Network Break 404: Episode Not Found
This week the Network Break covers new SASE capabilities from Fortinet, new 800G hardware from Cisco that uses its homegrown ASIC, and an app from RSA for smart phones that can disable authentication if the app detects malicious behavior. Plus we cover new initiatives from the Open Compute Project, disaggregated Wi-Fi, and more tech news.Network Break 404: Episode Not Found
This week the Network Break covers new SASE capabilities from Fortinet, new 800G hardware from Cisco that uses its homegrown ASIC, and an app from RSA for smart phones that can disable authentication if the app detects malicious behavior. Plus we cover new initiatives from the Open Compute Project, disaggregated Wi-Fi, and more tech news.
The post Network Break 404: Episode Not Found appeared first on Packet Pushers.
The Ever-Reddening Revenue Streams Of Big Blue
Speaking in generalities across any aspect of history is always risky, but that is what the job of history is. …
The Ever-Reddening Revenue Streams Of Big Blue was written by Timothy Prickett Morgan at The Next Platform.
On the ‘net: Privacy and Networking
The final three posts in my series on privacy for infrastructure engineers is up over at Packet Pushers. While privacy might not seem like a big deal to infrastructure folks, it really is an issue we should all be considering and addressing—if for no other reason than privacy and security are closely related topics. The primary “thing” you’re trying to secure when you think about networking is data—or rather, various forms of privacy.
Tech Bytes: Using Opengear Every Day–For Disruptions And More (Sponsored)
Today on the Tech Bytes podcast we talk about how to use out-of-band management for daily networking tasks, not just when there’s a problem or crisis. Our sponsor is Opengear and we’re joined by Ramtin Rampour, Solutions Architect, to talk about use cases including zero touch provisioning, configuration, and more.Tech Bytes: Using Opengear Every Day–For Disruptions And More (Sponsored)
Today on the Tech Bytes podcast we talk about how to use out-of-band management for daily networking tasks, not just when there’s a problem or crisis. Our sponsor is Opengear and we’re joined by Ramtin Rampour, Solutions Architect, to talk about use cases including zero touch provisioning, configuration, and more.
The post Tech Bytes: Using Opengear Every Day–For Disruptions And More (Sponsored) appeared first on Packet Pushers.
Best of Fest 2022
At AnsibleFest 2022, the power of automation was on full display. Through sessions, workshops, labs and more, we explored how to transform enterprise and industry through automation. There were a lot of exciting announcements made on both days, and in case you missed it, we are going to dive into what is new!
Ansible + AWS
We are thrilled to also announce a new AWS Marketplace offering, Red Hat Ansible Automation Platform. By offering Ansible Automation Platform as a pre-integrated service that can be quickly deployed from cloud marketplaces, we are meeting our customers where they are, while giving them the flexibility to deliver any application, anywhere, without additional overhead or complexity. Whether you are automating your hybrid cloud or multi-cloud environments, Ansible Automation Platform acts as a single platform. This platform provides consistency, visibility, and control to help you manage these environments at scale. Ansible is the IT automation “glue” for bringing your cloud, network, bare-metal and cloud-native infrastructure together. This provides the functionality to coordinate and manage across hybrid cloud environments in a simple and efficient way. Interested in learning more? Check out the press release.
Automation at the Edge
Ansible Automation Platform provides a Continue reading
Deploy Ceph on K8s Worker Nodes Using ROOK
please visit following Git wiki
https://github.com/kashif-nawaz/Deploy-Ceph-on-K8s-Worker-Node-Using-ROOK
And here’s another one: the Next.js Edge Runtime becomes the fourth full-stack framework supported by Cloudflare Pages


