Marvell Pays $650M for Avera, Moves Into ASIC Biz
 The acquisition puts Marvell in a better position to increase its marketshare wired and wireless...
The acquisition puts Marvell in a better position to increase its marketshare wired and wireless...
Nokia CEO Claims Vendor Is Leading in 5G
 Rajeev Suri said Nokia now has 37 5G commercial contracts, of which 20 are with named customers.
Rajeev Suri said Nokia now has 37 5G commercial contracts, of which 20 are with named customers.
Microsoft Spearheads Service Mesh Interoperability Push
 The Service Mesh Interface platform provides a standardized API that will allow for the ability to...
The Service Mesh Interface platform provides a standardized API that will allow for the ability to...
Trio of Security Firms Rake In $193M
 Nearly $200 million has been raised by a trio of security companies this week and it’s only...
Nearly $200 million has been raised by a trio of security companies this week and it’s only...
DataStax Offers Cloud-Native Database Management Based On Apache Cassandra
 The data management company plans to release the cloud-native system this year with a monitoring...
The data management company plans to release the cloud-native system this year with a monitoring...
Building a To-Do List with Workers and KV
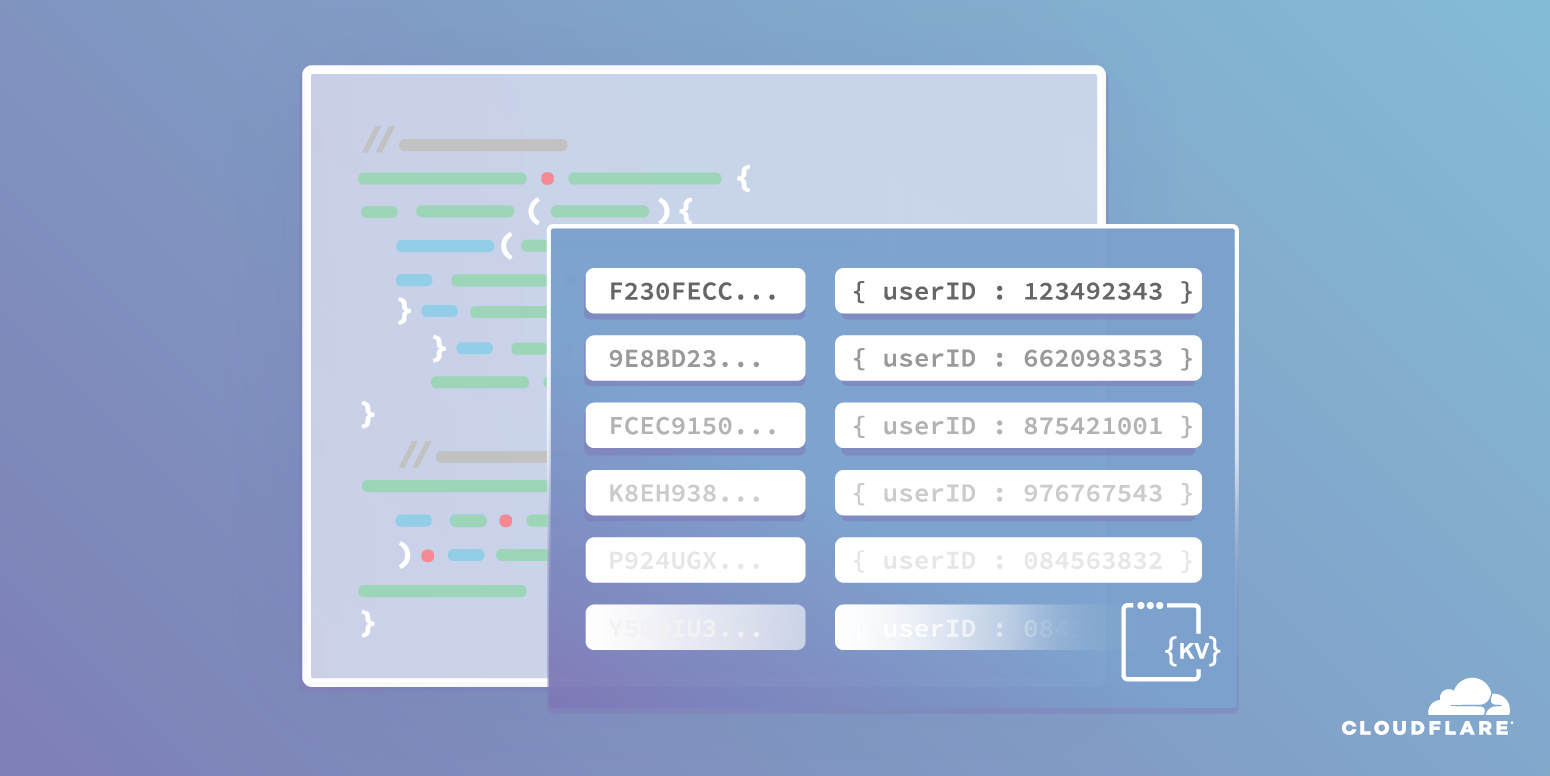
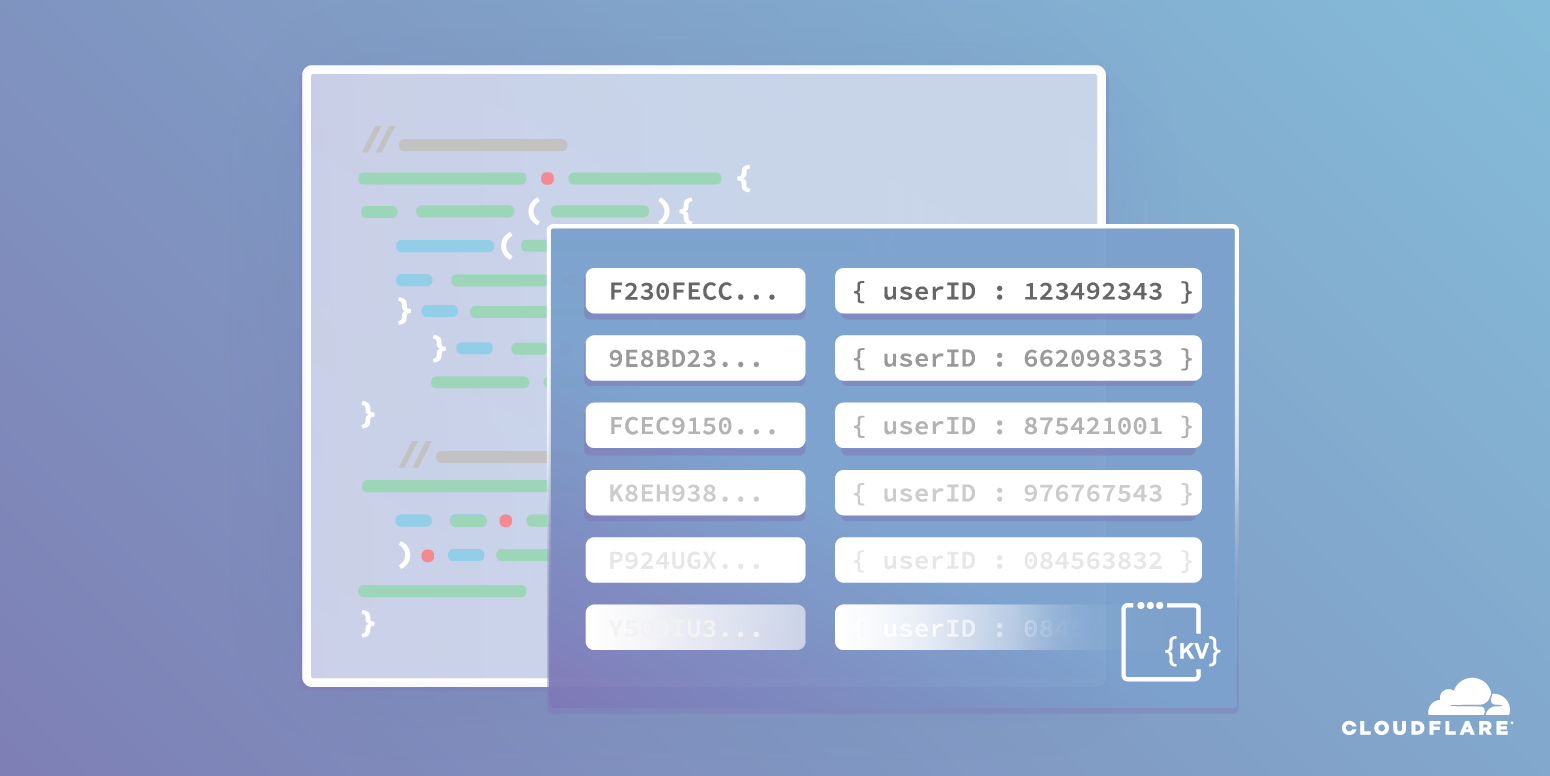
In this tutorial, we’ll build a todo list application in HTML, CSS and JavaScript, with a twist: all the data should be stored inside of the newly-launched Workers KV, and the application itself should be served directly from Cloudflare’s edge network, using Cloudflare Workers.
