Cloudflare Bot Management: machine learning and more

Introduction

Building Cloudflare Bot Management platform is an exhilarating experience. It blends Distributed Systems, Web Development, Machine Learning, Security and Research (and every discipline in between) while fighting ever-adaptive and motivated adversaries at the same time.
This is the ongoing story of Bot Management at Cloudflare and also an introduction to a series of blog posts about the detection mechanisms powering it. I’ll start with several definitions from the Bot Management world, then introduce the product and technical requirements, leading to an overview of the platform we’ve built. Finally, I’ll share details about the detection mechanisms powering our platform.
Let’s start with Bot Management’s nomenclature.
Some Definitions
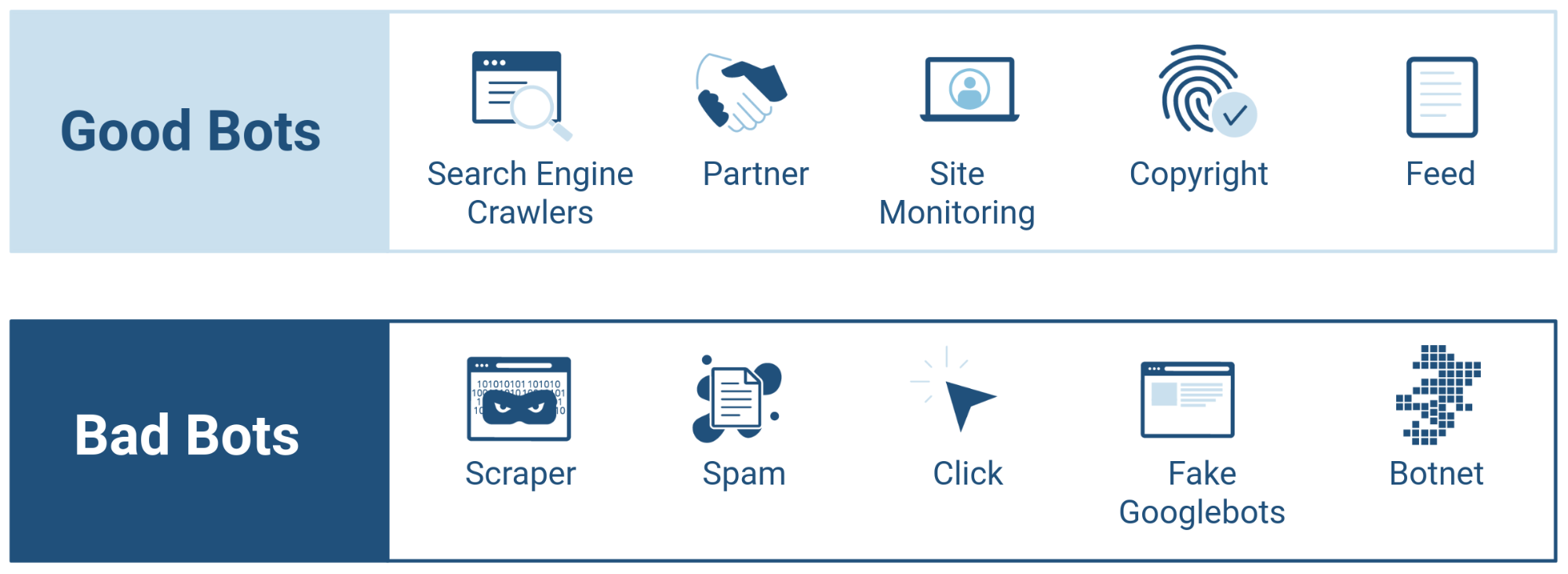
Bot - an autonomous program on a network that can interact with computer systems or users, imitating or replacing a human user's behavior, performing repetitive tasks much faster than human users could.
Good bots - bots which are useful to businesses they interact with, e.g. search engine bots like Googlebot, Bingbot or bots that operate on social media platforms like Facebook Bot.
Bad bots - bots which are designed to perform malicious actions, ultimately hurting businesses, e.g. credential stuffing bots, third-party scraping bots, spam bots and sneakerbots.
Bot Management - blocking Continue reading
AWS Networking 101
There was an obvious invisible elephant in the virtual Cloud Field Day 7 (CFD7v) event I attended in late April 2020. Most everyone was talking about AWS, how their stuff runs on AWS, how it integrates with AWS, or how it will help others leapfrog AWS (yeah, sure…).
Although you REALLY SHOULD watch my AWS Networking webinar (or something equivalent) to understand what problems vendors like VMWare or Pensando are facing or solving, I’m pretty sure a lot of people think they can get away with CliffsNotes version of it, so here they are ;)
Close to the Edge
PE-CE routing in MPLS L3VPN is an important topic which confuses a lot of people. Thanks to EVPN, it is now used not only in ISP but also DC networks.