You can now deploy Next.js applications which opt in to the Edge Runtime on Cloudflare Pages. Next.js is the fourth full-stack web framework that the Pages platform officially supports, and it is one of the most popular in the 'Jamstack-y' space.
Cloudflare Pages started its journey as a platform for static websites, but with last year's addition of Pages Functions powered by Cloudflare Workers, the platform has progressed to support an even more diverse range of use cases. Pages Functions allows developers to sprinkle in small pieces of server-side code with its simple file-based routing, or, as we've seen with the adoption from other frameworks (namely SvelteKit, Remix and Qwik), Pages Functions can be used to power your entire full-stack app. The folks behind Remix previously talked about the advantages of adopting open standards, and we've seen this again with Next.js' Edge Runtime.
Next.js' Edge Runtime
Next.js' Edge Runtime is an experimental mode that developers can opt into which results in a different type of application being built. Previously, Next.js applications which relied on server-side rendering (SSR) functionality had to be deployed on a Node.js server. Running a Node.js Continue reading
How Do You Meet The Bandwidth Demands Of HPC And AI System Architectures?
Sponsored Post: Analyst firm Gartner believes AI will remain one of the top workloads driving infrastructure decisions through to 2023 as more organizations push pilot projects into the production stage. …
How Do You Meet The Bandwidth Demands Of HPC And AI System Architectures? was written by Timothy Prickett Morgan at The Next Platform.
The Cloud is Not a Railroad – An Argument Against the Vertical Separation of Cloud Providers

There's a move to regulate cloud providers by vertically separating the services they offer.
Like railroads of yore, who were not allowed to provide freight services on top of their base services, cloud providers would not be allowed to provide services on top of their base platform services.
Vertical separation would be new to the cloud industry. Is it a good idea? Would it actually solve any problems? My answers are no and no, but probably not for the reasons you think. Let's dive in.
Here are a few useful resources for exploring this argument:
- Maintaining monopolies with the cloud by Cory Doctorow. https://pluralistic.net/2022/09/28/other-peoples-computers.
- A group advocating for fair licensing. https://www.fairsoftwarelicensing.com/our-principles.
- Cloud Infrastructure Services -- An analysis of potentially anti-competitive practices by Professor Frédéric Jenny. https://www.fairsoftwarestudy.com/.
Now Cory is about 100x times smarter than I am, but this analogy is wrong:
That's why the trustbusters were so big on "structural separation": the principle that a business can own a platform or use the platform, but not both.
So this remedy is also wrong:
Rather than trying to construct rules that kept the referee honest even when they played on one of the teams, they Continue reading
Use VRFs for VXLAN-Enabled VLANs
I started one of my VXLAN tests with a simple setup – two switches connecting two hosts over a VXLAN-enabled (gray tunnel) red VLAN. The switches are connected with a single blue link.
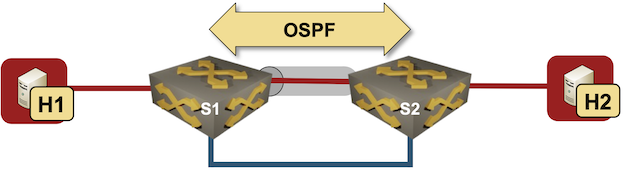
Test lab
I configured VLANs and VXLANs, and started OSPF on S1 and S2 to get connectivity between their loopback interfaces. Here’s the configuration of one of the Arista cEOS switches:
Use VRFs for VXLAN-Enabled VLANs
I started one of my VXLAN tests with a simple setup – two switches connecting two hosts over a VXLAN-enabled (gray tunnel) red VLAN. The switches are connected with a single blue link.

Test lab
I configured VLANs and VXLANs, and started OSPF on S1 and S2 to get connectivity between their loopback interfaces. Here’s the configuration of one of the Arista cEOS switches:
The RISC Deprogrammer
I should write up a larger technical document on this, but in the meanwhile is this short (-ish) blogpost. Everything you know about RISC is wrong. It's some weird nerd cult. Techies frequently mention RISC in conversation, with other techies nodding their head in agreement, but it's all wrong. Somehow everyone has been mind controlled to believe in wrong concepts.
An example is this recent blogpost which starts out saying that "RISC is a set of design principles". No, it wasn't. Let's start from this sort of viewpoint to discuss this odd cult.
What is RISC?
Because of the march of Moore's Law, every year, more and more parts of a computer could be included onto a single chip. When chip densities reached the point where we could almost fit an entire computer on a chip, designers made tradeoffs, discarding unimportant stuff to make the fit happen. They made tradeoffs, deciding what needed to be included, what needed to change, and what needed to be discarded.
RISC is a set of creative tradeoffs, meaningful at the time (early 1980s), but which were meaningless by the late 1990s.
The interesting parts of CPU evolution are the three decades from 1964 with Continue reading
Controversial Reads 102222
This month, LinkedIn researchers revealed in Science that the company spent five years quietly researching more than 20 million users. By tweaking the professional networking platform’s algorithm, researchers were trying to determine through A/B testing whether users end up Continue reading