The Bookshelf
I am a big fan of Audible for books. Every once in a while I have time and patience to read a physical book, but often times I find myself needing to do things like washing dishes, going on a long walk or drive, and Audible has made it so much easier for me to get back into “reading”. Since I started doing this, I’d like to share the books that I’ve been able to get through this way.LF Edge Sharpens Its Focus With Baetyl, Fledge
China's Baidu donated the Baetyl seed code, while Dianomic contributed Fledge.
EVPN-PIM: Anycast VTEPs
This is the second of the two part EVPN-PIM blog series exploring the feature and network deployment choices. If you missed part one, learn about BUM optimization using PIM-SM here.
Anycast VTEPs
Servers in a data-center Clos are typically dual connected to a pair of Top-of-Rack switches for redundancy purposes. These TOR switches are setup as a MLAG (Multichassis Link Aggregation) pair i.e. the server sees them as a single switch with two or more bonded links. Really there are two distinct switches with an ISL/peerlink between them syncing databases and pretending to be one.

The MLAG switches (L11, L12 in the sample setup) use a single VTEP IP address i.e. appear as an anycast-VTEP or virtual-VTEP.
Additional procedures involved in EVPN-PIM with anycast VTEPs are discussed in this blog.
EVPN-PIM in a MLAG setup vs. PIM-MLAG
Friend: “So you are working on PIM-MLAG?”
Me: “No, I am implementing EVPN-PIM in a MLAG setup”
Friend: “Yup, same difference”
Me: “No, it is not!”
Friend: “OK, OK, so you are implementing PIM-EVPN with MLAG?”
Me: “Yes!”
Friend: “i.e. PIM-MLAG?”
Me: “Well, now that you put it like that….……..NO, I AM NOT!! Continue reading
Oracle Slashes Data Cloud Workforce
Oracle reportedly cut 10% to 15% of its Data Cloud business unit this week amid its ongoing...
Why Every Size IT Team Should Strive to Implement a Software-Defined Data Center (SDDC)
Part One of a Five-Part Series on Software-Defined Data Centers in a Multi-Cloud World Business of all shapes and sizes...Alibaba Unsheaths AI Chip, Goes Head-to-Head With AWS, Google
Alibaba said it developed a new chip for AI inference that speeds up machine learning tasks on its...
CloudGenix SD-WAN Arrives On Hypercore Networks
In a win for CloudGenix, Hypercore Networks today announced a partnership with the SD-WAN vendor to...
Follow the Yellowbrick Data Road to Cloud Warehousing and DR
With the addition of its cloud offerings, Yellowbrick offers enterprise customers a platform to run...
Qualcomm Waxes 5G Vision, Downplays Early Challenges
Qualcomm showcased its long history of innovation in wireless technology and contends that it’s...
Network Outages and Idiots With Guns

As told to me:
The post Network Outages and Idiots With Guns appeared first on EtherealMind.
Network Neighborhood: Corporate Communications And The IT Community With Dana Iskoldski
On today's Network Neighborhood we talk with Dana Iskoldski, Corporate Communications Manager at BlueCat Networks. We discuss the role of corporate comms in tech, how the position straddles marketing and community engagement, and how Dana grapples with the natural skepticism of engineers.
The post Network Neighborhood: Corporate Communications And The IT Community With Dana Iskoldski appeared first on Packet Pushers.
Host, Docker, Swarm and Kubernetes monitoring
The open source Host sFlow agent incorporates technologies that address the challenges of microservice monitoring; leveraging recent enhancements to Berkeley Packet Filter (BPF) in the Linux kernel to randomly sample packets, and Asynchronous Docker metrics to track rapidly changing workloads. The continuous stream of real-time telemetry from all compute nodes, transported using the industry standard sFlow protocol, provides comprehensive real-time cluster-wide visibility into all services and the traffic flowing between them.The Host sFlow agent is available as pre-packaged rpm/deb files that can be downloaded and installed on each node in a cluster.
sflow {
collector { ip=10.0.0.70 }
docker { }
pcap { dev=docker0 }
pcap { dev=docker_gwbridge }
}The above /etc/hsflowd.conf file, see Configuring Host sFlow for Linux via /etc/hsflowd.conf, enables the docker {} and pcap {} modules for detailed visibility into container metrics and network traffic flows, and streams telemetry to an sFlow collector (10.0.0.70). The configuration is the same for every node making it simple to install and configure Host sFlow on all nodes using orchestration software such as Puppet, Chef, Ansible, etc.The agent is also available as the pre-build sflow/host-sflow image, Continue reading
Empowering More Gretas: Introducing the 2019 IGF Youth Ambassadors

When 16-year-old Swedish environmental activist Greta Thunberg burst onto the global scene a few months ago, people underestimated the power this young girl would have to raise awareness and rally the world around climate change. Today, she has become a fearless advocate, boldly speaking out and holding politicians to account for their lack of action on the climate crisis. We need more Gretas.
And they’re out there.
We’re proud to introduce 30 young changemakers who make up the 2019 cohort of the Internet Society’s IGF Youth Ambassadors Program. The group is made up of 15 women and 15 men from 21 countries. This cadre of young leaders are working on many of the pressing issues affecting the Internet globally.
In November, they’ll bring their drive for change to Berlin, Germany, to take part in the Internet Governance Forum (IGF). This is an annual multistakeholder forum for inclusive policy dialogue on shared principles, procedures, and programs that shape the evolution and use of the Internet. Although not an official decision-making body, the IGF remains an important forum. Many of the world’s experts in and advocates for the Internet gather there for discussion, networking, research sharing, and best practices from around the Continue reading
WARP is here (sorry it took so long)


Today, after a longer than expected wait, we're opening WARP and WARP Plus to the general public. If you haven’t heard about it yet, WARP is a mobile app designed for everyone which uses our global network to secure all of your phone’s Internet traffic.
We announced WARP on April 1 of this year and expected to roll it out over the next few months at a fairly steady clip and get it released to everyone who wanted to use it by July. That didn’t happen. It turned out that building a next generation service to secure consumer mobile connections without slowing them down or burning battery was… harder than we originally thought.
Before today, there were approximately two million people on the waitlist to try WARP. That demand blew us away. It also embarrassed us. The common refrain is consumers don’t care about their security and privacy, but the attention WARP got proved to us how wrong that assumption actually is.
