Introducing NFA Custom Groups
The post Introducing NFA Custom Groups appeared first on Noction.
The post Introducing NFA Custom Groups appeared first on Noction.
One of my readers is designing a layer-2-only data center fabric (no SVI interfaces on switches) with stringent security requirements using Cisco Nexus switches, and he wondered whether a host connected to such a fabric could attack a switch, and whether it would be possible to reach the management network in that way.
Do you think it’s possible to reach the MANAGEMENT PLANE from the DATA PLANE? Is it valid to think that there is a potential attack vector that someone can compromise to source traffic from the front of the device (ASIC) through the PCI bus across the CPU to the across the PCI bus to the Platform Controller Hub through the I/O card to spew out the Management Port onto that out-of-band network?
My initial answer was “of course there’s always a conduit from the switching ASIC to the CPU, how would you handle STP/CDP/LLDP otherwise”. I also asked Lukas Krattiger for more details; here’s what he sent me:
One of my readers is designing a layer-2-only data center fabric (no SVI interfaces on switches) with stringent security requirements using Cisco Nexus switches, and he wondered whether a host connected to such a fabric could attack a switch, and whether it would be possible to reach the management network in that way.
Do you think it’s possible to reach the MANAGEMENT PLANE from the DATA PLANE? Is it valid to think that there is a potential attack vector that someone can compromise to source traffic from the front of the device (ASIC) through the PCI bus across the CPU to the across the PCI bus to the Platform Controller Hub through the I/O card to spew out the Management Port onto that out-of-band network?
My initial answer was “of course there’s always a conduit from the switching ASIC to the CPU, how would you handle STP/CDP/LLDP otherwise”. I also asked Lukas Krattiger for more details; here’s what he sent me:
Maximizing the aggregate amount of compute that can be brought to bear for any given pile of money is what traditional high performance computing is all about. …
For HPC And AI, Composability Might Trump Cheap Flops was written by Timothy Prickett Morgan at The Next Platform.

One of the positive aspects of this difficult period, if I may say so, is the possibility of taking a Pearson Vue test online, called OnVue. Last Friday, October 23rd, I took a Cisco exam from home and I think it’s interesting to share with you the details of this experience. With OnVue – Get certified from your home! The registration for the exam The registration for the test is almost the same as for a Cisco test done in a Vue test center. Go to the website of Pearson…
The post OnVue – Get certified from your home appeared first on AboutNetworks.net.
2020 has been quite the year. Pandemic, lockdowns, virtual conferences and back-to-back Zoom meetings. Global economic pressures, confinement and webcams aside, we at Docker have been focused on delivering what we set out to do when we announced Docker’s Next Chapter: Advancing Developer Workflows for Modern Apps last November 2019. I wish to thank the Docker team for their “can do!” spirit and efforts throughout this unprecedented year, as well as our community, our Docker Captains, our ecosystem partners, and our customers for their non-stop enthusiasm and support. We could not have had the year we had without you.
This next chapter is being jointly written with you, the developer, as so much of our motivation and inspiration comes from your sharing with us how you’re using Docker. Consider the Washington University School of Medicine (WUSM): WUSM’s team of bioinformatics developers uses Docker to build pipelines – consisting of up to 25 Docker images in some cases – for analyzing the genome sequence data of cancer patients to inform diagnosis and treatments. Furthermore, they collaborate with each other internally and with other cancer research institutions by sharing their Docker images through Docker Hub. In the words of WUSM’s Dr. Continue reading
The rumors were right, and AMD president and chief executive officer Lisa Su is indeed printing out a tower of stock to acquire FPGA maker Xilinx for what amounts to about $35 billion and, as it turns out, she is relinquishing her position as president to Victor Peng, chief executive at Xilinx, to close the deal. …
AMD Girds For Compute War With Xilinx Deal was written by Timothy Prickett Morgan at The Next Platform.

