Tenstorrent Eyes Datacenter Deals With Another Star Hire From AMD
If Jim Keller makes a move, it’s best to watch closely. …
Tenstorrent Eyes Datacenter Deals With Another Star Hire From AMD was written by Dylan Martin at The Next Platform.
If Jim Keller makes a move, it’s best to watch closely. …
Tenstorrent Eyes Datacenter Deals With Another Star Hire From AMD was written by Dylan Martin at The Next Platform.
It is the nature of the many businesses that Hewlett Packard Enterprise remains in, after spinning off printers, PCs, services, and software, that it still has many ups and downs and there is always one business that can pull down the others. …
The Long Term Profitability Of HPE Depends On GreenLake was written by Timothy Prickett Morgan at The Next Platform.
My video on BGP convergence elicited a lot of . . . feedback, mainly concerning the difference between convergence in a data center fabric and convergence in the DFZ. Let’s begin here—BGP hunt and the impact of the MRAI are very real in the DFZ. Withdrawing a route can take several minutes.
What about the much more controlled environment of a data center fabric?
Several folks pointed out that the MRAI is often set to 0 in DC fabrics (and many implementations by default). Further, almost all implementations will use an MRAI of 0 for the first received update, holding the second and subsequent advertisements by the MRAI. Several folks also pointed out that all the paths through a DC fabric are the same length, so the second part of the equation is also very small.
These are good points—how do they impact BGP convergence? Let’s use the network below, a small slice of a five-stage butterfly fabric, to think it through. Assume every router is in a different AS, so all the peering sessions are eBGP.

Start with A losing its connection to 101::/64—
What goes into a perfect protein shake? If you’re looking for an answer to that question, you’ll find it in Protein and Greens by Vega. This convenient powder provides a perfect blend of protein, greens, and other nutrients to help support optimal health.
Protein and Greens by Vega is a great way to get your daily greens and protein. It’s a convenient powder that can be added to water or your favorite beverage. It’s also a good source of fiber and antioxidants.
If you’re looking for a convenient way to get your daily greens and protein, Protein and Greens by Vega is a perfect choice. It’s a convenient powder that can be added to water or your favorite beverage. It’s also a good source of fiber and antioxidants.
This Vega Blueberry Vanilla Smoothie recipe is the perfect way to start your day! It’s packed with healthy ingredients like Vega Protein and Greens, almond milk, banana, and blueberries. Plus, it’s super easy to make – just blend and go!
– 1 scoop Protein and Greens by Vega
– 1 cup unsweetened almond milk
– 1/2 banana
– 1 cup frozen blueberries
– 1 teaspoon vanilla Continue reading
By now, you’ve probably heard about why you should automate network management. Not only does automation save time and effort, but it also reduces risk. As Gartner notes, for instance, organizations that automate about 70 percent of their network change management operations will see a 50 percent reduction in outages. They’ll also cut in half the time it takes to roll out new services.
The bigger question many teams face surrounding network automation, however, is how to automate. With so many tools on the market that promise to help automate networking and security, which solution is the best fit for your needs? What should you look for from an automation lens when considering a networking platform?
To provide clarity on those questions, we’ve put together a list of the reasons why customers choose VMware NSX in order to deploy applications at scale with greater speed, efficiency, and security. VMware NSX, the platform for network virtualization, provides instant and programmatic provisioning for fast, highly available, and secure infrastructure. The automation capabilities of NSX listed below maximize time savings and minimize risk when managing distributed, multi-cloud environments. Continue reading

Red Hat Ansible Automation Platform 2.2 introduces a technical preview of automation services catalog.
Automation services catalog was first developed in the cloud at console.redhat.com, with capabilities for fast, agile development and feature release. Over time, Red Hat continually adapted features to meet customer requirements and incorporate their feedback. As customers became more familiar with the benefits, they’ve since requested the ability to access these catalog components within their firewalled infrastructure with direct access to the Ansible clusters and their corporate identity services. We continue to listen and are providing a private version of automation services catalog, installed by the platform installer alongside automation controller and private automation hub.
