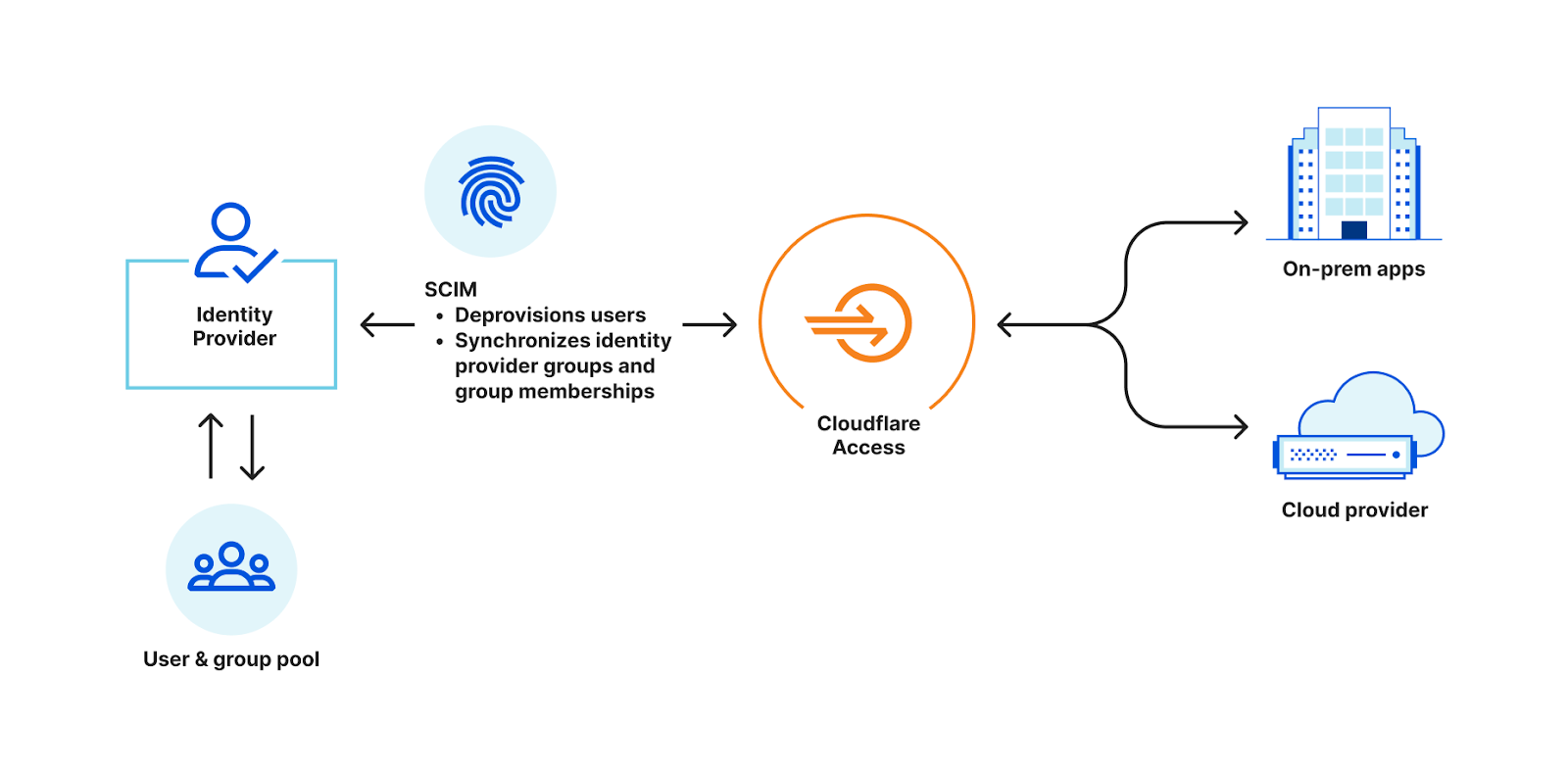
Making network utility tools work as expected is very important to us, especially now as more and more customers are building their private networks on Cloudflare. Over 10,000 teams now run a private network on Cloudflare. Some of these teams are among the world's largest enterprises, some are small crews, and yet others are hobbyists, but they all want to know - can I reach that?
That’s why today we’re excited to incorporate support for these utilities into our already expansive troubleshooting toolkit for Cloudflare Zero Trust. To get started, sign up to receive beta access and start using the Continue reading




 Encrypt everything! Now! We don’t often do well with absolutes like this in the engineering world–we tend to focus on “get it down,” and not to think very much about the side effects or unintended consequences. What are the unintended consequences of encrypting all traffic all the time? Geoff Huston joins Tom Ammon and Russ White to discuss the problems with going dark.
Encrypt everything! Now! We don’t often do well with absolutes like this in the engineering world–we tend to focus on “get it down,” and not to think very much about the side effects or unintended consequences. What are the unintended consequences of encrypting all traffic all the time? Geoff Huston joins Tom Ammon and Russ White to discuss the problems with going dark.