Fundamentals of PE-CE routing
Usually either static routing or eBGP …
AWS Redirect URL with Route 53 and S3
I previously hosted my domains with GoDaddy. In their service it was pretty trivial to redirect a URL from one domain to another. I own the domain bradleysearle.com and I redirect it to https://codingpackets.com/about. The process to do this is not as simple with AWS so in this post I...AWS Redirect URL with Route 53 and S3
How to redirect a URL using AWS Route 53 and S3.Nvidia, Digital Realty Team Up on Enterprise AI
The new Data Hub product gives enterprises access to Nvidia’s AI infrastructure inside Digital...
Daily Roundup: Nutanix Furloughs CA Workforce
Nutanix furloughed 25% of its workforce; IBM targeted 5G and edge deployments; and Microsoft Azure...
Oracle Claims It Will Beat Salesforce at Cloud CRM
Much of that poise relies on the success of Oracle’s Gen 2 Cloud, a bare metal framework that it...
NVIDIA, Mellanox, and Cumulus
Recent press releases, Riding a Cloud: NVIDIA Acquires Network-Software Trailblazer Cumulus and NVIDIA Completes Acquisition of Mellanox, Creating Major Force Driving Next-Gen Data Centers, describe NVIDIA's moves to provide high speed data center networks to connect compute clusters that use of their GPUs to accelerate big data workloads, including: deep learning, climate modeling, animation, data visualization, physics, molecular dynamics etc.Real-time visibility into compute, network, and GPU infrastructure is required manage and optimize the unified infrastructure. This article explores how the industry standard sFlow technology supported by all three vendors can deliver comprehensive visibility.
Cumulus Linux simplifies operations, providing the same operating system, Linux, that runs on the servers. Cumulus Networks and Mellanox have a long history of working with the Linux community to integrate support for switches. The latest Linux kernels now include native support for network ASICs, seamlessly integrating with standard Linux routing (FRR, Quagga, Bird, etc), configuration (Puppet, Chef, Ansible, etc) and monitoring (collectd, netstat, top, etc) tools.
Linux 4.11 kernel extends packet sampling support describes enhancements to the Linux kernel to support industry standard sFlow instrumentation in network ASICs. Cumulus Linux and Mellanox both support the new Linux APIs. Cumulus Linux uses the open source Continue reading
Midrange All-Flash Storage Market, Meet Dell EMC PowerStore
The new storage systems come with built-in vSphere integration enabling VMware virtualized...
Coalition Forms to Address Open RAN Policies
The Open RAN Policy Coalition has support from seven operators and 24 vendors, though it's...
HPE’s Ungaro On Delivering Exascale For The Masses
When Hewlett Packard Enterprise finally closed on its $1.3 billion acquisition of supercomputer maker Cray in September, it was just over a month after the US Department of Energy announced Cray had completed a sweep in the country’s initial push into the exascale computing era. …
HPE’s Ungaro On Delivering Exascale For The Masses was written by Jeffrey Burt at The Next Platform.
Microsoft Azure Sentinel Powers Open Systems’ Threat Detection
Open Systems’ customers liked the Sentinel technology, but wanted the threat detection and...
How to Build and Test Your Docker Images in the Cloud with Docker Hub
Part 2 in the series on Using Docker Desktop and Docker Hub Together
Introduction
In part 1 of this series, we took a look at installing Docker Desktop, building images, configuring our builds to use build arguments, running our application in containers, and finally, we took a look at how Docker Compose helps in this process.
In this article, we’ll walk through deploying our code to the cloud, how to use Docker Hub to build our images when we push to GitHub and how to use Docker Hub to automate running tests.
Docker Hub
Docker Hub is the easiest way to create, manage, and ship your team’s images to your cloud environments whether on-premises or into a public cloud.
This first thing you will want to do is create a Docker ID, if you do not already have one, and log in to Hub.
Creating Repositories
Once you’re logged in, let’s create a couple of repos where we will push our images to.
Click on “Repositories” in the main navigation bar and then click the “Create Repository” button at the top of the screen.
You should now see the “Create Repository” screen.
You can create repositories for your Continue reading
