Kubernetes Opportunities, Challenges Escalated in 2019
The past year was highlighted by ongoing security and commercialization challenges around business...
The past year was highlighted by ongoing security and commercialization challenges around business...
When I studied for my CCDE, I had the good fortune of receiving mentoring from Russ White. Something he taught me, that I really took to heart, is that in every design and choice you make, there is a tradeoff.
If you haven’t found the tradeoff, you haven’t looked hard enough.
From a SD-WAN perspective, in selecting your vendor of choice, what does that mean?
SD-WAN vendors, for a loose definition of SD-WAN, come mainly from three different camps:
There are also vendors that were born in the SD-WAN era and have no previous background.
Cisco of course, through the acquisition of Viptela, bought a company that was very strong in routing, control- and data plane design. A solution designed by Architects/Engineers with profound experience of large scale networking, from large enterprises and service providers. Viptela was born in the SD-WAN era, with no legacy platforms or products to take into consideration. With the background of Viptela, this means that this is a SD-WAN product where the main strength is on routing, separation of control- and data plane, and the flexibility of the product. Other vendors with the same background will also likely Continue reading
One great thing about software defined radio is that you can become less blind to the invisible world of radio waves that’s all around us. One simple thing is to do a survey of the spectrum, to see what parts are busy.
More practically you can also use this to find which Wifi channels are least busy, so that you can get optimal performance on your network. Counting the number of networks is not a good indicator, since one network may be completely unused, while another is used 24/7 to stream Netflix. And some networks are hidden anyway, making them no more secure, but more annoying.
[GNU Radio][gnuradio] has a bunch of building blocks for some interactive peeking at spectrums, but there’s still some assembly required in order to make actually useful things.
To do a survey I used a USRP B200 with a [broadband spiral antenna. If you’re only interested in the Wifi spectrum then a 2.4/5GHz antenna is a better choice.
You can probably use a cheaper SDR, but you need to make sure it sends frequency tag updates in GNU Radio, so the block knows which frequency is tuned, as it moves across the spectrum.
This is a special holiday episode of Day Two Cloud with guest Kelsey Hightower, a Kubernetes evangelist and contributor. We discuss the current state of Kubernetes and the future for this orchestration platform, including how it will address networking, should you get certified, and will Kubernetes eventually fade into the background as hidden infrastructure you don't have to think about so much.
