Heavy Networking 602: All About SPF, DKIM, DMARC Email Security
Today on Heavy Networking, all about improving email security with SPF (Sender Policy Framework), DMARC (Domain-based Message Authentication, Reporting & Conformance), and DKIM (Domain Keys Identified Mail). Our guest is Alex Blackie. He wrote an article on Email Authenticity 101 that I thought explained these topics really well. If you're a domain manager, you should listen to this one, even if you don't route mail through your domain. You can keep the bad guys from spamming in your name!
The post Heavy Networking 602: All About SPF, DKIM, DMARC Email Security appeared first on Packet Pushers.
Choosing the Least Incorrect Answer

My son was complaining to me the other day that he missed on question on a multiple choice quiz in his class and he got a low B grade instead of getting a perfect score. When I asked him why he was frustrated he told me, “Because it was easy and I missed it. But I think the question was wrong.” As usual, I pressed him further to explain his reasoning and found out that the question was indeed ambiguous but the answer choices were pretty obviously wrong all over. He asked me why someone would write a test like that. Which is how he got a big lesson on writing test questions.
Spin the Wheel
When you write a multiple choice test question for any reputable exam you are supposed to pick “wrong” answers, known as distractors, that ensure that the candidate doesn’t have a better than 25% chance of guessing the correct answer. You’ve probably seen this before because you took some kind of simple quiz that had answers that were completely wrong to the point of being easy to pick out. Those quizzes are usually designed to be passed with the minimum amount of effort.
Dell Ties Storage To Kubernetes, Sharpens Edge Strategy
Dell Technologies, since its founding 37 years ago, has been about infrastructure, from the servers, networking systems and storage appliances that populate enterprise datacenters to the corporate clients that are designed to make employees more productive. …
Dell Ties Storage To Kubernetes, Sharpens Edge Strategy was written by Jeffrey Burt at The Next Platform.
Introducing Cloudflare’s Technology Partner Program

The Internet is built on a series of shared protocols, all working in harmony to deliver the collective experience that has changed the way we live and work. These open standards have created a platform such that a myriad of companies can build unique services and products that work together seamlessly. As a steward and supporter of an open Internet, we aspire to provide an interoperable platform that works with all the complementary technologies that our customers use across their technology stack. This has been the guiding principle for the multiple partnerships we have launched over the last few years.
One example is our Bandwidth Alliance — launched in 2018, this alliance with 18 cloud and storage providers aims to reduce egress fees, also known as data transfer fees, for our customers. The Bandwidth Alliance has broken the norms of the cloud industry so that customers can move data more freely. Since then, we have launched several technology partner programs with over 40+ partners, including:
- Analytics — Visualize Cloudflare logs and metrics easily, and help customers better understand events and trends from websites and applications on the Cloudflare network.
- Network Interconnect — Partnerships with best-in-class Interconnection platforms offer private, Continue reading
Kicking Off Cloudflare’s Summer 2022 Internship Program

Fall is my favorite season for numerous reasons: the change in temperature, pumpkin spice flavored...everything, and of course, the start of the university recruitment cycle. I am excited to announce Cloudflare has begun hiring for our Summer 2022 internship program. We just opened many of our internship roles on our careers website and will begin reviewing applications on a rolling basis. We are looking for Software Engineer, Product Management, Research, Data Science interns and more. We also have a host of virtual events and tech talks to engage prospective students throughout October and November. Find our event lineup below and RSVP through the attached links by clicking on the event titles.
| Date | Time | |
|---|---|---|
| Inside Look: Hiring Software Engineering Interns and New Grads | October 15, 2021 | 10:00-10:45 PT |
| Inside Look: Cloudflare’s Intern Hiring Process | October 19, 2021 | 11:15-12:00 PT |
| Inside Look: Nativeflare | October 27, 2021 | 10:45-11:30 PT |
| Inside Look: Cloudflare’s Intern Experiences | October 28, 2021 | 13:00-13:45 PT |
| Inside Look: Cloudflare’s Culture | November 11, 2021 | 13:00-13:30 PT |
*We have many more events coming up later in the fall and early spring 2022, join our community here for news and updates from us!
