Linear Regression Rough Notes
Introduction

When it comes to stats, one of the first topics we learn is linear regression. But many people don’t realize how deep the linear regression topic is. Below are my partial notes on Linear Regression for anyone who may find this helpful.
Linear Model
A basic statistical model with single explanatory variable has equation describing the relation between x and the mean
$\mu$ of the conditional distribution of Y at each value of x.
$ E(Y_{i}) = \beta_{0} + \beta_{1}x_{i} $
Alternative formulation for the model expresses $Y_{i}$
$ Y_{i} = \beta_{0} + \beta_{1}x_{i} + \epsilon_{i} $
where $\epsilon_{i}$ is the deviation of $Y_{i}$ from $E(Y_{i}) = \beta_{0} + \beta_{1}x_{i} + \epsilon_{i}$ is called
the error term, since it represents the error that results from using the conditional expectation of Y at $x_{i}$ to
predict the individual observation.
Least Squares Method
For the linear model $E(Y_{i}) = \beta_{0} + \beta_{1}x_{i}$, with a sample of n observations the least squares method determines the value of $\hat{\beta_{0}}$ and $\hat{\beta_{1}}$ that minimize the sum of squared residuals.
$ \sum_{i=1}^{n}(y_{i}-\hat{\mu_{i}})^2 = \sum_{i=1}^{n}[y_{i}-(\hat{\beta_{0}} + \hat{\beta_{1}}x_{i})]^2 = \sum_{i=1}^{n}e^{2}_{i} $
As a function of model parameters $(\beta_{0} , \beta_{1})$, the expression is quadratic in $\beta_{0},\beta_{1}$
Linear Regression Notes
Introduction

When it comes to stats, one of the first topics we learn is linear regression. But most people don’t realize how deep the linear regression topic is, and observing blind applications in day-to-day life makes me cringe. This post is not about virtue-signaling(as I know some areas I haven’t explored myself), but to share my notes which may be helpful to others.
Linear Model
A basic stastical model with single explanatory variable has equation describing the relation between x and the mean
$\mu$ of the conditional distribution of Y at each value of x.
$ E(Y_{i}) = \beta_{0} + \beta_{1}x_{i} $
Alternative formulation for the model expresses $Y_{i}$
$ Y_{i} = \beta_{0} + \beta_{1}x_{i} + \epsilon_{i} $
where $\epsilon_{i}$ is the deviation of $Y_{i}$ from $E(Y_{i}) = \beta_{0} + \beta_{1}x_{i} + \epsilon_{i}$ is called
the error term, since it represents the error that results from using the conditional expectation of Y at $x_{i}$ to
predict the individual observation.
Least Squares Method
For the linear model $E(Y_{i}) = \beta_{0} + \beta_{1}x_{i}$, with a sample of n observations the least squares method determines the value of $\hat{\beta_{0}}$ and $\hat{\beta_{1}}$ that minimize the sum of squared residuals.
$ \sum_{i=1}^{n}(y_{i}-\hat{\mu_{i}})^2 = \sum_{i=1}^{n}[y_{i}-(\hat{\beta_{0}} + Continue reading
VPP Lab – Setup
Introduction
In a previous post (VPP Linux CP - Virtual Machine Playground), I wrote a bit about building a QEMU image so that folks can play with the Vector Packet Processor and the Linux Control Plane code. Judging by our access logs, this image has definitely been downloaded a bunch, and I myself use it regularly when I want to tinker a little bit, without wanting to impact the production routers at AS8298.
The topology of my tests has become a bit more complicated over time, and often just one router would not be
enough. Yet, repeatability is quite important, and I found myself constantly reinstalling / recheckpointing
the vpp-proto virtual machine I was using. I got my hands on some LAB hardware, so it’s time for an upgrade!