The post Day Two Cloud 029: Kubernetes Needs To Disappear appeared first on Packet Pushers.
Dear friend,
The year 2019 is almost over and it is a time to sincerely thank you for the time you spend reading this blog, for all your questions, ideas and suggestions. All these things gives us inspiration to continue blogging about new things for you, dear friend!
We wish you jolly time over the holidays period with your families and friends. We wish you to achieve all your professional and personal goals in 2020! Let the year be successful for you and your loved ones!
Merry Christmas and Happy New 2020 Year!
BR, Anton
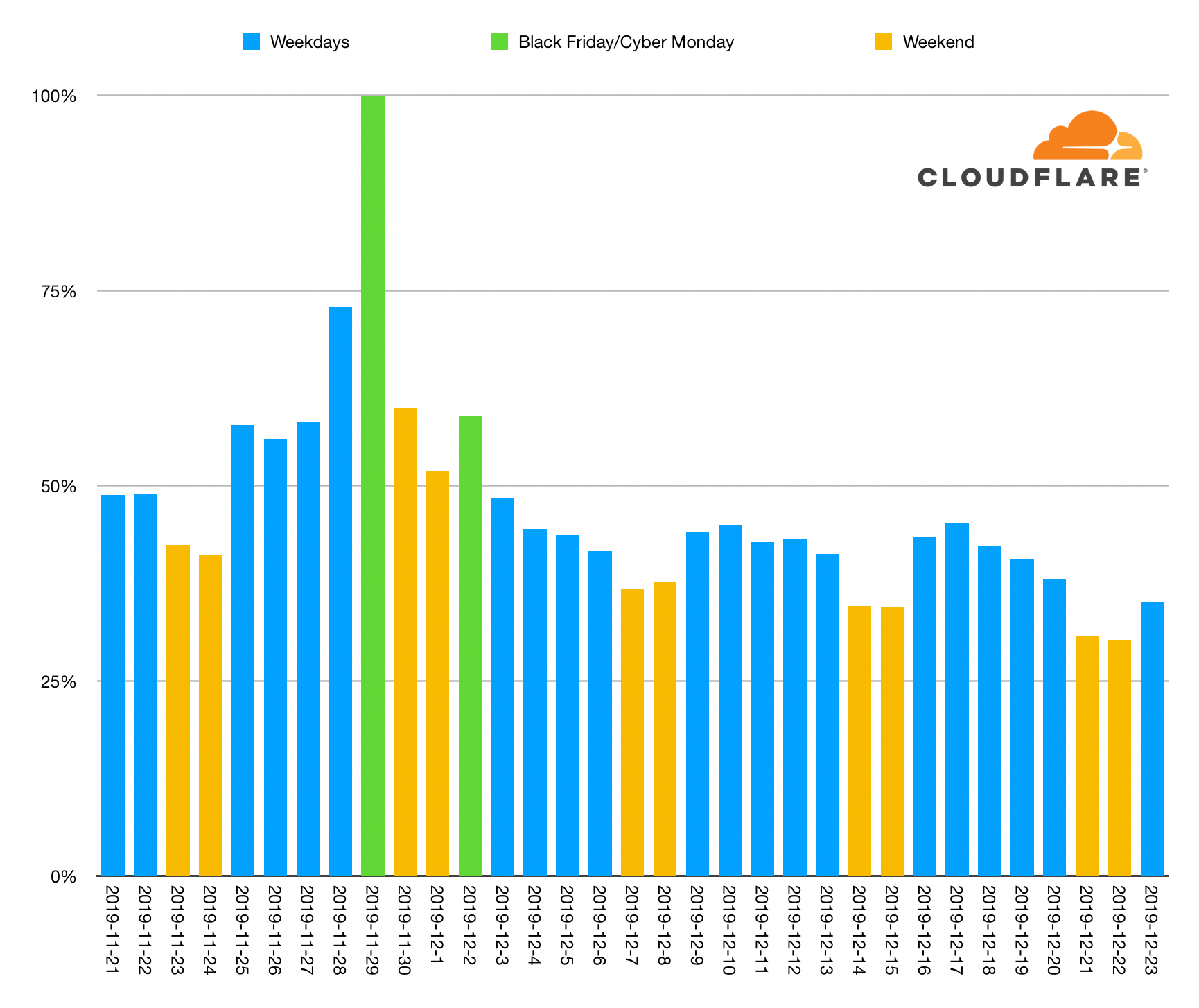
What’s the biggest day of the holiday season for holiday shopping? Black Friday, the day after US Thanksgiving, has been embraced globally as the day retail stores announce their sales. But it was believed that the following Monday, dubbed “Cyber Monday,” may be even bigger. Or, with the explosion of reliable 2-day and even 1-day shipping, maybe another day closer to Christmas has taken the crown. At Cloudflare, we aimed to answer this question for the 2019 holiday shopping season.
Black Friday was the biggest online shopping day but the second biggest wasn't Cyber Monday... it was Thanksgiving Day itself (the day before Black Friday!). Cyber Monday was the fourth biggest day.
Here's a look at checkout events seen across Cloudflare's network since before Thanksgiving in the US.
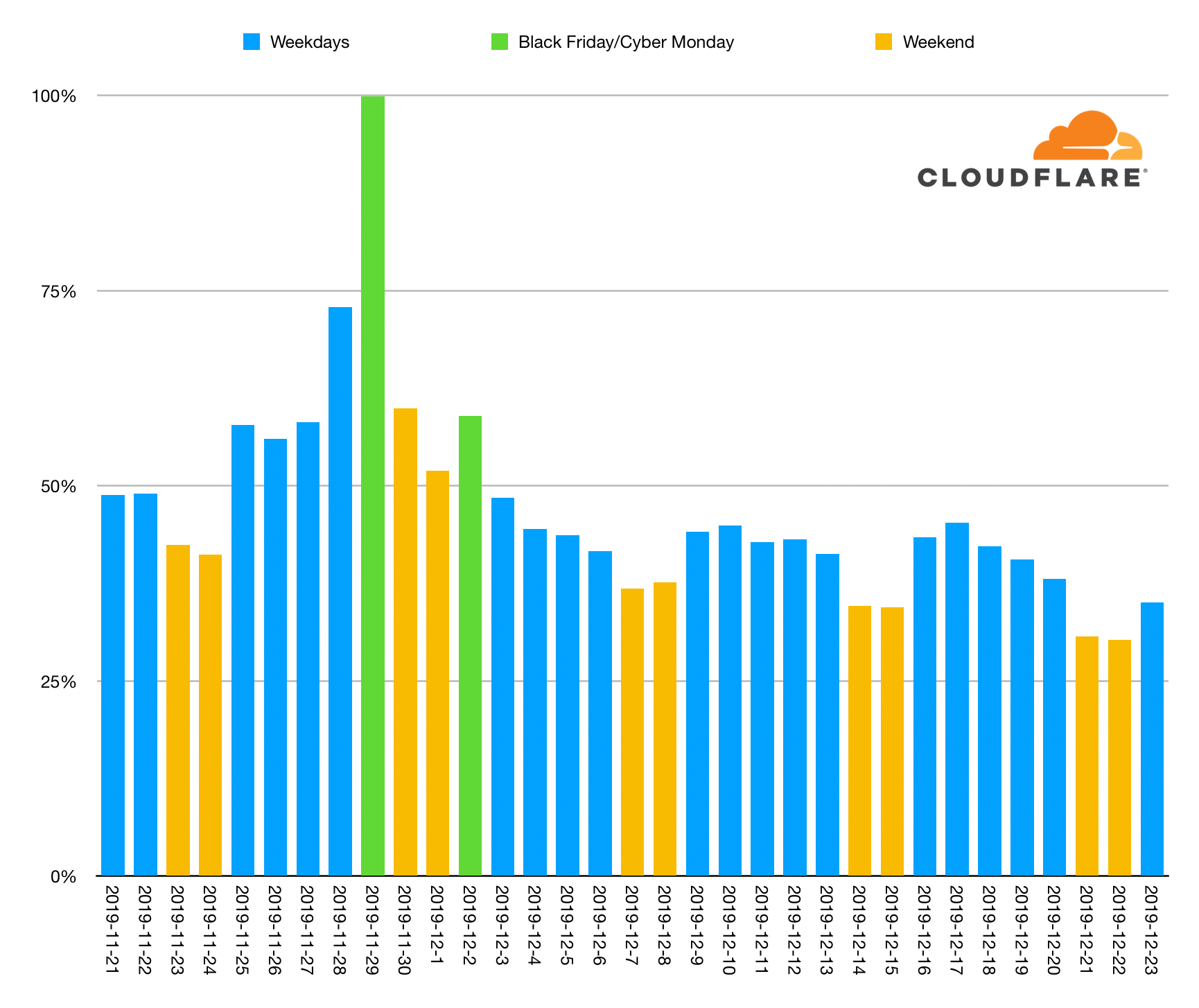
The weekends are shown in yellow and Black Friday and Cyber Monday are shown in green. You can see that checkouts ramped up during Thanksgiving week and then continued through the weekend into Cyber Monday.
Black Friday had twice the number of checkouts as the preceding Friday and the entire Thanksgiving week dominates. Post-Cyber Monday, no day reached 50% of the Continue reading

In 2018, we began collaborating with the Philippines’ Department of Information and Communications Technology (DICT) to develop the country’s National ICT Ecosystem Framework (NICTEF), a successor to the Philippine Digital Strategy for 2011-2016.
The DICT, like all Philippine government agencies, is mandated by law to hold open consultations as a means of improving transparency and encouraging public involvement in the policymaking process. But it took this initiative further by ensuring that NICTEF is fully reflective of the needs and priorities of different sectors across the archipelago. For one year, the DICT led capacity building workshops, focus group discussions, writeshops, an online public survey, and regional consultations in each of the country’s major island groups, localizing the multistakeholder approach in the process to reach important and difficult decisions.
