Kubernetes Kills Containership’s Cruise
The company's founder and CTO explained that it was unable to adequately monetize its operations in...
Rubrik, NetApp Catapult Data Management to the Cloud
The partnership aims to simplify data management on cloud-scale architectures through policy-based...
Full Stack Journey 034: Choosing Your Own Adventure
If you've ever thought about working for yourself, catch this episode of the Full Stack Journey. Guest Ned Bellavance discusses his decision to leave a job as an IT consultant to become an independent content creator of tech training material. Ned shares real-world insights into his experience along with practical takeaways.
The post Full Stack Journey 034: Choosing Your Own Adventure appeared first on Packet Pushers.
Full Stack Journey 034: Choosing Your Own Adventure
If you've ever thought about working for yourself, catch this episode of the Full Stack Journey. Guest Ned Bellavance discusses his decision to leave a job as an IT consultant to become an independent content creator of tech training material. Ned shares real-world insights into his experience along with practical takeaways.NSX-T 2.5 What is new for Kubernetes
NSX-T 2.5 was released last week and now we also have the new NSX Container Plugin 2.5 on the market…. VMworld US 2019 is also over with announcements of huge innovations like NSX Intelligence, enhanced security, and improved operability and observability. You can find more information here! I would like to take this opportunity to specifically highlight the new containers capabilities we had been working on for this release.
What is new in NSX Container plugin (NCP)
Simplified UI (Policy API) support
With the introduction of the new intent-based Policy API and corresponding Simplified UI, administrators have seen that objects created by NCP for Kubernetes are not visible in the new UI. Instead they had to go to the Advanced Networking & Security tab that corresponds to the old imperative APIs. Furthermore, all related objects like T0, IP Block, IP Pool had to be created using the Advanced Networking & Security tab. I am happy to announce that from NCP 2.5+ we have a parameter in the NCP configmap (ncp.ini) policy_nsxapi that can be set to True. In that case, NCP will start calling the new intent-based API and all objects will be visible in the simplified UI. Continue reading
Aryaka’s HybridWAN Boasts Multi-Tenancy, Enhanced Firewalls
Its HybridWAN allows low-priority traffic to be routed over broadband or 4G LTE while running...
Verizon NG-PON2 Trial Hits 34 Gb/s Speed
The trial with network partner Calix used SDN to bond four multi-gig fiber optic channels.
Broadcom Targets 5G Networks, Hyperscale Security
Broadcom released a dual 400G MACSec PHY device to support increasing bandwidth demands and...
NSX-T Data Center and EUC Design Guide Release
When it comes to VMware NSX, support for VMware Horizon deployments have been a staple ask every release. NSX compliments Horizon deployments tremendously by:
- Helping to provide the networking for the Horizon components
- Identity and firewalling security for VDI and RDSH desktops
- Endpoint protection
- Load balancing
Earlier this year, NSX-T Data Center 2.4 was released which brought identity firewalling, endpoint protection, and other necessary features for customers to consume equivalent to NSX Data Center for vSphere. The release of NSX-T Data Center 2.5 takes those features and provides even further scale enhancements to support small, medium, and the largest Horizon deployments.
NSX-T Data Center and EUC Design Guide
The NSX-T and EUC Design Guide takes information provided in the VMware Horizon Reference Architecture and the VMware NSX-T Reference Design Guide, and brings the two platforms together into a single solution.
Use Cases and What’s Covered
Let’s take a look at what all is covered and the use cases that NSX-T Data Center has for Horizon deployments:
Horizon Pod Alignment
NSX-T Data Center 2.5 supports massive scale that can cover an entire Horizon Pod scale, and more in some cases. This design guide Continue reading
How Operators Can Work With Developers to Monetize Edge
Operators and developers need to work together to bring edge uses to market and capitalize on the...
In Colombia: Latin American Summit on Community Networks

The University of Cundinamarca will host the Second Latin American Summit of Community Networks September 24-28. The event is organized by the Community Networks Special Interest Group, the Fusa Libre Collective, and the Colombia Chapter, with backing from the Internet Society.
The Summit, which will include representatives of 24 organizations that operate community networks in different countries, is meant to be a resource for the region. On the first day there will be 12 presentations that will share experiences from projects developed in countries such as Argentina, Colombia, Ecuador, and Mexico.
