Worth Reading: Does your hammer own you?
My friend Marjan Bradeško wrote a great article describing how we tend to forget common sense and rely too much on technology. I would strongly recommend you read it and start thinking about the choices you make when building a network with magic software-intent-defined-intelligent technology from your preferred vendor.
Worth Reading: Does your hammer own you?
My friend Marjan Bradeško wrote a great article describing how we tend to forget common sense and rely too much on technology. I would strongly recommend you read it and start thinking about the choices you make when building a network with magic software-intent-defined-intelligent technology from your preferred vendor.
One more (Zero Trust) thing: Cloudflare Intrusion Detection System
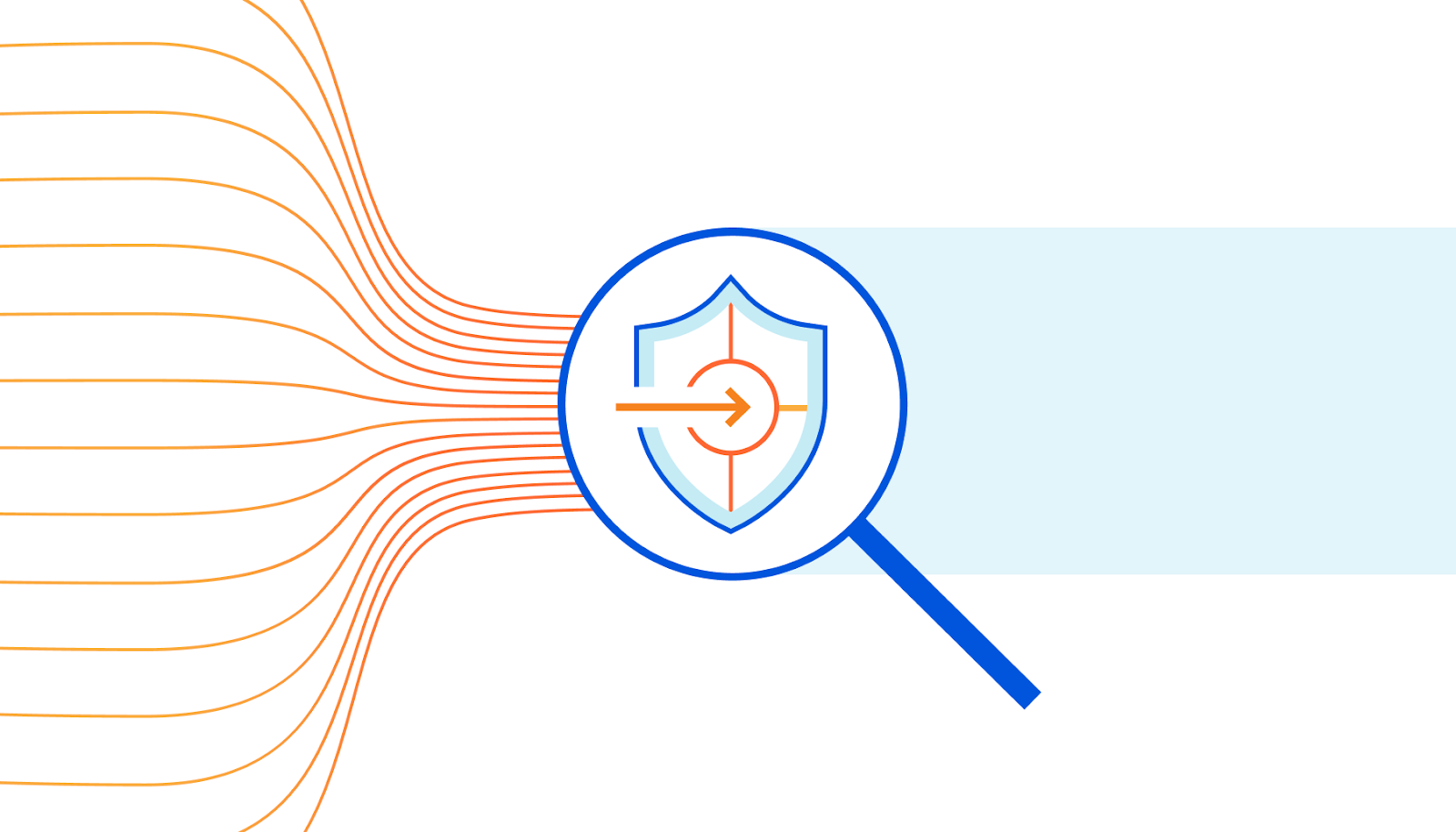
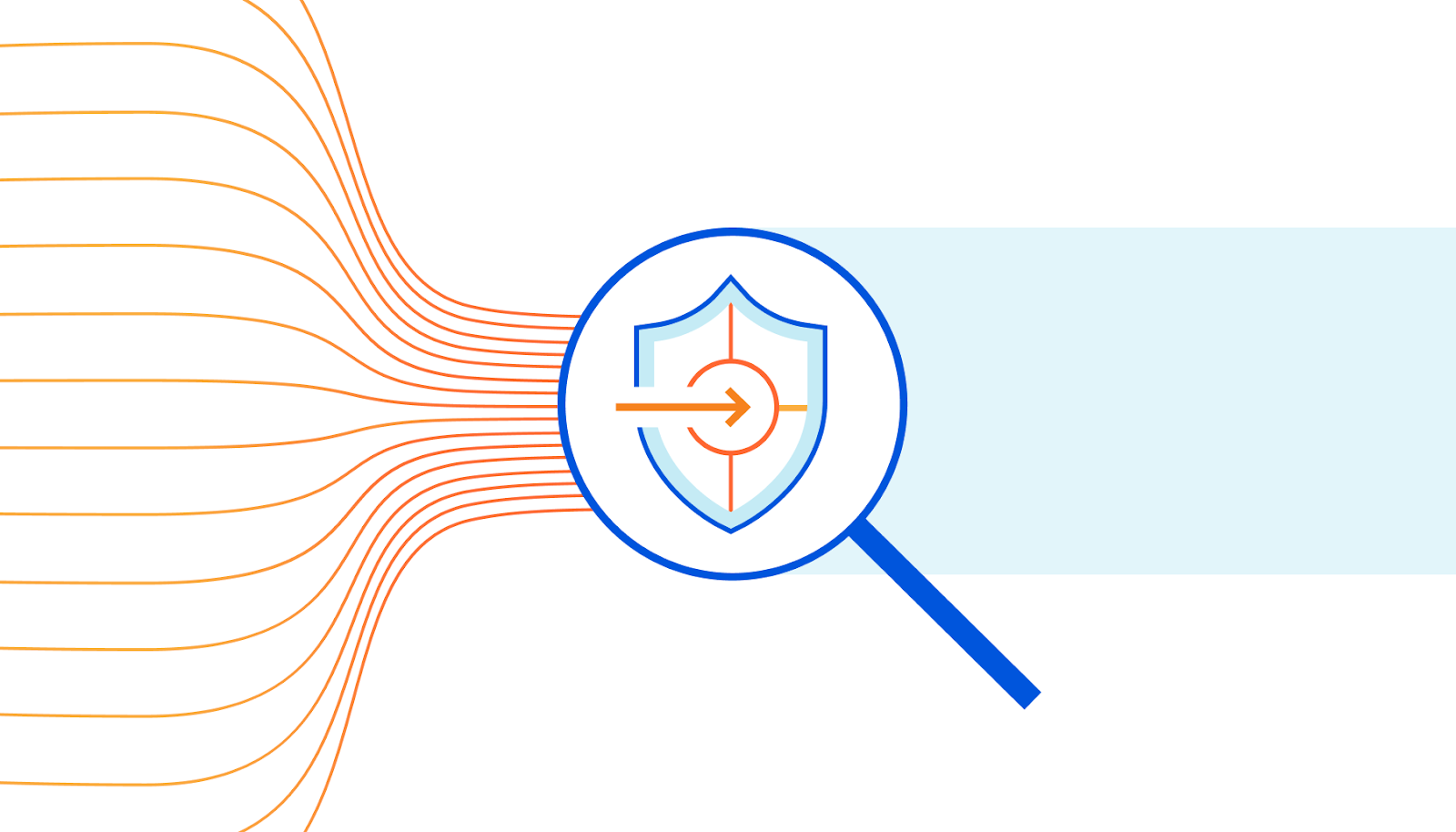
Today, we’re very excited to announce our plans for Cloudflare Intrusion Detection System, a new product that monitors your network and alerts when an attack is suspected. With deep integration into Cloudflare One, Cloudflare Intrusion Detection System gives you a bird’s eye view of your entire global network and inspects all traffic for bad behavior, regardless of whether it came from outside or inside your network.
Analyze your network without doing the legwork
Enterprises build firewall rules to keep their networks safe from external and internal threats. When bad actors try to attack a network, those firewalls check if the attack matches a rule pattern. If it does, the firewall steps in and blocks the attack.
Teams used to configure those rules across physical firewall appliances, frequently of different makes and models, deployed to physical locations. Yesterday, we announced Magic Firewall, Cloudflare’s network-level firewall delivered in our data centers around the world. Your team can write a firewall rule once, deploy it to Cloudflare, and our global network will protect your offices and data centers without the need for on-premises hardware.
This is great if you know where attacks are coming from. If you don’t have that level Continue reading
Zero-Touch Provisioning with Nornir
In early 2018 I described how Hans Verkerk implemented zero-touch provisioning with Ansible. Recently he rewrote his scripts as a Python-only solution using Nornir. Enjoy!
Zero-Touch Provisioning with Nornir
In early 2018 I described how Hans Verkerk implemented zero-touch provisioning with Ansible. Recently he rewrote his scripts as a Python-only solution using Nornir. Enjoy!
No, that’s not how warrantee expiration works
The NYPost Hunter Biden story has triggered a lot of sleuths obsessing on technical details trying to prove it's a hoax. So far, these claims are wrong. The story is certainly bad journalism aiming to misinform readers, but it has not yet been shown to be a hoax.
In this post, we look at claim the timelines don't match up with the manufacturing dates of the drives. Sleuths claim to prove the drives were manufactured after the events in question, based on serial numbers.
What this post will show is that the theory is wrong. Manufacturers pad warrantee periods. Thus, you can't assume a date of manufacture based upon the end of a warrantee period.
The story starts with Hunter Biden (or associates) dropping off a laptop at a repair shop because of water damage. The repair shop made a copy of the laptop's hard drive, stored on an external drive. Later, the FBI swooped in and confiscated both the laptop and that external drive.
The serial numbers of both devices are listed in the subpoena published by the NYPost:
You can enter these serial numbers in the support pages at Apple (FVFXC2MMHV29) and Western Digital (WX21A19ATFF3) to discover precisely Continue reading
Next Platform TV: October 16, 2020
Front Row with Frontera; Spectrum Scale Strategy; Computational Storage Deep Dive; Neural Programming Frontiers; MLPerf for HPC + More…
On today’s episode for the week, we talk to Dan Stanzione, director of the Texas Advanced Computing Center, to get an update on the “Frontera” supercomputer. …
Next Platform TV: October 16, 2020 was written by Nicole Hemsoth at The Next Platform.
No, font errors mean nothing in that NYPost article
The NYPost has an article on Hunter Biden emails. Critics claim that these don't look like emails, and that there are errors with the fonts, thus showing they are forgeries. This is false. This is how Apple's "Mail" app prints emails to a PDF file. The font errors are due to viewing PDF files within a web browser -- you don't see them in a PDF app.
In this blogpost, I prove this.
I'm going to do this by creating forged email. The point isn't to prove the email wasn't forged, it could easily have been -- the NYPost didn't do due diligence to prove they weren't forged. The point is simply that that these inexplicable problems aren't evidence of forgery. All emails printed by the Mail app to a PDF, then displayed with Scribd, will look the same way.
To start with, we are going to create a simple text file on the computer called "erratarob-conspire.eml". That's what email messages are at the core -- text files. I use Apple's "TextEdit" app on my MacBook to create the file.
The structure of an email is simple. It has a block of "metadata" consisting of fields separated by a Continue readingUsing Social Media Content for Screening in Recruitment and Selection: Pros and Cons for Employers
Social media has become a popular tool these days. Many organizations use social media content for screening in recruitment and selection to scan and shortlist the job candidates. They do it by learning more about them through Facebook, Twitter, Instagram, and many more platforms. They search for the candidates on these platforms to learn about their lifestyles, interests, and hobbies. In this way, they can deduce whether these candidates can serve as an asset to the organization or not. Thus, it has become a common recruitment process these days.
Just like everything has its pros and cons, using social media content for screening in recruitment and selection: pros and cons are present too. There has been a long debate on the pros and cons of this screening method. Let’s take a look at them below.
Pros of Using Social Media For Screening
· Insight into the Informal Life of the Job Candidate
The candidate tries to be as formal as possible during the job interview. They are pretending to be something they are actually not, because they want to impress the interviewer to land that job. Therefore, employers are not able to deduce what the candidate is actually Continue reading
In Africa, Strengthening Digital Infrastructure for a Safe Return to Schools

When COVID-19 struck Africa, governments imposed temporary or full shutdowns of education systems to contain its spread. At least 53 out of the 54 African countries took measures that canceled or partially closed schools. Kenya, for example, canceled the 2020 academic year in March, before changing its directives six months later to allow schools to reopen.
No Internet, No Schools
Across the Democratic Republic of Congo, Liberia, Nigeria, and South Africa, where governments imposed partial closure, the few students with access to the Internet, mobile devices, and computers continue learning. But for the majority, there is no schooling. Most can’t afford the cost of Internet data, and very few have access to smartphones and computers. They must improvise to learn, thus widening disparities between learners with Internet access and those without. How can Africa close this gap and offer equal learning opportunities to everyone?
As we gear up towards resuming formal education, there is general panic among parents about the implications resulting from the major learning disruptions. Could COVID-19 lead to a lost generation of students?
Solutions for a Safe Return
Fortunately, African decision-makers are shifting their positions on schools as we learn to live with COVID-19. Governments across the Continue reading
How our network powers Cloudflare One
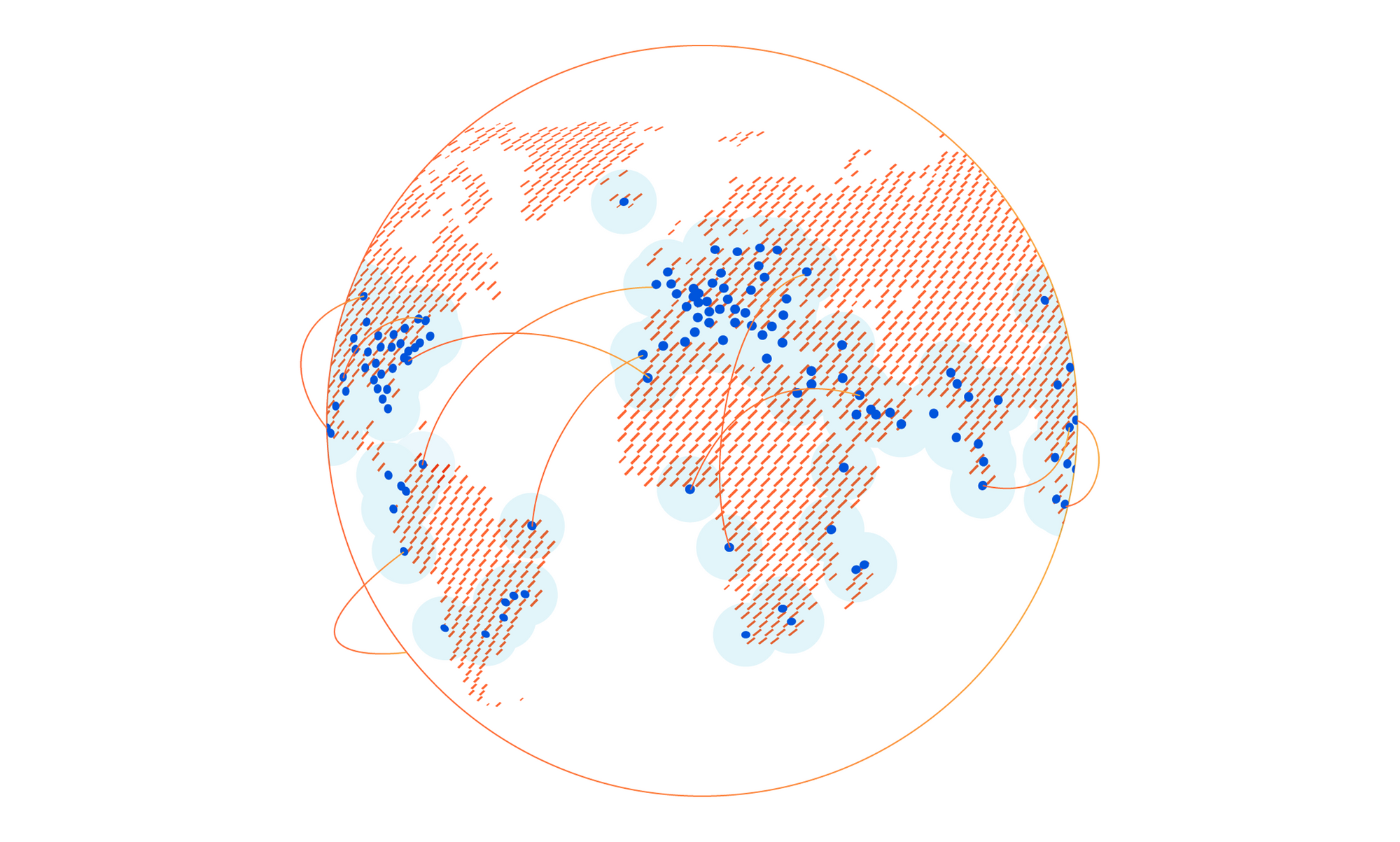
Earlier this week, we announced Cloudflare One™, a unified approach to solving problems in enterprise networking and security. With Cloudflare One, your organization’s data centers, offices, and devices can all be protected and managed in a single control plane. Cloudflare’s network is central to the value of all of our products, and today I want to dive deeper into how our network powers Cloudflare One.
Over the past ten years, Cloudflare has encountered the same challenges that face every organization trying to grow and protect a global network: we need to protect our infrastructure and devices from attackers and malicious outsiders, but traditional solutions aren’t built for distributed networks and teams. And we need visibility into the activity across our network and applications, but stitching together logging and analytics tools across multiple solutions is painful and creates information gaps.
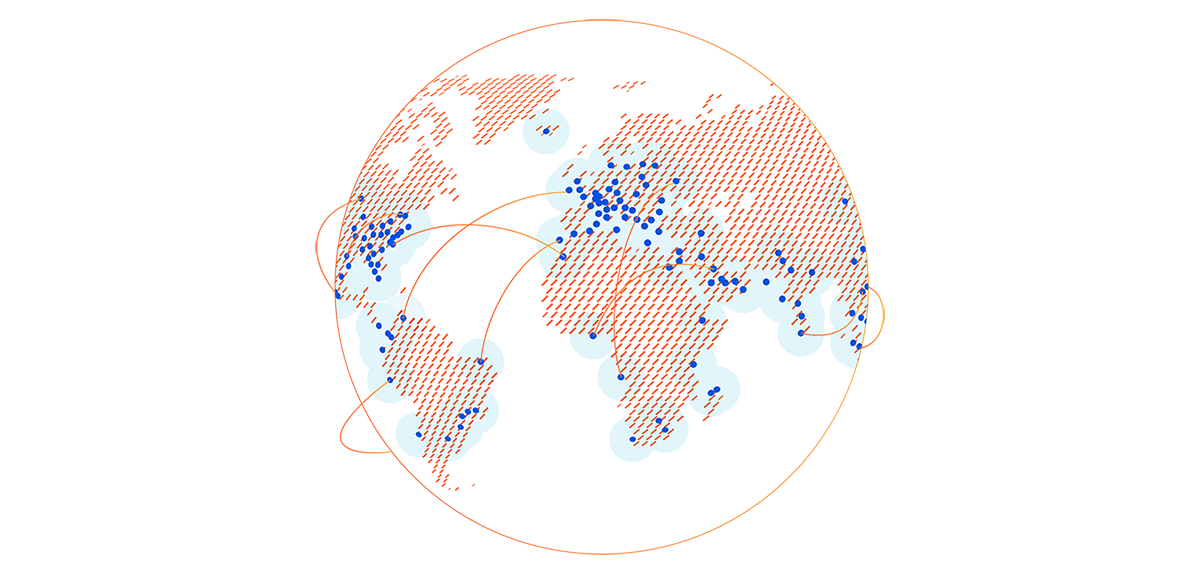
We’ve architected our network to meet these challenges, and with Cloudflare One, we’re extending the advantages of these decisions to your company’s network to help you solve them too.
Distribution
Enterprises and some small organizations alike have team members around the world. Legacy models of networking forced traffic back through central choke points, slowing down users and constraining network scale. Continue reading
Heavy Networking 544: Building Effective Network Monitoring Solutions With Codilime (Sponsored)
Monitoring and visibility are critical to network operations. On today's sponsored Heavy Networking show, we talk with sponsor Codilime about custom development and integration of network monitoring and management tools for the data center and cloud. Our guests from Codilime are are Monika Antoniak, Head of R&D; and Edyta Kałka, Senior Project Manager.Heavy Networking 544: Building Effective Network Monitoring Solutions With Codilime (Sponsored)
Monitoring and visibility are critical to network operations. On today's sponsored Heavy Networking show, we talk with sponsor Codilime about custom development and integration of network monitoring and management tools for the data center and cloud. Our guests from Codilime are are Monika Antoniak, Head of R&D; and Edyta Kałka, Senior Project Manager.
The post Heavy Networking 544: Building Effective Network Monitoring Solutions With Codilime (Sponsored) appeared first on Packet Pushers.
Imposters Among Us

Have you been playing Among Us? If you haven’t, your kids definitely have. I found out about it a few weeks ago because my children suddenly became Batman-level detectives and knew how to ask the kinds of interview questions that would make the FBI proud. In short, the game is all about finding the imposters in your midst based on their behavior and voting them out of the group to win. Sometimes you get it right. Other times you get it wrong and vote out someone who was doing legitimate tasks. It’s all a matter of perception.
Now, let’s look at another situation where we see this kind of behavior in a different light. You probably guessed where this is going already. We’re going to talk about Imposter Syndrome in our non-gaming lives and how it affects us. We may even make reference to pop culture along the way.
Where You Need To Be
I was thinking about this because something I said a few years ago at Security Field Day 1 popped back up in my feed. I was giving a speech at the beginning of the first day to the delegates and I wanted them to know that Continue reading
Introducing Magic Firewall
Today we’re excited to announce Magic Firewall™, a network-level firewall delivered through Cloudflare to secure your enterprise. Magic Firewall covers your remote users, branch offices, data centers and cloud infrastructure. Best of all, it’s deeply integrated with Cloudflare One™, giving you a one-stop overview of everything that’s happening on your network.
Cloudflare Magic Transit™ secures IP subnets with the same DDoS protection technology that we built to keep our own global network secure. That helps ensure your network is safe from attack and available and it replaces physical appliances that have limits with Cloudflare’s network.
That still leaves some hardware onsite, though, for a different function: firewalls. Networks don’t just need protection from DDoS attacks; administrators need a way to set policies for all traffic entering and leaving the network. With Magic Firewall, we want to help your team deprecate those network firewall appliances and move that burden to the Cloudflare global network.
Firewall boxes are miserable to manage
Network firewalls have always been clunky. Not only are they expensive, they are bound by their own hardware constraints. If you need more CPU or memory, you have to buy more boxes. If you lack capacity, the entire network suffers, directly Continue reading
Video: Simplify Device Configurations with Cumulus Linux
The designers of Cumulus Linux CLI were always focused on simplifying network device configurations. One of the first features along these lines was BGP across unnumbered interfaces, then they introduced simplified EVPN configurations, and recently auto-MLAG and auto-BGP.
You can watch a short description of these features by Dinesh Dutt and Pete Lumbis in Simplify Network Configuration with Cumulus Linux and Smart Datacenter Defaults videos (part of Cumulus Linux section of Data Center Fabrics webinar).
Video: Simplify Device Configurations with Cumulus Linux
The designers of Cumulus Linux CLI were always focused on simplifying network device configurations. One of the first features along these lines was BGP across unnumbered interfaces, then they introduced simplified EVPN configurations, and recently auto-MLAG and auto-BGP.
You can watch a short description of these features by Dinesh Dutt and Pete Lumbis in Simplify Network Configuration with Cumulus Linux and Smart Datacenter Defaults videos (part of Cumulus Linux section of Data Center Fabrics webinar).
Intel Networking: Not Just A Bag Of Parts
What is the hardest job at Intel, excepting whoever is in charge of the development of chip etching processes and the foundries that implement it? …
Intel Networking: Not Just A Bag Of Parts was written by Timothy Prickett Morgan at The Next Platform.