To start, let’s break this project down into a couple different discrete steps. In particular, it can help to focus on the constraint of working with Workers KV, as handling data is generally the most complex part of building an application:
- Build a todos data structure
- Write the todos into Workers KV
- Retrieve the todos from Workers KV
- Return an HTML page to the client, including the todos (if they exist)
- Allow creation of new todos in the UI
- Allow completion of todos in the UI
- Handle todo updates
This task order is pretty convenient, because it’s almost perfectly split into two parts: first, understanding the Cloudflare/API-level things we need to know about Workers and KV, and second, actually building up a user interface to work with the data.
Understanding Workers
In terms of implementation, a great deal of this project is centered around KV - although that may be the case, it’s useful to break Continue reading
Get ready to write — Workers KV is now in GA!
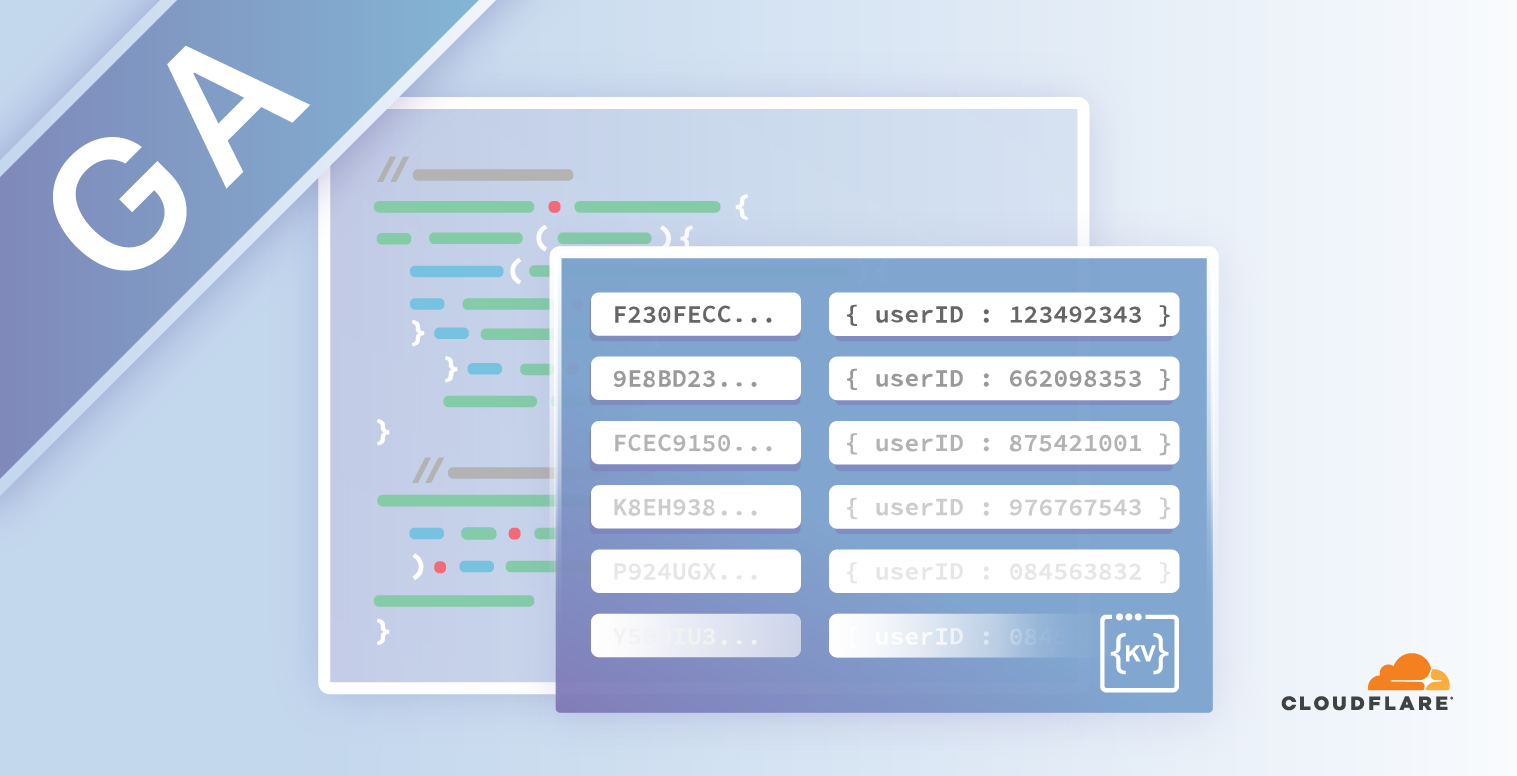
Today, we’re excited to announce Workers KV is entering general availability and is ready for production use!