The NICTEF is now an authoritative guide on the Philippines’ digital ecosystem, and a roadmap to harmonize and coordinate the country’s ICT programs. The multistakeholder process adopted by NICTEF has been documented in a case study, offering other countries in the region a reference in developing public policies that are forward-thinking, inclusive, and suited to the needs of a steadily-interconnected world.
Below are some of our key takeaways from the process:
Develop Continue reading
Billions of dollars changed hands this year as industry giants attempted to bolster their positions...
Hello my friend,
The Christmas and New Year is coming, so it is typically the time to think about the future and plan ahead. And today we look into future by reviewing the new network operation system deployed in the data centres hosting Microsoft Azure clouds. This operation system is called SONiC: Software for Open Networking in the Cloud.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
If you even more interested in your future, join our network automation training we start on 18th and 22nd of January, where we cover the details of the data modelling, NETCONF/YANG, REST API, Python and Ansible in the multivendor environment with Cisco, Nokia, Arista and Cumulus Linux as network functions.
Special thanks for Avi Alkobi from Mellanox for providing me the Mellanox SN2010 for tests and initial documentation for Microsoft Azure SONiC setup.
Everyone talks about the clouds. You can hear about public clouds, private clouds, hybrid clouds, clouds interconnection Continue reading
5G is available from sea to shining sea — with many pockets of 4G LTE remaining in between.

As this decade comes to a close, we are rounding up some of your favorite content from 2019. Catch up on anything you missed and get ready for a lot more to come in 2020!
Brian Christner did an analysis of VMware, Docker, and Kubernetes Google Trends and the results just might surprise you. . . or maybe not.
John Lees Miller updated his 2016 Lessons from Building a Node App in Docker. Run through the updated tutorial to learn how to Dockerize your node.js apps by setting up the socket.io chat example with Docker, from scratch to production-ready.
Ajeet Singh Raina wrote nearly 30 blogs in 2019, and the most popular was 5 Minutes to Kubernetes Dashboard running on Docker Desktop for Windows 2.0.0.3. Find yourself five minutes before the end of the year to try this out yourself.
Łukasz Lach and Thomas Shaw spread holiday cheer with some seasonal docker run commands:
$ docker run -it lukaszlach/merry-christmas
docker run --rm -t tomwillfixit/hohoho
Bret Fisher hosts a weekly Docker and DevOps YouTube live show – a fun and educational way to spend an hour on Thursdays. Continue reading
The bug was initially spotted by Cisco in June 2018 and given a “critical” rating.