Before the large cable providers came on the scene, most people accessed the Internet through dial-up MODEMS, connecting to services like America Online, across plain old telephone lines. The entrance of cable providers, and cable MODEMs, allowed the edge of the Internet to explode, causing massive growth. Join Donald Sharp and I on this episode of the History of Networking as John Chapman discusses the origins of the cable MODEM, and the origins of the DOCSIS standards.
Zero trust network access is ideal for today's distributed workforce, but it can be tricky to put into place. On today's sponsored Heavy Networking podcast, we talk with NetMotion about its remote access product that enable zero trust plus performance monitoring to help troubleshoot problems for remote workers. Our guest is Jay Klauser, VP of Worldwide Sales Engineering & Alliances at NetMotion.
The post Heavy Networking 546: Making Zero Trust Remote Access Work (Sponsored) appeared first on Packet Pushers.
Docker is happy to announce the GA of our V2 Github Action. We’ve been working with @crazy-max over the last few months along with getting feedback from the wider community on how we can improve our existing Github Action. We have now moved from our single action to a clearer division and advanced set of options that not only allow you to just build & push but also support features like multiple architectures and build cache.
The big change with the advent of our V2 action is also the expansion of the number of actions that Docker is providing on Github. This more modular approach and the power of Github Actions has allowed us to make the minimal UX changes to the original action and add a lot more functionality.
We still have our more meta build/push action which does not actually require all of these preconfiguration steps and can still be used to deliver the same workflow we had with the previous workflow! To Upgrade the only changes are that we have split out the login to a new step and also now have a step to setup our builder.
-
name: Setup Docker Buildx
uses: docker/setup-buildx-action@v1This Continue reading

The COVID-19 pandemic has not only caused more than one million deaths worldwide, but it is also accelerating a decline in Internet freedoms across the globe, according to a new report from Freedom House.
The past year has been “especially dismal” for Internet Freedom, according to the Freedom on the Net 2020 report, sponsored by the Internet Society. Political leaders have used the pandemic as an excuse to limit access to information and to roll out new surveillance measures, the report says.
At the same time, a slow-motion splintering of the Internet has turned into an “all-out race toward ‘cyber sovereignty,’ with each government imposing its own internet regulations in a manner that restricts the flow of information across national borders,” the report says. Authorities in several countries, including the U.S., China, Russia, Brazil, and Turkey have erected new digital borders.
As a result, Internet freedoms have declined for the 10th consecutive year, says the report, which tracks Internet freedom in 65 countries, covering 87 percent of the world’s Internet users. From May 2019 to June 2020, the report found Internet freedom scores dropping in 26 countries, with 22 registering net gains.
The largest declines occurred in Continue reading
![Diving into /proc/[pid]/mem](http://blog.cloudflare.com/content/images/2020/10/image3-25.png)
![Diving into /proc/[pid]/mem](http://blog.cloudflare.com/content/images/2020/10/image2-27.png)
A few months ago, after reading about Cloudflare doubling its intern class size, I quickly dusted off my CV and applied for an internship. Long story short: now, a couple of months later, I found myself staring into Linux kernel code and adding a pretty cool feature to gVisor, a Linux container runtime.
My internship was under the Emerging Technologies and Incubation group on a project involving gVisor. A co-worker contacted my team about not being able to read the debug symbols of stack traces inside the sandbox. For example, when the isolated process crashed, this is what we saw in the logs:
*** Check failure stack trace: ***
@ 0x7ff5f69e50bd (unknown)
@ 0x7ff5f69e9c9c (unknown)
@ 0x7ff5f69e4dbd (unknown)
@ 0x7ff5f69e55a9 (unknown)
@ 0x5564b27912da (unknown)
@ 0x7ff5f650ecca (unknown)
@ 0x5564b27910fa (unknown)
Obviously, this wasn't very useful. I eagerly volunteered to fix this stack unwinding code - how hard could it be?
After some debugging, we found that the logging library used in the project opened /proc/self/mem to look for ELF headers at the start of each memory-mapped region. This was necessary to calculate an offset to find the correct addresses for debug symbols.
It turns out this mechanism is rather Continue reading
I should have known better, but I got pulled into another stretched VLANs for disaster recovery tweetfest. Surprisingly, most of the tweets were along the lines of you really shouldn’t be doing that and that would never work well, but then I guess I was only exposed to a small curated bubble of common sense… until this gem appeared in my timeline:
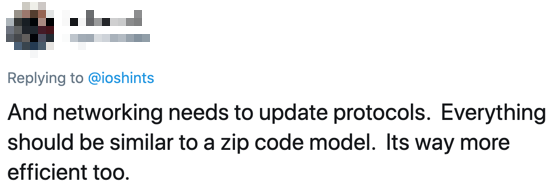
Interestingly, that’s exactly how IP works:
I should have known better, but I got pulled into another stretched VLANs for disaster recovery tweetfest. Surprisingly, most of the tweets were along the lines of you really shouldn’t be doing that and that would never work well, but then I guess I was only exposed to a small curated bubble of common sense… until this gem appeared in my timeline:

Interestingly, that’s exactly how IP works: