The Daily DDoS: Ten Days of Massive Attacks
Back in March my colleague Marek wrote about a Winter of Whopping Weekend DDoS Attacks where we were seeing 400Gbps attacks occurring mostly at the weekends. We speculated that attackers were busy with something else during the week.
This winter we've seen a new pattern, and attackers aren't taking the week off, but they do seem to be working regular hours.
 CC BY 2.0 image by Carol VanHook
CC BY 2.0 image by Carol VanHook
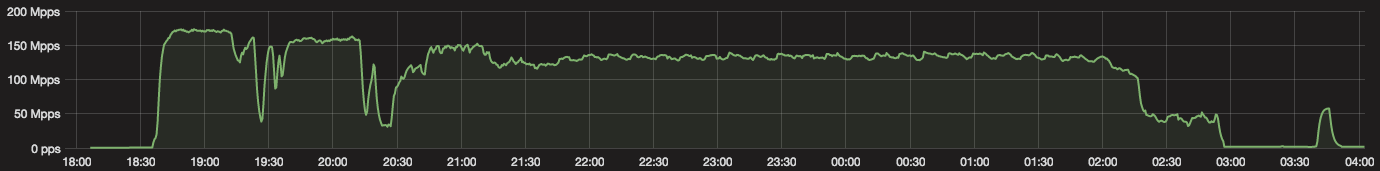
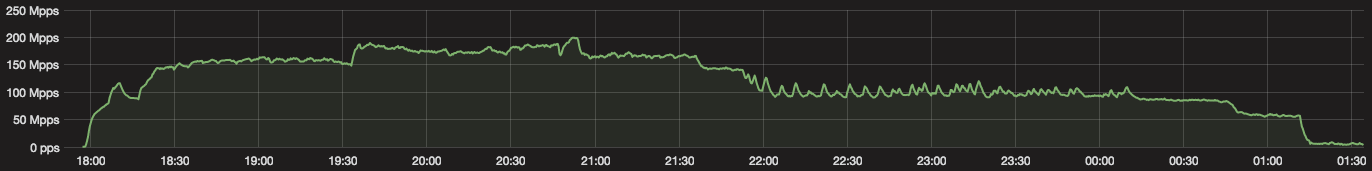
On November 23, the day before US Thanksgiving, our systems detected and mitigated an attack that peaked at 172Mpps and 400Gbps. The attack started at 1830 UTC and lasted non-stop for almost exactly 8.5 hours stopping at 0300 UTC. It felt as if an attacker 'worked' a day and then went home.
The very next day the same thing happened again (although the attack started 30 minutes earlier at 1800 UTC).
On the third day the attacker started promptly at 1800 UTC but went home a little early at around 0130 UTC. But they managed to peak the attack over 200Mpps and 480Gbps.
And the attacker just kept this up day after day. Right through Thanksgiving, Black Friday, Cyber Monday and into this week. Night after night attacks were peaking Continue reading
Packet Blast: Top Tech Blogs, Dec. 2
We collect the top expert content in the infrastructure community and fire it along the priority queue.
Your Docker Agenda for December 2016
Thank you Docker community for your amazing Global Mentor Week Events last month! In November, the community organized over 110 Docker Global Mentor Week events and more than 8,000 people enrolled in at least one of the courses for 1000+ course completions and counting! The five self-paced courses are now available for everyone free online. Check them out here!
As you gear up for the holidays, make sure to check out all the great events that are scheduled this month in Docker communities all over the world! From webinars to workshops, meetups to conference talks, check out our list of events that are coming up in December.
Official Docker Training Courses
View the full schedule of instructor led training courses here!
Introduction to Docker:
This is a two-day, on-site or classroom-based training course which introduces you to the Docker platform and takes you through installing, integrating, and running it in your working environment.
Dec 7-8: Introduction to Docker with AKRA Hamburg City, Germany
Docker Administration and Operations:
The Docker Administration and Operations course consists of both the Introduction to Docker course, followed by the Advanced Docker Topics course, held over four consecutive days.
Weekly Snapshot of Tier 1 carrier performance
The post Weekly Snapshot of Tier 1 carrier performance appeared first on Noction.
Building a L3-Only Data Center with Cumulus Linux
Dinesh Dutt was the guest speaker in the second Leaf-and-Spine Fabric Design session. After I explained how you can use ARP/ND information to build a layer-3-only data center fabric that still support IP address mobility Dinesh described the details of Cumulus Linux redistribute ARP functionality and demoed how it works in a live data center.
Juniper to Acquire Cloud Operations Startup AppFormix
 It will incorporate the technology with its Contrail platform.
It will incorporate the technology with its Contrail platform.
5G Trials and Tribulations: A Guide to Global 5G Operator Tests
 Many operators conduct technology trials in hope that the results will contribute to the 5G standard.
Many operators conduct technology trials in hope that the results will contribute to the 5G standard.
Trend Micro Offers Deep Security Service on AWS Marketplace
 This pure-play security company has been around for 28 years.
This pure-play security company has been around for 28 years.