This post is an explanation of why releasing WARP took so long, what we've learned along the way, and an apology for those who have been eagerly waiting. It also talks briefly about the rationale for why we Continue reading
The Technical Challenges of Building Cloudflare WARP
If you have seen our other post you know that we released WARP to the last members of our waiting list today. With WARP our goal was to secure and improve the connection between your mobile devices and the Internet. Along the way we ran into problems with phone and operating system versions, diverse networks, and our own infrastructure, all while working to meet the pent up demand of a waiting list nearly two million people long.
To understand all these problems and how we solved them we first need to give you some background on how the Cloudflare network works:
How Our Network Works
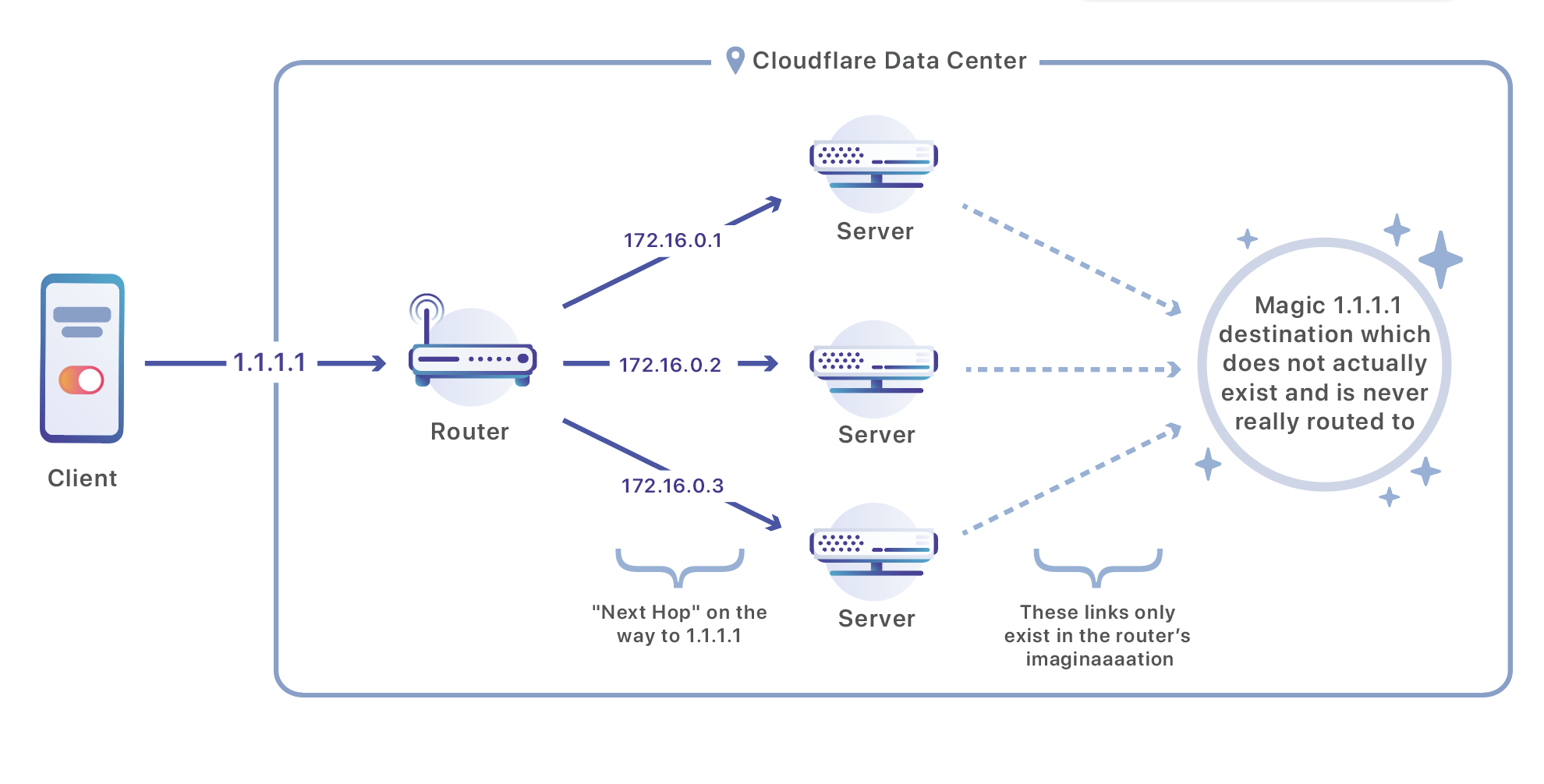
The Cloudflare network is composed of data centers located in 194 cities and in more than 90 countries. Every Cloudflare data center is composed of many servers that receive a continual flood of requests and has to distribute those requests between the servers that handle them. We use a set of routers to perform that operation:
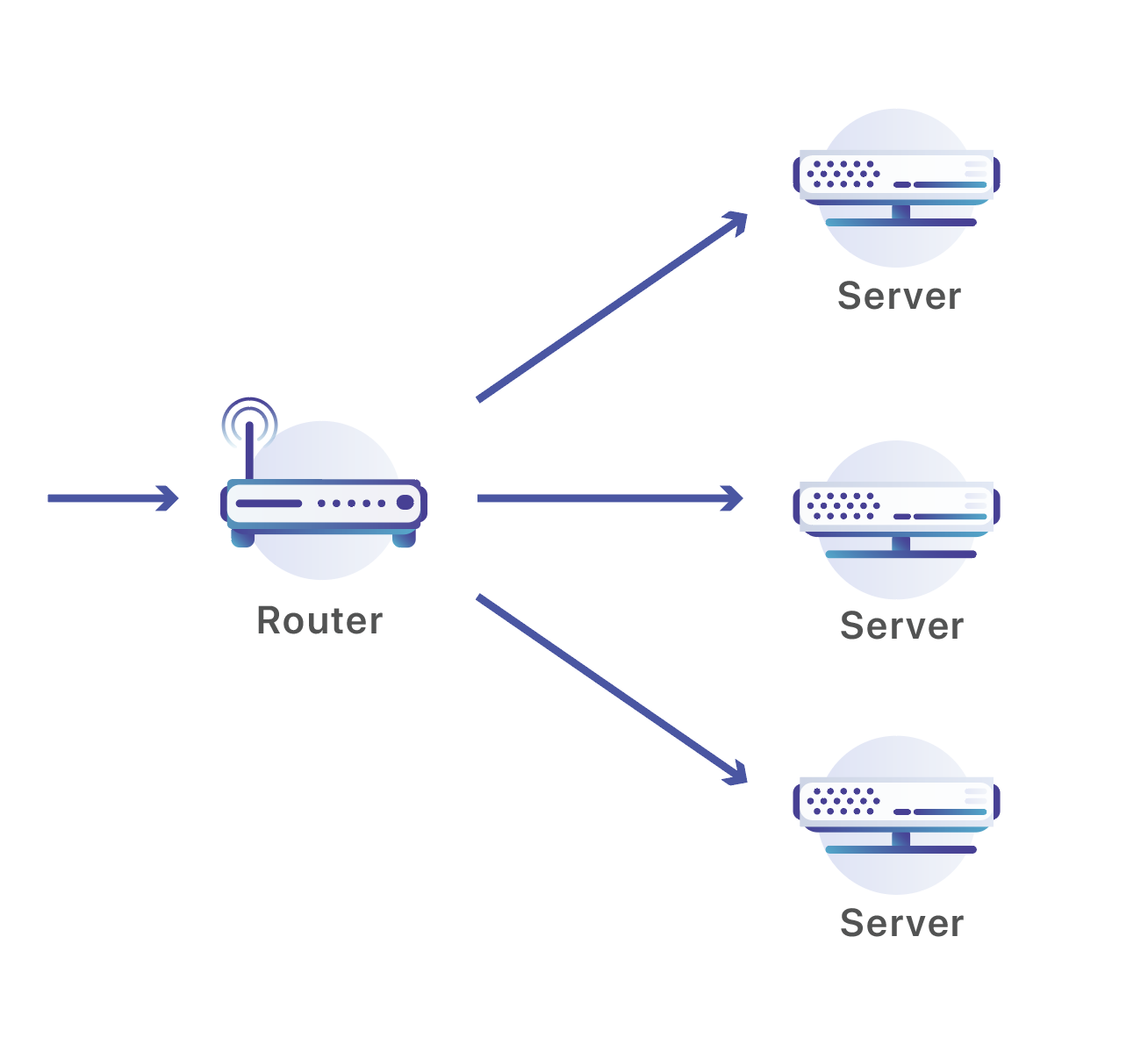
Our routers listen on Anycast IP addresses which are advertised over the public Internet. If you have a site on Cloudflare, your site is available via two of these addresses. In this case, I am doing a DNS query Continue reading
Testing Open vSwitch-DPDK

In a previous tutorial we have built DPDK 18.11.2 and Open vSwitch 2.11.1 on Linux Debian 10.1 VM (buster). We have created a L3 Open vSwitch QEMU appliance that we will use to compare performance of Open vSwitch with enabled/disabled DPDK. A network topology is depicted on the Picture 1.
