Cloudflare Developer Summer Challenge


There are a lot of experiences we have all grown to miss over the last year and a half. After hearing from our community, two of the top experiences they miss are collaborating with peers, and getting Cloudflare swag. Perhaps even in the reverse order! In-person events like conferences were once a key channel to satisfy both these interests, however today’s remote world makes that much harder. But does it have to?
Today, we are excited to introduce the Cloudflare Developer Summer Challenge. We will be rewarding 300 participants with boxes of our most popular swag, while enabling collaboration with other participants through our Workers Discord channel.
To participate, you have to build a project that uses Cloudflare Workers and at least one other product in our rapidly expanding developer platform. We will judge submissions and award swag boxes to those with the most innovative projects, limited to one box per person. The Challenge will be open for submissions between today, and closing November 1, 2021. See a full list of terms and conditions here.
What are the details?
Cloudflare’s developer platform offers all the building blocks to create end-to-end applications with products across compute, storage, and frontend services. To Continue reading
Building the Cloudflare Summer Challenge Application


If you haven’t already heard, we’re hosting the Cloudflare Summer Developer Challenge, a contest for the Cloudflare community at large. Anybody – yes, including you – can sign up for free and compete for a chance to win one of 300 available prizes. To submit you need to use at least two products from the Cloudflare developer platform — which makes this contest a great opportunity to give them a try if you haven’t already! The top 300 submissions will receive a box of our most popular swag, so you should give it a go!
Coincidentally, the Cloudflare Summer Developer Challenge’s landing page and signup workflow qualifies as a valid project submission (so meta), so if you’re looking for some inspiration, this walkthrough will shed some light on how it was built.
Overview
At its core, the application is a series of static HTML pages, most of which have a form to submit, with a backend API to handle those submissions, and a storage layer to persist the data. In a Cloudflare lens, this would point towards using Pages, a Worker, and Workers KV. And while this should be the preferred stack for a project like this, truthfully, this Continue reading
What’s New in VMware HCX 4.2
Real-time Estimation of vMotion and Replication Assisted vMotion Migration
HCX analyzes migration metrics and provides an estimate of the time required to complete the relocation phase of every configured vMotion, as well as the time required to complete the transfer phase of every RAV migration. For each virtual machine migration, the estimate is shown in the progress bar displayed on both the Migration Tracking and Migration Management pages while the transfer is underway.
The following snapshot shows an estimate of time remaining for the vMotion-based migration to complete.

Here we see a similar estimate for a RAV– (Replication Assisted vMotion) based migration.

Predictive Estimation of Replication Assisted vMotion (RAV) Migrations
For RAV migrations in draft state, HCX uses machine learning to generate an estimate of the time required to complete the migration. The estimate is shown in the progress bar displayed on the Migration Management page. Predictive estimation is available for Early Adoption (EA) with both RAV and Bulk migration.
5The following snapshot shows how the user can get a predictive estimate of the time needed for Replication Assisted vMotion (RAV) to migrate workloads of virtual machines in a Mobility group.

OS Assisted Migration (OSAM) with HCX for VMware Cloud
HCX OS Assisted Migrations enable transitions from non-vSphere-based environments to vSphere-based environments. OSAM can now be run in VMware Cloud Continue reading
Next-Gen Insurers Are Going to Need (Way) More AI Horsepower
While involving AI/ML in the complex process of insurance claims now might be piecemeal, the future is bright for insurers to speed time to claim resolution by using image-based data and machine learning models to understand the scope of damage to vehicles or eventually, entire geographic regions. …
Next-Gen Insurers Are Going to Need (Way) More AI Horsepower was written by Nicole Hemsoth at The Next Platform.
Network Visibility: What It Means and How to Achieve It
A step beyond network monitoring, network visibility technology provides deep insights into everything within and moving through your enterprise network.IPv6 Buzz 082: All About Allocations
In today's IPv6 Buzz podcast we discuss IPv6 allocations, which are critical to successful IPv6 adoption. Topics include allocation sizing, address planning, and differences among Regional Internet Registries (RIRs), service providers, and government agencies.IPv6 Buzz 082: All About Allocations
In today's IPv6 Buzz podcast we discuss IPv6 allocations, which are critical to successful IPv6 adoption. Topics include allocation sizing, address planning, and differences among Regional Internet Registries (RIRs), service providers, and government agencies.
The post IPv6 Buzz 082: All About Allocations appeared first on Packet Pushers.
More devices, fewer CAPTCHAs, happier users


