0
Over the past few weeks, our team has written a lot about the Cloudflare for Teams Dashboard, and more specifically, about our approach to design and the content within it. In these recent posts, we charted the journey of developing omni-directional communication channels across product, design, and content, and how these relationships directly influence the user experiences we aim to create.
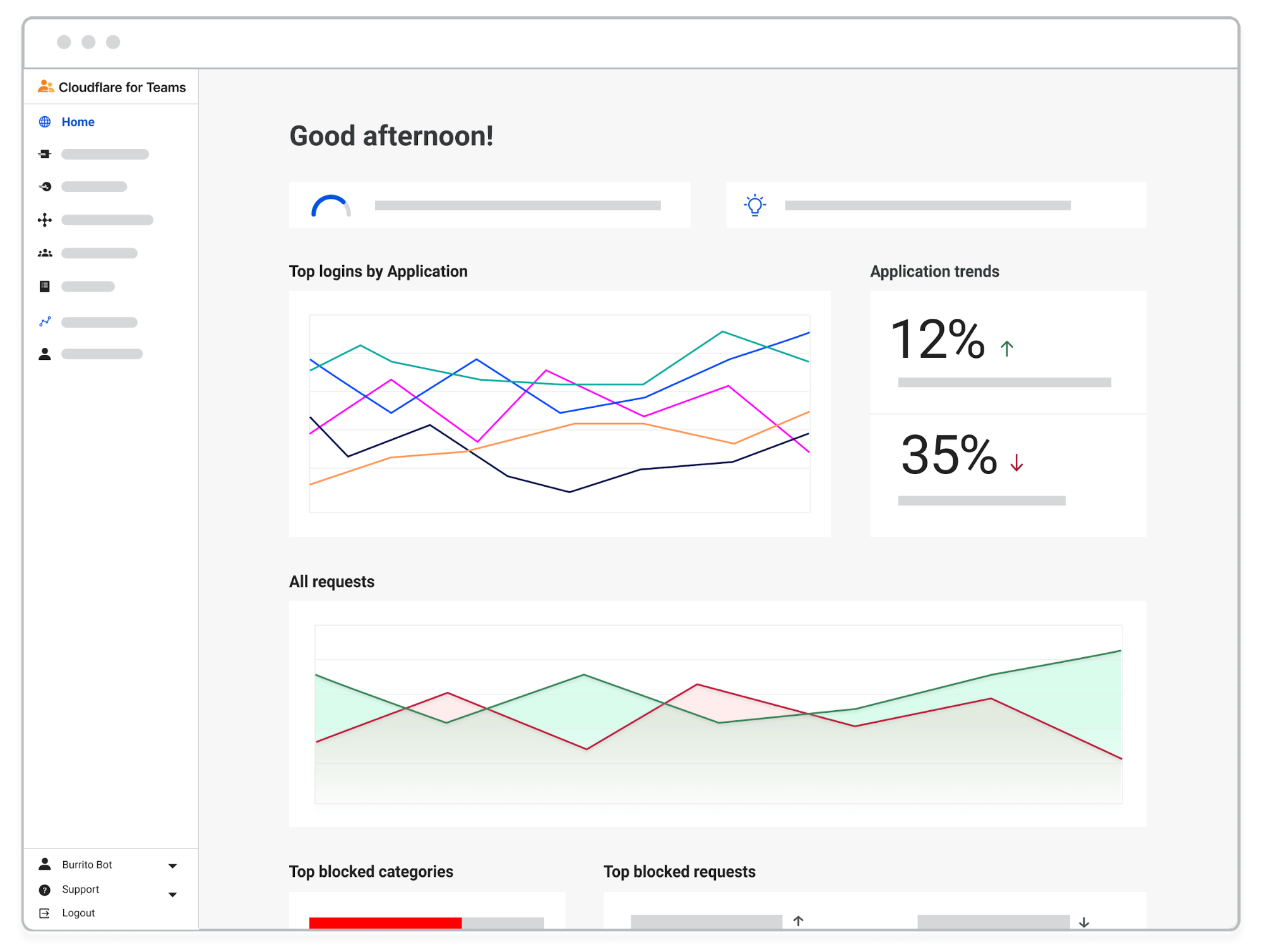
Today, we’re announcing a new feature within the Teams Dash. We called it “Home”. We created Home with a simple goal in mind: design an adaptive and informative landing page where users can see a round-up of their environment.
In this last post of our series, we’ll show, rather than tell, how we collaborated as a team that rows in the same direction and towards the same goal — to create a great user experience.
In this blog post, we’ll walk you through your new Teams Home by calling out a few of the guiding principles we had in mind as we designed it. Transparency, adaptiveness, guidance and warmth aren’t only foundational words in the Cloudflare for Teams product principles — they’re part of our day-to-day brainstorming and discussion around user experience.
Here’s how the Teams Home reflects these Continue reading