During the rest of the Summit, attendees will explore topics that will help strengthen their projects and enhance their development. The topics addressed in these working sessions have been defined collaboratively: gender-related issues, regulatory frameworks, local content, methodological strategies for community work, and actions for the promotion and deployment of new community networks. It could not be otherwise in a community where collaboration has stood out. In addition, attendees can share their experiences and best practices.
Although many people are familiar with the term “community networks,” their collaborative nature can be a surprise to those who are learning about how they function. Seeing people working together to plan, Continue reading
Heavy Networking 473: Synthetic Transactions, SD-WAN Readiness, And Internet Outage Autopsies With ThousandEyes (Sponsored)
ThousandEyes sponsors today's Heavy Networking for a wide-ranging episode that explores a new synthetic transaction monitoring feature, discusses why performance monitoring is essential to prepare for SD-WAN rollouts, and walks through postmortems on 2019's biggest Internet outages. Guests Alex Henthorn-Iwane and Angelique Medina join us.
The post Heavy Networking 473: Synthetic Transactions, SD-WAN Readiness, And Internet Outage Autopsies With ThousandEyes (Sponsored) appeared first on Packet Pushers.
Inside the Web Browser’s Performance API
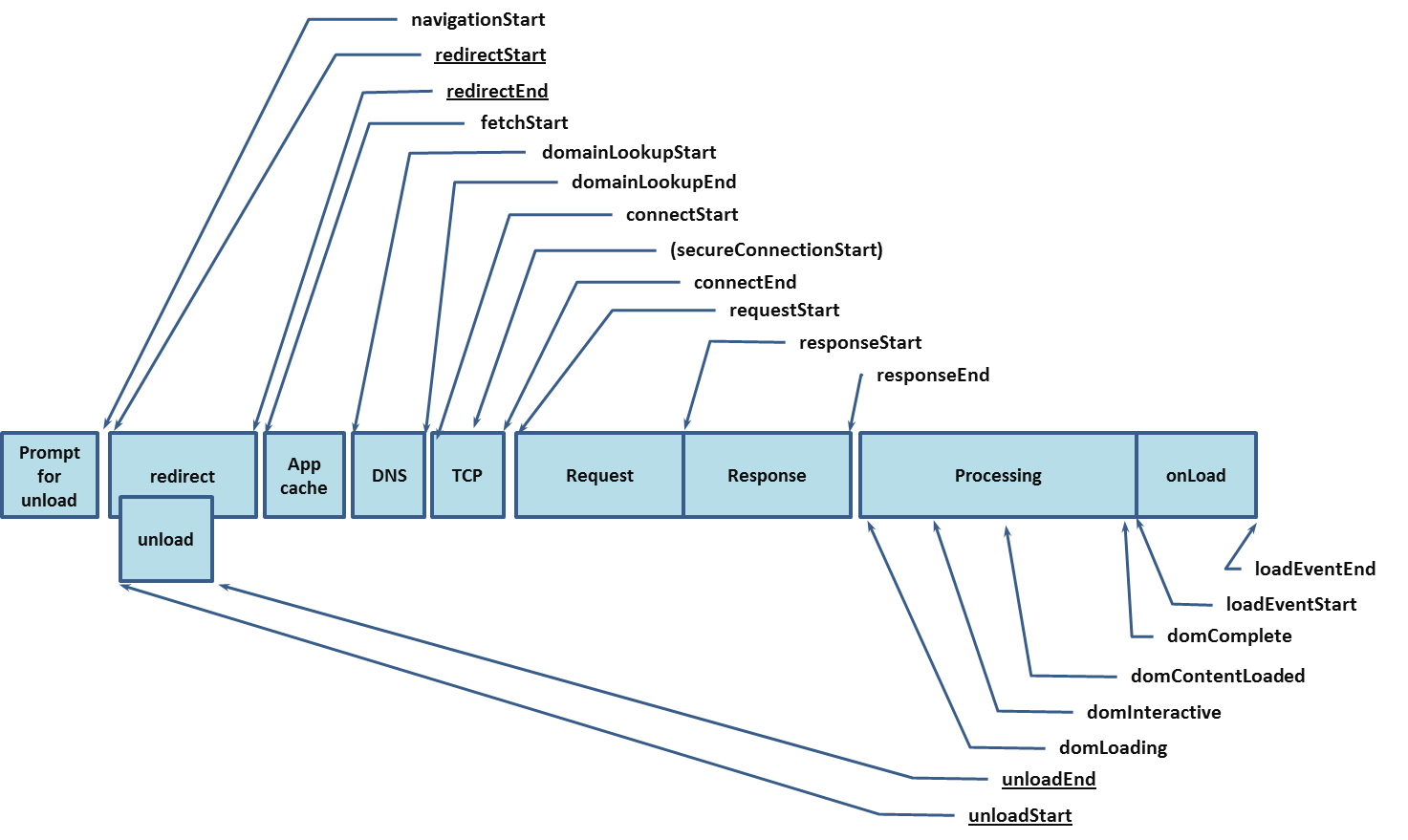
Building a beautiful, feature-rich website is easier than ever before. Not long ago, you’d have to fire up a text editor and hand-craft a lot of HTML, CSS, and JavaScript. Today, you can use WYSIWYG tools and third-party libraries that make development much simpler. The flip side of this is that it can be hard to see everything that’s going into your website — and the performance can suffer.