In September, Cloudflare kicked off our fall Continue reading
AWS Networking – Part XI: VPC NAT Gateway
Introduction
Back-End EC2 instances like Application and Database servers are most often launched on a Private subnet. As a recap, a Private subnet is a subnet that doesn’t have a route to the Internet Gateway in its Route table. Besides, EC2 instances in the Private subnet don’t have Elastic-IP address association. These two facts mean that EC2 instances on the Private subnet don’t have Internet access. However, these EC2 instances might still need occasional Internet access to get firmware upgrades from the external source. We can use a NAT Gateway (NGW) for allowing IPv4 Internet traffic from Private subnets to the Internet. When we launch an NGW, we also need to allocate an Elastic-IP address (EIP) and associate it with the NGW. This association works the same way as the EIP-to-EC2 association. It creates a static NAT entry to IGW that translates NGW’s local subnet address to its associated EIP. The NGW, in turn, is responsible for translating the source IP address from the ingress traffic originated from the Private subnet to its local subnet IP address. As an example, EC2 instance NWKT-EC2-Back-End sends packets towards the Internet to NGW. When the NGW receives these packets, it rewrites the source IP address 10.10.1.172 with its Public subnet IP address 10.10.0.195 and forwards packets to the Internet gateway. IGW translates the source IP address 10.10.0.195 to EIP 18.132.96.95 (EIP associated with NGW). That means that the source IP of data is rewritten twice, first by NGW and then by IGW.
Figure 4-1 illustrates our example NAT GW design and its configuration steps. As a pretask, we launch an EC2 instance on the Private subnet 10.10.1.0/24 (1). We also modify the existing Security Group (SG) to allow an Inbound/Outbound ICMP traffic within VPC CIDR 10.10.0.0/16 (2). We also allow an SSH session initiation from the 10.10.0.218/24. I’m using the same SG for both EC2 instances to keep things simple. Besides, both EC2 uses the same Key Pair. Chapter 3 shows how to launch an EC2 instance and how we modify the SGs, and that is why we go ahead straight to the NGW configuration.
When we have done pre-tasks, we launch an NGW on the Public subnet (3). Then we allocate an EIP and associate it with NGW (4). Next, we add a default route towards NGW on the Private subnet Route Table (5).
The last three steps are related to connectivity testing. First, verify Intra-VPC IP connectivity using ICMP (6). Then we test the Internet connectivity (7). As the last step, we can confirm that no route exists back to NWKT-EC-Backe-End from the IGW. We are using an AWS Path Analyzer for that (8).
Note! Our example doesn’t follow good design principles. AWS Availability Zones (AZ) are restricted failure domains, which means that failure in one AZ doesn’t affect the operation of other AZ. Now, if our NGW on AZ eu-west-2c fails, Internet traffic from the Private subnet on eu-west2a fails. The proper design is to launch NGW on the AZ where unidirectional egress Internet access is needed.
Figure 4-1: Example Topology.
Continue reading
KubeCon + CloudNativeCon Highlights Security for Open Source
Vulnerabilities in the life cycle of open-source software development can start from tiny crumbs but grow into substantial issues.“Look, Ma, no probes!” — Characterizing CDNs’ latencies with passive measurement
Something that comes up a lot at Cloudflare is how well our network and systems are performing. Like many service providers, we need to be engaged in a constant process of introspection to evaluate aspects of Cloudflare’s service with respect to customers, within our own network and systems and, as was the case in a recent blog post, the clients (such as web browsers). Many of these questions are obvious, but answering them is decisive in opening paths to new and improved services. The important point here is that it’s relatively straightforward to monitor and assess aspects of our service we can see or measure directly.
However, for certain aspects of our performance we may not have access to the necessary data, for a number of reasons. For instance, the data sources may be outside our network perimeter, or we may avoid collecting certain measurements that would violate the privacy of end users. In particular, the questions below are important to gain a better understanding of our performance, but harder to answer due to limitations in data availability:
- How much better (or worse!) are we doing compared to other service providers (CDNs) by being in certain locations?
- Can Continue reading
Multi-User IP Address Detection
Cloudflare provides our customers with security tools that help them protect their Internet applications against malicious or undesired traffic. Malicious traffic can include scraping content from a website, spamming form submissions, and a variety of other cyberattacks. To protect themselves from these types of threats while minimizing the blocking of legitimate site visitors, Cloudflare’s customers need to be able to identify traffic that might be malicious.