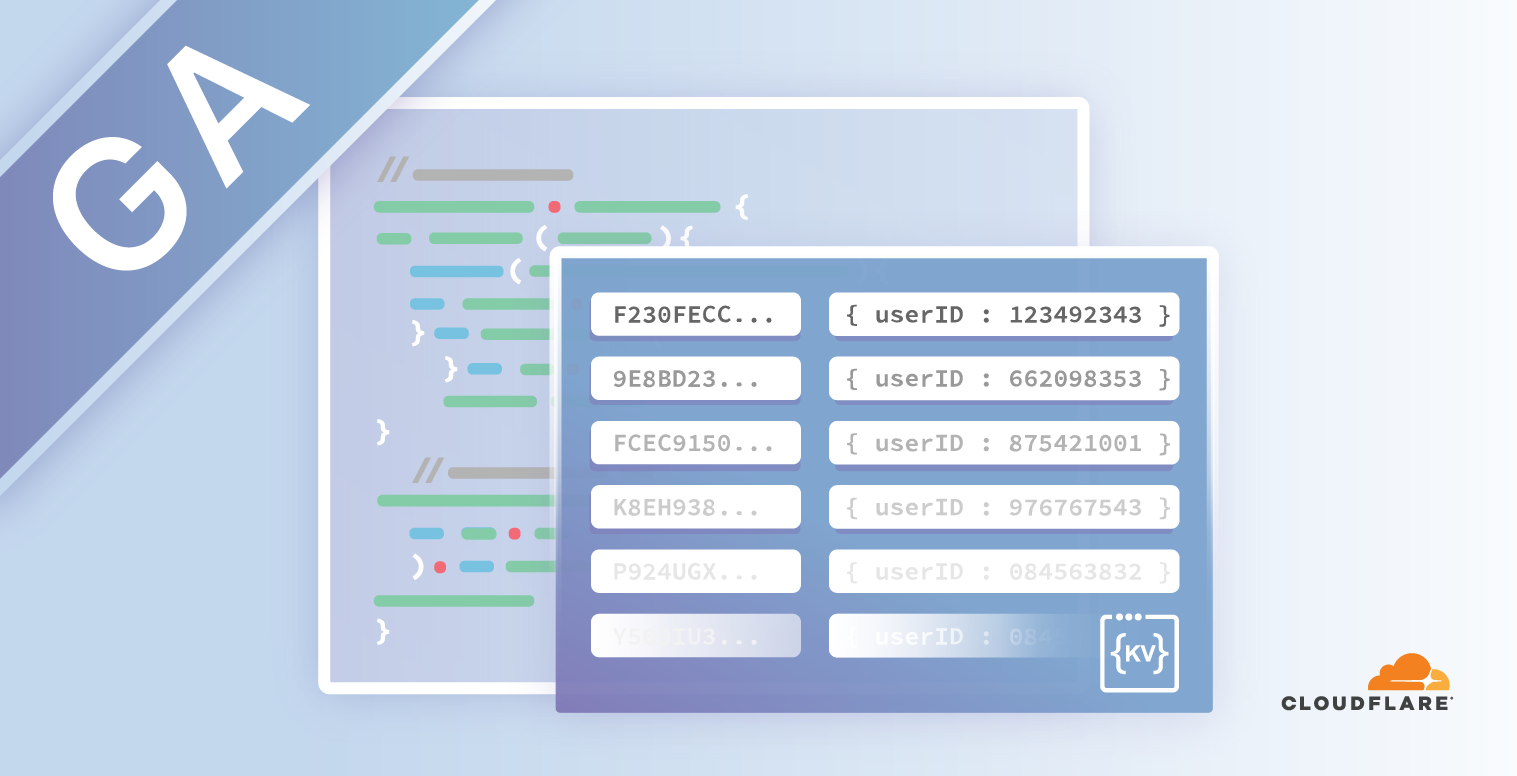
What is Workers KV?