IPng Networks LAB - Physical
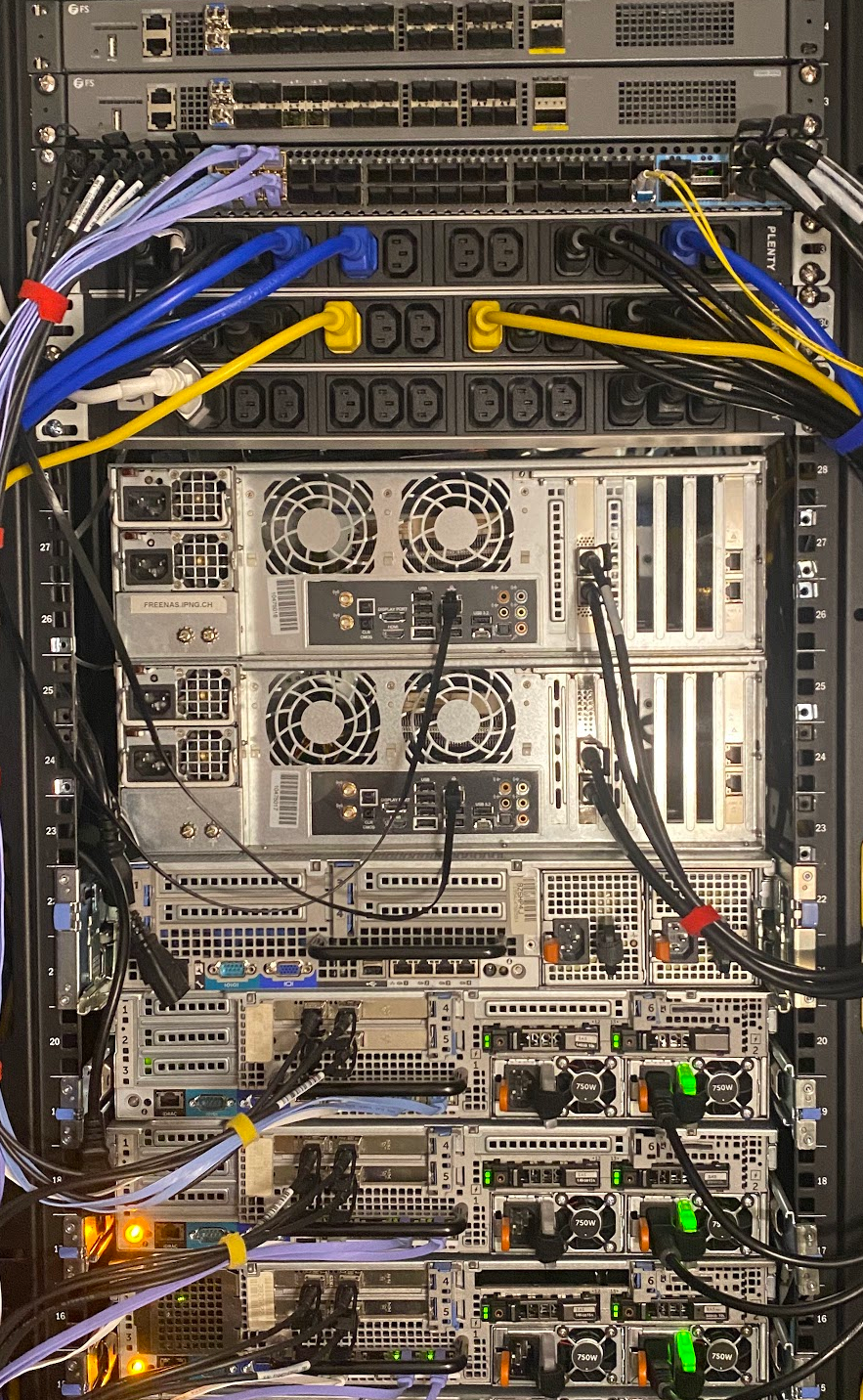
First, I specc’d out a few machines that will serve as hypervisors. From top to bottom in the picture here, two FS.com S5680-20SQ switches – I reviewed these earlier [ref], and I really like these, as they come with 20x10G, 4x25G and 2x40G ports, an OOB management port and serial to configure them. Under it, is its larger brother, with 48x10G Continue reading
Heavy Networking 651: How Juniper Networks’ SMO Enables Network Slicing (Sponsored)
As carriers and service providers look to embrace disaggregated infrastructure and software, and drive new business through technologies such as network slicing, it’s critical to have management and orchestration capabilities to coordinate hardware and software resources in the RAN, the transport layer, and the network core. On today's sponsored Heavy Networking, sponsored by Juniper, we dive into Juniper's Service Management and Orchestration (SMO) platform, which is designed to provision, manage and monetize custom network services on demand.Heavy Networking 651: How Juniper Networks’ SMO Enables Network Slicing (Sponsored)
As carriers and service providers look to embrace disaggregated infrastructure and software, and drive new business through technologies such as network slicing, it’s critical to have management and orchestration capabilities to coordinate hardware and software resources in the RAN, the transport layer, and the network core. On today's sponsored Heavy Networking, sponsored by Juniper, we dive into Juniper's Service Management and Orchestration (SMO) platform, which is designed to provision, manage and monetize custom network services on demand.
The post Heavy Networking 651: How Juniper Networks’ SMO Enables Network Slicing (Sponsored) appeared first on Packet Pushers.
Hedgehog – The Network OS Distro?

You’ve probably seen by now that there’s a new entrant into the market for network operating systems. Hedgehog came out of stealth mode this week to fanfare from the networking community. If you read through the website you might question why I labeled them as a network operating system. While they aren’t technically the OS I think it’s more important to look at them as an OS distribution.