The lab is created as GNS3 project which consists of a single Debian Open vSwitch appliance. Two Linux Core 6.3 hosts PC1 and PC2 are connected to the switchports Ethernet0 and Ethernet1, respectively. Firstly, we are going to bind the both ports to DPDK-compatible driver and create a bridge with the DPDK ports attached to the bridge. As a last step, we will measure maximum achievable bandwidth with iPerf3 tool. The host PC1 will be be acting as a iPerf3 client connecting to the iPerf3 server running on the host PC2.
Note: Open vSwitch 2.11.1 appliance built on Debian 10 buster and DPDK 18.11.2 is available in Download-> Appliance Section. The Linux Core 6.3 image is available there, as well.

Picture 1 - Debian Open vSwitch/DPSK Appliance with Connected Host
1. GNS3 Configuration
Check GNS3 settings for Open Continue reading
Debian Open vSwitch Appliance with DPDK
Open vSwitch is a production quality, multilayer virtual switch licensed under the open source Apache 2.0 license. It is designed to enable massive network automation through programmatic extension, while still supporting standard management interfaces and protocols (e.g. NetFlow, sFlow, IPFIX, RSPAN, CLI, LACP, 802.1ag).
DPDK is the Data Plane Development Kit that consists of libraries to accelerate packet processing workloads running on a wide variety of CPU architectures.
Note: Open vSwitch images are customized with my after install script and they are ready for use in GNS3.
Username is debian with the password debian.
Debian Linux 10 (buster) VMDK Appliance with DPDK 18.11.2 and Open vSwitch 2.11.1 [997,2MB]
https://drive.google.com/file/d/1ZuVVP2POUnFjySt0YpFwPeSG5Rtw_6Gj/view?usp=sharing
Juniper JNCIE-CLOUD Announced
I know we all have our cloudy day (some of us more than others) yet if you are a cloud …
The post Juniper JNCIE-CLOUD Announced appeared first on Fryguy's Blog.