Earlier this year we announced that we are committed to making online human verification easier for more users, all around the globe. We want to end the endless loops of selecting buses, traffic lights, and convoluted word diagrams. Not just because humanity wastes 500 years per day on solving other people's machine learning problems, but because we are dedicated to making an Internet that is fast, transparent, and private for everyone. CAPTCHAs are not very human-friendly, being hard to solve for even the most dedicated Internet users. They are extremely difficult to solve for people who don’t speak certain languages, and people who are on mobile devices (which is most users!).
Today, we are taking another step in helping to reduce the Internet’s reliance on CAPTCHAs to prove that you are not a robot. We are expanding the reach of our Cryptographic Attestation of Personhood experiment by adding support for a much wider range of devices. This includes biometric authenticators — like Apple's Face ID, Microsoft Hello, and Android Biometric Authentication. This will let you solve challenges in under five seconds with just a touch of your finger or a view of your face -- without sending this private Continue reading
Introducing Zero-Knowledge Proofs for Private Web Attestation with Cross/Multi-Vendor Hardware
A few weeks ago we introduced Cryptographic Attestation of Personhood to replace CAPTCHAs with USB security keys, and today we announced additional support for on-device biometric hardware. While doing that work, it occurred to us that hardware attestation, proving identity or other properties of a user with a piece of hardware, could have many wider applications beyond just CAPTCHA alternatives and user authentication via WebAuthn. Really, why should someone have to have an account to prove they exist, when their own trusted device can do so?
Attestation in the WebAuthn standard lets websites know that your security key is authentic. It was designed to have good privacy properties baked into policies that must be followed by device manufacturers. The information your security key sends to websites is indistinguishable from that of myriad other keys. Even so, we wanted to do better. If we’re taking attestation out of authentication, then we need to learn only that your security key is authentic — and we’ve designed a new Zero-Knowledge Proof for the browser to do that.
This is part of our work to improve privacy across the Internet. We’ve yet to put this proof of personhood in production, but you can see Continue reading
How to Avoid Security Vulnerabilities When Building Components in Apex
Development teams today are tasked with creating powerful custom capabilities and are pushing out software faster than ever. To keep up, security needs to shift left – or earlier in the development cycle – to leverage DevSecOps for Salesforce's Apex code.Kubernetes observability challenges in cloud-native architecture