As far as catalogs go, there is a fairly standard pattern to follow. Here is the first glimpse of the user interface.
This image shows what are known as “products”. Products reside within “portfolios,” which allow the administrator to group products into sharable, access controlled folders. Products are simply references to a job template or workflow.
What I really like about having this new level of abstraction is that I can reference the same job template in a product multiple times. Continue reading
Last week I described how easy it is to use access VLANs in netlab. Next step: VLAN trunks.
We’ll add two Linux hosts to the lab topology used in the previous blog post, resulting in two switches, two Linux hosts in red VLAN and two Linux hosts in blue VLAN.
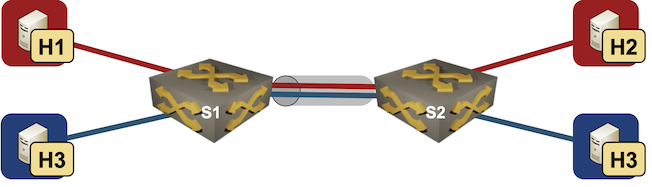
Lab topology
Last week I described how easy it is to use access VLANs in netsim-tools. Next step: VLAN trunks.
We’ll add two Linux hosts to the lab topology used in the previous blog post, resulting in two switches, two Linux hosts in red VLAN and two Linux hosts in blue VLAN.
Hello my friend,
Typically on this date, June the 5th we celebrate the birthday of our company, Karneliuk.com. It started with a blog back in 2016 and since then we are constantly creating, what we believe is, interesting and useful educational content in the area of network technologies and network automation. We thank you a lot for being with us all this time!
Technically, we started blog earlier than June the 5th, but on that date we published our first blogpost about interconnecting Cisco IOS XR and Nokia SR OS VMs, which defined the course of the blog and the direction for the company – multivendorness. We breath multivendor network technologies every day in heterogeneous networks, which our team support for our companies and customers daily. And we build multivendor network automation to unleash the true potential of networks and IT systems being an enabler for applications and user services, rather than an obstacle draining time and money of organizations.
So, what have we done in the past twelve months? Let’s take a look.
One of the interesting experiences we’ve obtained in the software development was the development of Prometheus exporter to report trace Continue reading