The good news is that modern web browsers expose lots of performance data that can help you understand how your web page performs. With the launch of Browser Insights today, we can analyze the performance from the perspective of the web browser and what the end user actually experiences. In this post, we’ll dive into how we think about performance and utilize the timing APIs in the web browser.
How web browsers measure performance
In the old days, the only way for a developer to profile performance was to intercept requests and measure the time from the beginning of the page load until the end of the load event.
Today, we can use Web APIs that are supported by modern browsers. This is part of the web standard called the Performance Continue reading
Introducing Browser Insights

Speed matters. We know that when your website or app gets faster, users have a better experience and you get more conversions and more revenue. At Cloudflare, we spend our days obsessing about speed and building new features to squeeze out as much performance as possible.
But to improve speed, you first need to measure it. That’s why we’re launching Browser Insights: a new tool that measures the performance of your website from the perspective of your users. Browser Insights lets you dive in to understand where, when, and why web pages are slow. And you can enable it today, for free, with one click.

Why did we build Browser Insights?
Let’s say you run an e-commerce site, and you want to make your conversion rates better. You’ve noticed that there’s a lot of traffic from visitors in Peru, but they have worse conversion than users in North America. Maybe you theorize that it takes a long time to load your checkout page, which causes customers to drop off before checking out. How would you verify that this is happening?
There are a few ways you could do this: you could check your server logs to look at timing Continue reading
Cisco ACI – API Calls vs JSON POST
API Calls method The fancy way of configuring Cisco ACI Fabric is by using Python script for generating API calls. Those API calls are then used to configure Cisco ACI by pushing those calls to APIC controller using POSTMAN (or similar tool). Configuration changes done this way are those that you are doing often and without much chance of making mistakes. You write a Python script and that script will take your configuration variables and generate API call that will configure the system quickly and correctly every time. The thing is that you need to take the API call example
The post Cisco ACI – API Calls vs JSON POST appeared first on How Does Internet Work.
What do I run at home?
I have decided to do a little series on “What I run at home” with regards to networking, labs, and …
The post What do I run at home? appeared first on Fryguy's Blog.
vlog. Episode 6. Closed-loop automation [LIVE]
Hello my friend,
This vlog episode I’m alone. Eh… But I have an opportunity to share with you the talk I’ve delivered an the NetLdn #6 event two weeks ago. Now you have an opportunity to watch this talk as well!

In this episode you will see the high-level description of the Data Centre Fabric Project I’ve been doing this year with the focus on the closed-loop automation using open-source tools. Additionally, you will see LIVE DEMO of the closed-loop automation as an extension to ZTP, where the full data centre fabric running Cumulus switches will be provisioned from zero to full operational state.
If you’ve recently read about Mellanox/Cumulus, the same approach perfectly fits this pair.
But it is not only about Cumulus. Any network supplier we’ve discussed (Arista, Nokia, Cisco and much more) can be provisioned in such a way, and you can find the sample templates in the GitHub repo.
Support us
Continue reading
On the Usability of OSI Layered Networking Model
Two weeks ago I replied to a battle-scar reaction to 7-layer OSI model, this time I’ll address a much more nuanced view from Russ White. Please read his article first (as always, it’s well worth reading) and when you come back we’ll focus on this claim:
The OSI Model does not accurately describe networks.
Like with any tool in your toolbox, you can view the 7-layer OSI model in a number of ways. In the case of OSI model, it can be used:
Read more ...