0
Resilient application architectures have evolved quite significantly over the years. It is increasingly more common for Enterprises to deploy multiple data centers to support flexible workload placement and redundancy to achieve application and network high availability.
Here, we discuss key reasons to deploy multiple data centers and how NSX Federation and the recently introduced traceflow support simplify associated infrastructure strategy and implementation.
Workload Placement and Mobility
Applications and the associated infrastructure (compute, storage, networking, and security) are deployed in multiple locations to support workload mobility between these locations for use cases such as Data Center migration and Disaster Recovery testing.

Figure: Multi-Cloud Mobility
Data Center Expansion
In this scenario, IT runs out of capacity at a location (rack, building, site) and wants additional capacity at a different location for hosting new applications. Capacity can be of different types such as compute (servers), and/or storage, and/or network (bandwidth).
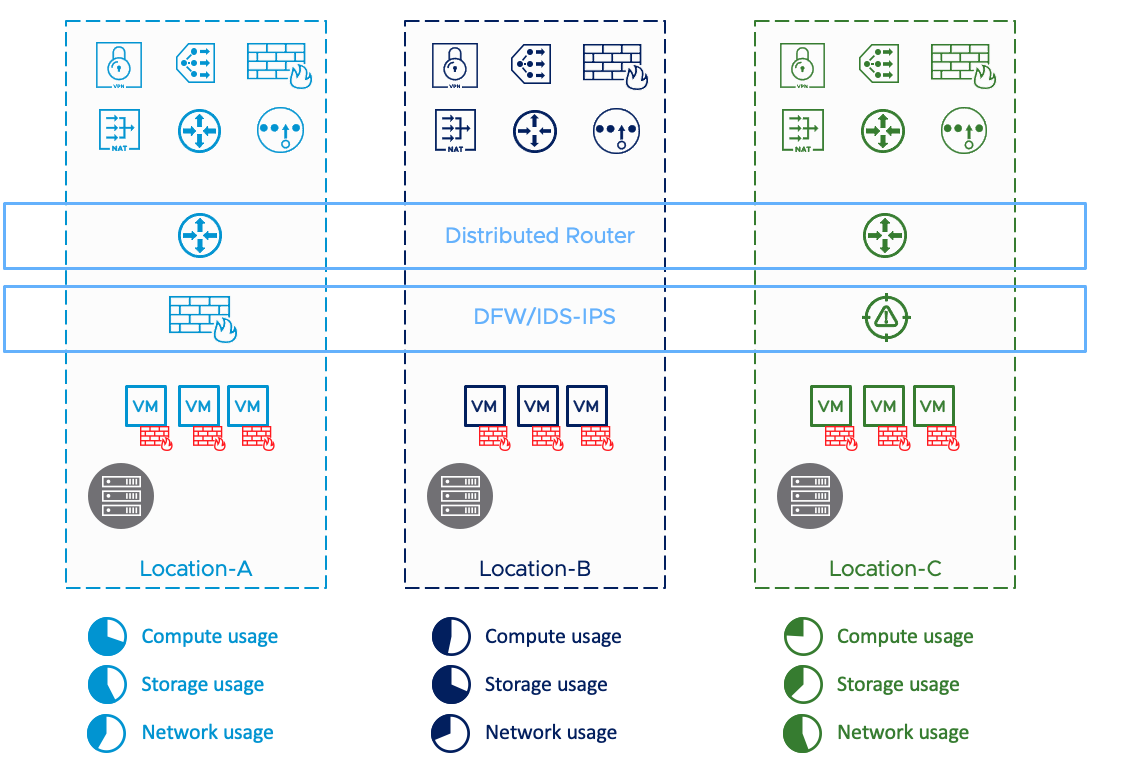
Figure: Multi-Cloud Growth
Disaster Avoidance / Disaster Recovery
This is a scenario where you lose one of your locations completely (rack, building, site) and you need to maintain the availability of your application services (compute, storage, network and security).

Figure: Multi-Location DR
Simplifying Deployment and Operations with NSX Federation
Continue reading