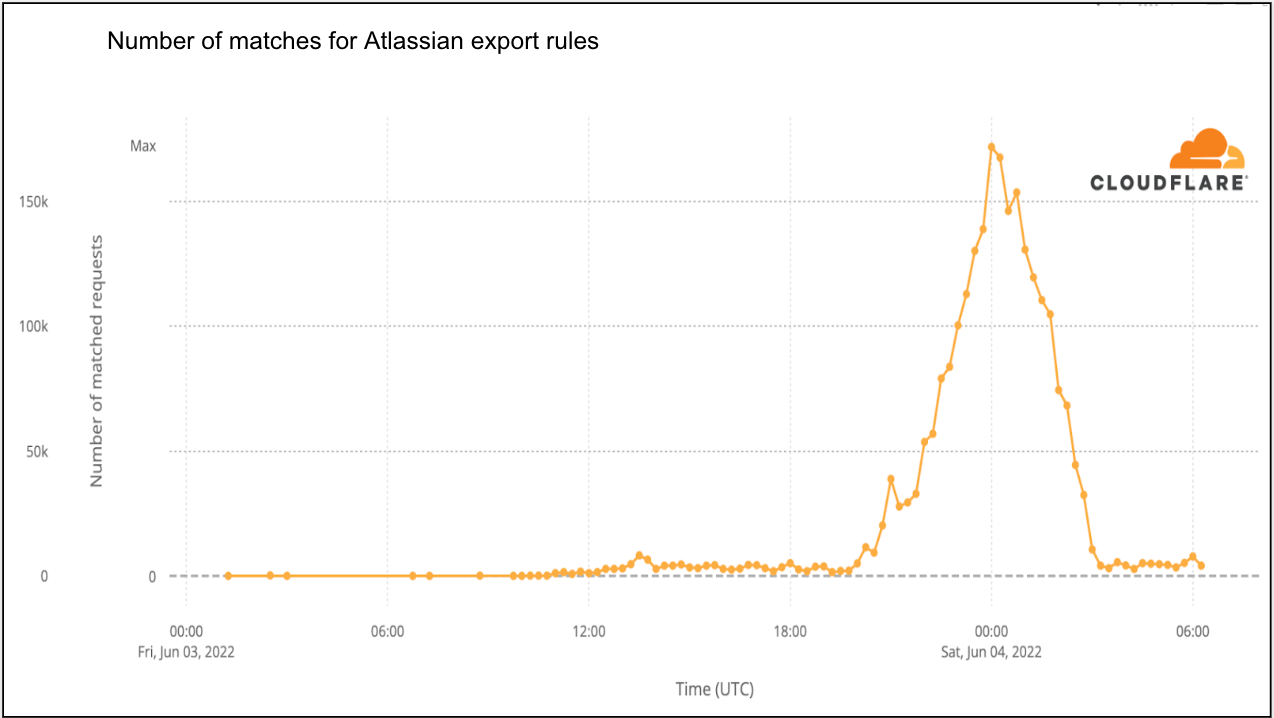
On 2022-06-02 at 20:00 UTC Atlassian released a Security Advisory relating to a remote code execution (RCE) vulnerability affecting Confluence Server and Confluence Data Center products. This post covers our current analysis of this vulnerability.
When we learned about the vulnerability, Cloudflare’s internal teams immediately engaged to ensure all our customers and our own infrastructure were protected:
According to Volexity, the vulnerability results in full unauthenticated RCE, allowing an attacker to fully take over the target application.
Active exploits of this vulnerability leverage command injections using specially crafted strings to load a malicious class file in memory, allowing attackers to subsequently plant a webshell on the target machine that they can interact with.
Once the vulnerability is exploited, attackers can implant additional malicious code such as Behinder; a custom webshell called noop.jsp, which replaces the legitimate noop.jsp file located at Confluence root>/confluence/noop.jsp; and another open source webshell called Continue reading
Following up on the last post, we will explore IS-IS Area Proxy in this post.
The main goal of the IS-IS Area proxy is to provide abstraction by hiding the topology. Looking at our toy topology, we see that we have fabrics connected, and
the whole network is a single flat level-2 flooding domain. The edge nodes are connected at the ends, transiting
multiple fabrics, and view all the nodes in the topology.
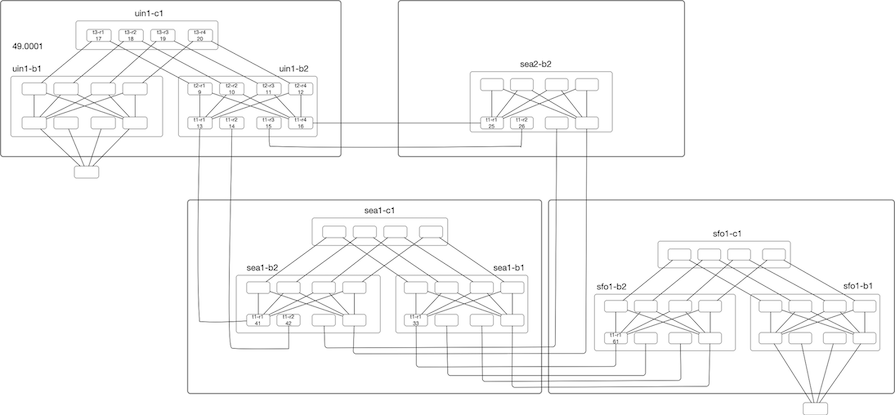
Now assume that we are using a router with a radix of 32x100G and want to deploy three-level Fat-Tree(32,3). For a single fabric, we will have 1280 nodes, 512 leaf Nodes, providing a bandwidth of 819T. If we deploy ten instances of this fabric, we are looking at a topology size greater than >12k Nodes. This is a lot for any IGP to handle. This inflation of Nodes (and links) is coming from deploying this sort of dense topology to provide more bandwidth and directly impacts IGP scaling in terms of Flooding, LSDB size, SPF runtimes, and frequency of SPF run.