Cacophony of Choice
Hedgehog starts from a very simple premise. Cloud networking is where we’re all headed. Whether or not you’re running entirely on-premises, fully in the public cloud, or in some kind of super-multi-hybrid cloud offering you’re all chasing the same thing. You want a stable system that acts as a force multiplier for your operations teams to reduce deployment times for users to get their builds done. It’s been said before but the idea of cloud is to get IT out of the way of the business.
Streamlining processes means automating a lot of the things that were formerly done by people. That means building repeatable and consistent tools to make that happen. If anyone has ever worked on AWS or Google Cloud you have lots of access to that Continue reading
Weekend Reads 101422
The City of Chicago asked some researchers at the University of Chicago for help to identify the neighborhoods and the number of households that are not connected to broadband.
https://circleid.com/posts/20221006-solving-the-.us-registrant-data-directory-services-rdds-conundrum
Recently ten Democratic Members of Congress wrote a letter to Alan Davidson, head of the NTIA, requesting that the “NTIA immediately cease the public disclosure of personal information about users of .US” country code top-level domain (ccTLD).
https://circleid.com/posts/20221005-four-steps-to-an-effective-brand-protection-program
This makes a comprehensive, holistic brand protection program crucial for any brand owner, including monitoring to identify potentially damaging third-party content, and using enforcement strategies to take down infringing material
A fundamental mechanism that secures the internet has been broken
National research center for Cybersecurity ATHENE says it has found a way to easily bypass this security mechanism, and in a way that means affected network operators are unable to notice.
https://www.darkreading.com/edge-articles/the-insecurities-of-cybersecurity-success
While he uses content creation as a lens for talking about mental health and the pressures he faces, he also draws parallels between making videos for the community and making tools for the community
https://circleid.com/posts/20221004-developing-models-for-the-prediction-of-domain-name-renewal-rates
One of the key issues for the Domain industry is how to accurately predict year-on-year Continue reading
Null Zero Long Form Video Content 🎬
In this is post
🎬 EVPN-VXLAN Explainer - now on youtube.
📔 An update on what I've been up to, lots of EVPN.
🦀 MY other project - learning Rust
EVPN-VXLAN Explainer 1
My recent EVPN Explainer posts were essentially preparation for a video series, covering roughly the same content.
With the large amount of detail required, and as I refined my messaging, I felt that a blog was a better medium to use at first. Videos are much harder to edit and correct any mistakes. Thus I wanted to try out my content in writing, then move on to creating the videos.
After a couple of weeks preparing and recording, along with my main job, I'm happy to say that I've released the first video, and here it is:
This video is a gentle introduction to EVPN, focusing on the high-level operation and configuration, rather than going to deep. With the basics out of the way, I'll be going into the details, much like my blog posts, in later videos.
A Brief Update AKA What I've been up to
As the long, hot summer of 2022 draws to a close, I've put away the flip-flops and dived straight back Continue reading
Getting Ahead Of The Game: Inspur’s Machine For Digital Twins And Immersive Experiences
Commissioned: Not everybody wants to be Iron Man. But there isn’t an artist or engineer around that doesn’t envy the 3D, immersive design experience that Tony Stark used to invent new equipment and analyze his existing gadgets in the Avenger movies. …
Getting Ahead Of The Game: Inspur’s Machine For Digital Twins And Immersive Experiences was written by Timothy Prickett Morgan at The Next Platform.
Video: Bridging Beyond Spanning Tree
In this week’s update of the Data Center Infrastructure for Networking Engineers webinar, we talked about VLANs, VRFs, and modern data center fabrics.
Those videos are available with Standard or Expert ipSpace.net Subscription; if you’re still sitting on the fence, you might want to watch the how networks really work version of the same topic that’s available with Free Subscription – it describes the principles-of-operation of bridging fabrics that don’t use STP (TRILL, SPBM, VXLAN, EVPN)
Video: Bridging Beyond Spanning Tree
In this week’s update of the Data Center Infrastructure for Networking Engineers webinar we talked about VLANs, VRFs, and modern data center fabrics.
Those videos are available with Standard or Expert ipSpace.net Subscription; if you’re still sitting on the fence, you might want to watch the how networks really work version of the same topic that’s available with Free Subscription – it describes the principles-of-operation of bridging fabrics that don’t use STP (TRILL, SPBM, VXLAN, EVPN)
TSMC: The Leading Indicator For An Entire Industry
Taiwan Semiconductor Manufacturing Co is the world’s largest and most advanced producer of semiconductors, and is therefore a “bellwether” for the semiconductor industry and, in turn therefore, a leading indicator of the entire IT sector that depends so heavily on semiconductors as its key driver. …
TSMC: The Leading Indicator For An Entire Industry was written by Timothy Prickett Morgan at The Next Platform.