Kubernetes is the de-facto platform for orchestrating containerized workloads and microservices, which are the building blocks of cloud-native applications. Kubernetes workloads are highly dynamic, ephemeral, and are deployed on a distributed and agile infrastructure. Although the benefits of cloud-native applications managed by Kubernetes are plenty, Kubernetes presents a new set of observability challenges in cloud-native applications.
Let’s consider some observability challenges:
- Data silos – Traditional monitoring tools specialize in collecting metrics at the application and infrastructure level. Given the highly dynamic, distributed, and ephemeral nature of cloud-native applications, this style of metrics collection creates data in silos that need to be stitched together in the context of a service in order to enable DevOps and SREs to debug service issues (e.g. slow response time, downtime, etc.). Further, if DevOps or service owners add new metrics for observation, data silos can cause broken cross-references and data misinterpretation, leading to data misalignment, slower communication, and incorrect analysis.
- Data volume and granular components – Kubernetes deployments have granular components such as pods, containers, and microservices that are running on top of distributed and ephemeral infrastructure. An incredibly high volume of granular data is generated at each layer as alerts, logs, and Continue reading
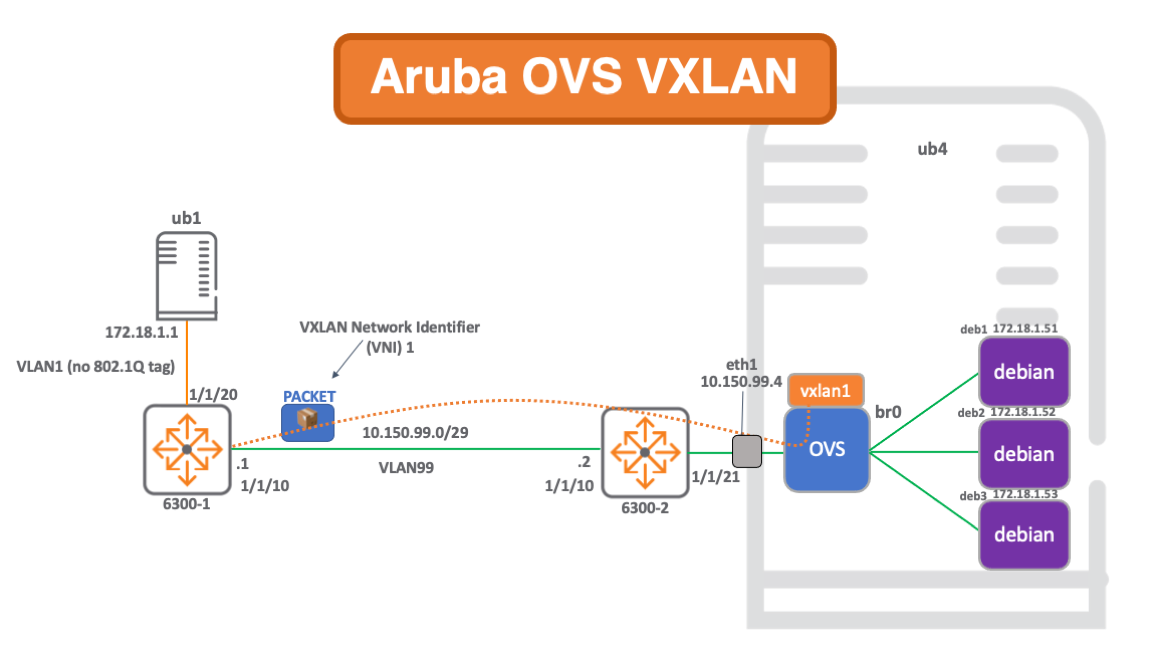
Docker, Openvswitch & Aruba VXLAN Network Build
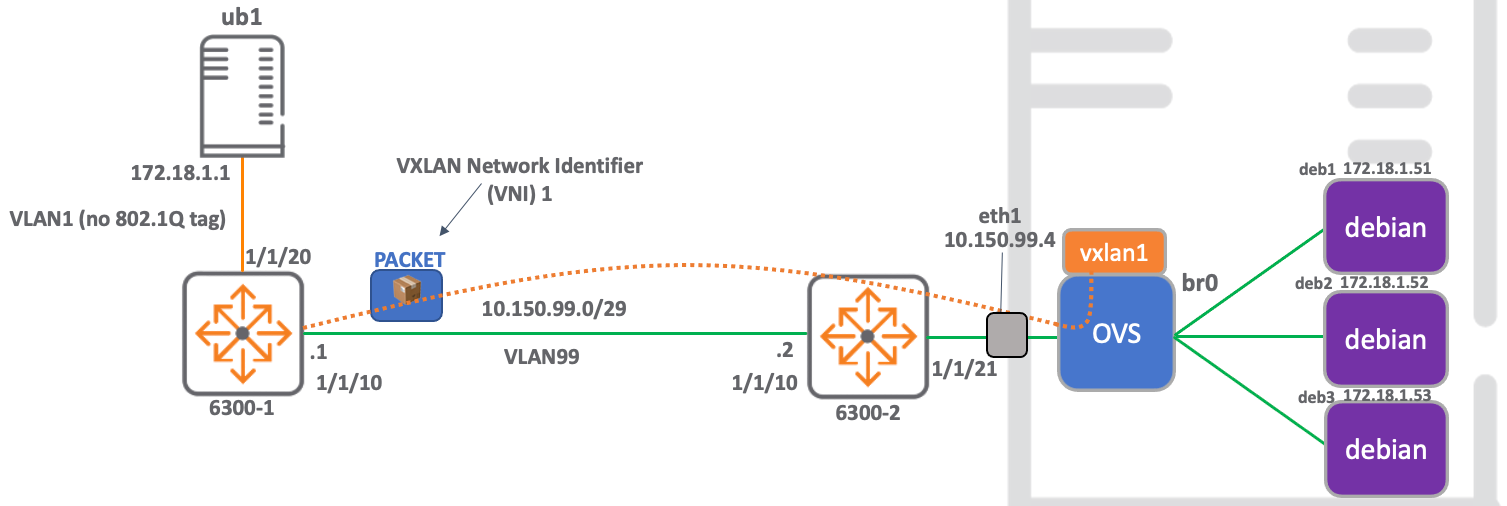
This blog provides details of how to build a static VXLAN network that connects physical hardware to a virtualised network, enabling communication from docker containers to external nodes.
The build is comprised of a hardware ArubaOS-Switch acting as a VTEP and an openvswitch VTEP running on an ubuntu server, which is the host for the docker containers.
This network also serves to prove interoperability between the ArubaOS-Switch VXLAN stack and that running on openvswitch.
The use of docker containers as target nodes enables rapid deploy and tear-down of network components, which is particularly useful in lab environments for testing.
Kit List
2 x ArubaOS-CX 6300 hardware switch (only 1 is required.)
1 x HP EliteDesk PC running Hyper-V hosting an ubuntu 21.04 VM
1 x HP EliteDesk PC running ubuntu 21.04 bare metal.
Notes:
I used a VM for the openvswitch / docker linux server to take advantage of snapshots while documenting this build. This server can be any linux server.
Network Diagram
Build Steps
Configure the ArubaOS-CX hardware switch
- Configure the ArubaOS-CX switch and local server (172.18.1.1) so that they are in the same subnet and can ping each other.
- Configure the ArubaOS-CX Continue reading