Referring back to our toy topology, if we look from the edge node’s perspective, they use these fabrics as transit, and if we can Continue reading
Information Security was one of the fields that Cisco systems used to, and still heavily participating.
Now a days not just information security, but cyber security as well, is a field that Cisco is going in and training many
of their engineers to profession.
The main difference summarizes the concept of both the domains, that is for information security, it is mainly
About securing the network components and assets from unauthorized access starting from physical access
Towards the control access, and by that it means accessing the nodes controlling the network, and affecting it.
Cyber security on the other hand is about protecting the same components from attacks, inside and outside attacks.
The attacks aim is usually either stealing sensitive data, or sabotage network components, or sometimes “both”.
Information Security wise, or IT Security wise, Cisco have been there for years, and they’ve been famous for their IT Security programs including the old obsolete CCNA Security, and the CCNP/CCIE Security programs that are still valid and refreshing till now a day.
Cyber Security wise, Cisco have evolved and developed their programs to present the CyberOps programs that includes the:
In today's Heavy Networking podcast, sponsored by NVIDIA, we explore DOCA on Bluefield DPUs. DOCA is a runtime operating system on the DPU including tools for provisioning, deploying, and orchestrating containerized services. It's also an SDK to supports a range of operating systems and distributions and includes drivers, libraries, and tools. Our guests are Justin Betz and Wes Kennedy, both Technical Marketing Engineers with NVIDIA.
The post Heavy Networking 633: Building DPU Apps With NVIDIA DOCA (Sponsored) appeared first on Packet Pushers.
Just ahead of the revelations about the feeds and speeds of the “Frontier” supercomputer at Oak Ridge National Laboratory concurrent with the International Supercomputing conference in Hamburg, Germany and the concurrent publishing of the summer Top500 rankings of supercomputers, we had a chat with Jeff Nichols, who has steered the creation of successive generations of supercomputers at Oak Ridge. …
The Final Frontier: Talking Exascale With Oak Ridge’s Jeff Nichols was written by Timothy Prickett Morgan at The Next Platform.
This edition of weekend reads begins with a few straight security stories of interest. I knew key loggers existed in the wild, but the logging of keystrokes before a web form is submitted is apparently a lot more common than I realized—
Illustrating that security is often a game of “whack-a-mole,” web skimmers are obfuscating their operation—
Identity is fraught with problems even in the real world; just as people used to carry “letters of introduction” with them when they moved to a new area or started a new job, identity is often a matter of transitive trust. How to replicate transitive trust in the digital world is still a problem, but it’s also the foundation of decentralized systems—
The central thesis of the decentralized future is that I should be Continue reading
There is no denying that GPUs have incredible potential to accelerate workloads of all kinds, but developing applications that can scale across two, four, or even more GPUs continues to be a prohibitively expensive proposition. …
Fractional GPUs Empower New Wave Of Accelerated Software Development was written by Tobias Mann at The Next Platform.

A Candlestick Phone (image courtesy of WIkipedia)
This week on the Gestalt IT Rundown, I talked about the plan by Let’s Encrypt to reuse some reserved IP address space. I’ve talked about this before and I said it was a bad idea then for a lot of reasons, mostly related to the fact that modern operating systems are coded not to allow 240/4 as a valid address space, for example. Yes, I realize that when the address space was codified back in the early days of the Internet that decisions were made to organize things and we “lost” a lot of addresses for experimental reasons. However, this is not the only time this has happened. Nor is it the largest example. For that, we need to talk about the device that you’re very likely reading this post on right now: your phone.
We’re going to be referring to the North American Numbering Plan (NANP) in this post, so my non-US readers are going to want to click that link to understand how phone numbering works in the US. The NANP was devised back in the 1940s by AT&T as a way to assign numbers to the Continue reading