We know some of our customers rely on IP addresses to distinguish between traffic from legitimate users and potentially malicious users. However, in many cases the IP address of a request does not correspond to a particular user or even device. Furthermore, Cloudflare believes that in the long term, the IP address will be an even more unreliable signal for identifying the origin of a request. We envision a day where IP will be completely unassociated with identity. With that vision in mind, multi-user IP address detection represents our first step: pointing out situations where the IP address of a request cannot be assumed to be a single user. This gives our customers the ability to make more judicious decisions when responding to traffic from an IP address, instead of indiscriminately treating that traffic Continue reading
Geo Key Manager: Setting up a service for scale
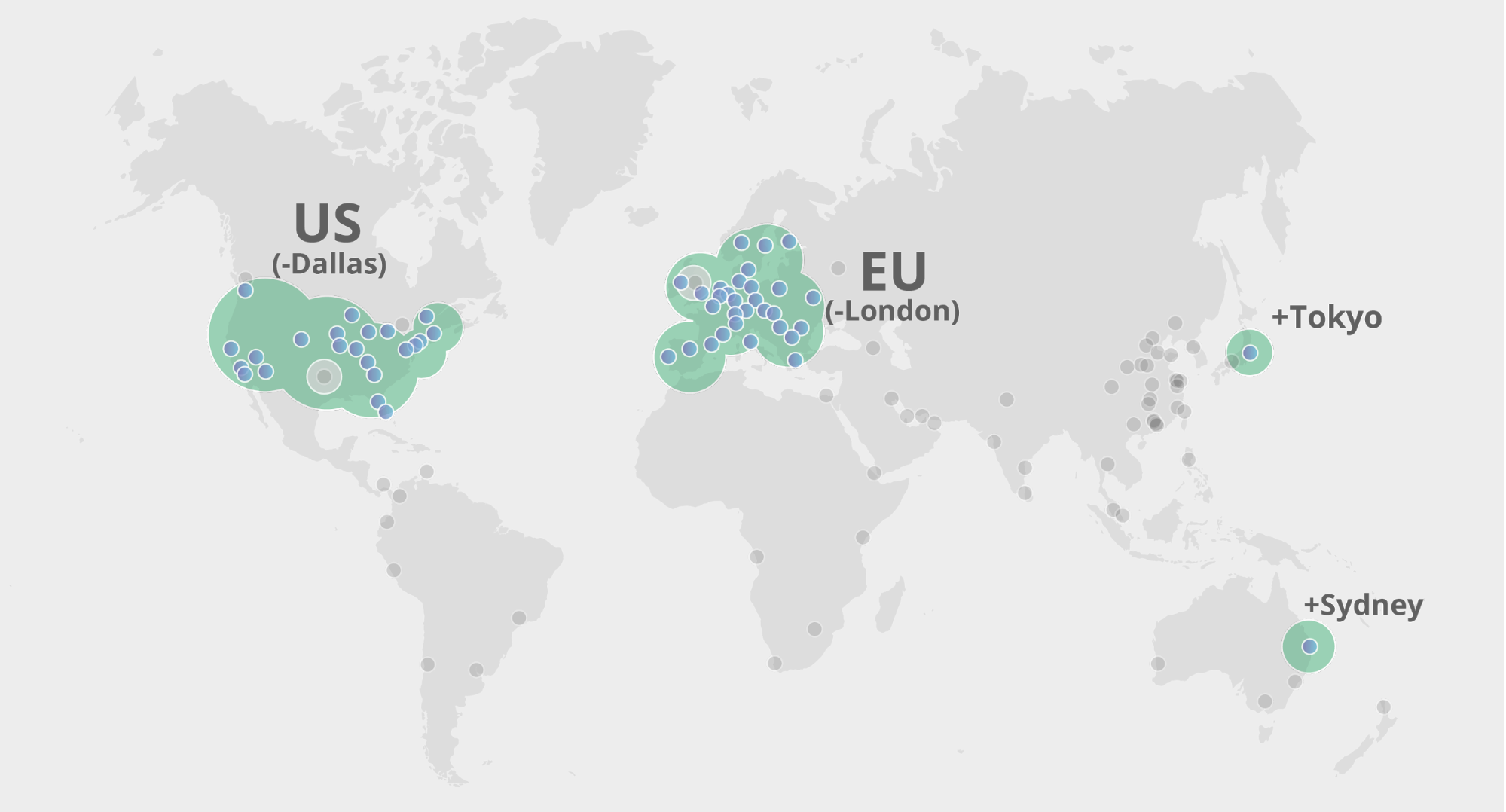
In 2017, we launched Geo Key Manager, a service that allows Cloudflare customers to choose where they store their TLS certificate private keys. For example, if a US customer only wants its private keys stored in US data centers, we can make that happen. When a user from Tokyo makes a request to this website or API, it first hits the Tokyo data center. As the Tokyo data center lacks access to the private key, it contacts a data center in the US to terminate the TLS request. Once the TLS session is established, the Tokyo data center can serve future requests. For a detailed description of how this works, refer to this post on Geo Key Manager.
This is a story about the evolution of systems in response to increase in scale and scope. Geo Key Manager started off as a small research project and, as it got used more and more, wasn’t scaling as well as we wanted it to. This post describes the challenges Geo Key Manager is facing today, particularly from a networking standpoint, and some of the steps along its way to a truly scalable service.
Geo Key Manager started out as a research Continue reading
Lessons Learned: Complexity Will Kill Your System
You wouldn’t believe the intricate network designs I created decades ago until I learned that having uninterrupted sleep is worth more than proving I can get the impossible to work (see also: using EBGP instead of IGP in a 4-node data center fabric).
Once I started valuing my free time, I tried to design things to be as simple as possible. However, as my friend Nicola Modena once said, “Consultants must propose new technologies because they must be seen as bringing innovation,” and we all know complexity sells. Go figure.
Lessons Learned: Complexity Will Kill Your System
You wouldn’t believe the intricate network designs I created decades ago until I learned that having an uninterrupted sleep is worth more than proving I can get the impossible to work (see also: using EBGP instead of IGP in a 4-node data center fabric).
Once I started valuing my free time, I tried to design things to be as simple as possible. However, as my friend Nicola Modena once said, “Consultants must propose new technologies because they must be seen as bringing innovation,” and we all know complexity sells. Go figure.
Missing good old ‘wr’ command on N9K? let’s bring it back!
Doing a lot on Nexus 9000 series datacenter boxes (N9K) lately? Sure you’re missing the good old ‘wr’ command to save your last startup-config into running-config. NXOS architecture guys decided that you should be really well concentrated when deciding to save your nice new configuration to survive device reboot and type: N9K_1(config)# copy running-config startup-config. Just typing ‘wr’ into the console would be too nice right? Let’s use the alias configuration and bring that command back to the box. N9K_1(config)# copy running-config startup-config 100% Copy complete, now saving to disk (please wait)... Copy complete. N9K_1(config)# If you try ‘wr’:
The post Missing good old ‘wr’ command on N9K? let’s bring it back! appeared first on How Does Internet Work.
Calico Cloud: What’s new in October
Calico Cloud is an industry-first security and observability SaaS platform for Kubernetes, containers, and cloud. Since its launch, we have seen customers use Calico Cloud to address a range of security and observability problems for regulatory and compliance requirements in a matter of days and weeks. In addition, they only paid for the services used, instead of an upfront investment commitment, thus aligning their budgets with their business needs.
New in October
We are excited to announce recent Calico Cloud enhancements. Highlights include:
- Managing your security and observability shouldn’t require you to manage a separate credential, authentication, and authorization access workflow. With Calico Cloud, you can bring your identity provider to manage user access to your security and observability platform. Simple sign in now requires login with the same credentials aligned to organizational roles. User management is simplified by leveraging in-house knowledge of identity management for many popular platforms. Calico Cloud supports Microsoft Azure Active Directory, Google IDP, and Open ID.
- Pre-built use case workflows are available in Calico Cloud for workload access control and enterprise security and controls. After signup:
- Users can start monitoring and observing their application and microservices communication to external resources within minutes.
- Users can prevent Continue reading
Networking A Way Into The Datacenter From The Outside In
Every startup has to be both flexible and focused, and it is tough to balance the two. …
Networking A Way Into The Datacenter From The Outside In was written by Timothy Prickett Morgan at The Next Platform.