Workers KV is a highly distributed, eventually consistent, key-value store that spans Cloudflare's global edge. It allows you to store billions of key-value pairs and read them with ultra-low latency anywhere in the world. Now you can build entire applications with the performance of a CDN static cache.
Why did we build it?
Workers is a platform that lets you run JavaScript on Cloudflare's global edge of 175+ data centers. With only a few lines of code, you can route HTTP requests, modify responses, or even create new responses without an origin server.
// A Worker that handles a single redirect,
// such a humble beginning...
addEventListener("fetch", event => {
event.respondWith(handleOneRedirect(event.request))
})
async function handleOneRedirect(request) {
let url = new URL(request.url)
let device = request.headers.get("CF-Device-Type")
// If the device is mobile, add a prefix to the hostname.
// (eg. example.com becomes mobile.example.com)
if (device === "mobile") {
url.hostname = "mobile." + url.hostname
return Response.redirect(url, 302)
}
// Otherwise, send request to the original hostname.
return await fetch(request)
Continue reading9 Things to Consider When Estimating Time
Often in my career I have to make an estimate about the so-called “level of effort” (LoE) to do a thing.
- What’s the LoE for me to do a demo for this customer?
- What’s the LoE for me to help respond to this RFP?
- What’s the LoE for me to participate in this conference?
The critical metric by which I usually have to measure the LoE is time. People, equipment, venue, materials, and location are rarely ever a limiting factor. Time is always the limiting factor because no matter the circumstance, you can’t just go and get more of it. The other factors are often elastic and can be obtained.
And oh how I suck at estimating time.
As soon as the question comes up, “What’s the LoE for…”, I immediately start to think, ok, if I am doing the work, I can do this piece and that piece, I can read up on this thing and get it done with slightly more time invested, and then yada, yada, yada… it’s done!
What I don’t account for is the human element. The unexpected. The fact that we’re all different and team members will go about their work in their Continue reading
Data Deduplication in Network Automation Data Models
One of the toughest challenges in the hands-on part of Building Network Automation Solutions online course is the create a data model describing your service exercise.
Networking engineers never had to think about data models describing their networks or services, and the first attempt often results in something that looks like simplified device configuration in YAML or JSON format.
I wrote a long article describing how you can slowly redesign your box-focused data model into a network-focused one. The first parts describing the problem and initial deduplication are already online.
9 Things to Consider When Estimating Time
Often in my career I have to make an estimate about the so-called “level of effort” (LoE) to do a thing.
- What's the LoE for me to do a demo for this customer?
- What's the LoE for me to help respond to this RFP?
- What's the LoE for me to participate in this conference?
The critical metric by which I usually have to measure the LoE is time. People, equipment, venue, materials, and location are rarely ever a limiting factor. Time is always the limiting factor because no matter the circumstance, you can't just go and get more of it. The other factors are often elastic and can be obtained.
And oh how I suck at estimating time.
As soon as the question comes up, “What's the LoE for…", I immediately start to think, ok, if I am doing the work, I can do this piece and that piece, I can read up on this thing and get it done with slightly more time invested, and then yada, yada, yada… it's done!
What I don't account for is the human element. The unexpected. The fact that we're all different and team members will go about their work in their Continue reading
One night in Beijing


As the old saying goes, good things come in pairs, 好事成双! The month of May marks a double celebration in China for our customers, partners and Cloudflare.
First and Foremost
A Beijing Customer Appreciation Cocktail was held in the heart of Beijing at Yintai Centre Xiu Rooftop Garden Bar on the 10 May 2019, an RSVP event graced by our supportive group of partners and customers.
We have been blessed with almost 10 years of strong growth at Cloudflare - sharing our belief in providing access to internet security and performance to customers of all sizes and industries. This success has been the result of collaboration between our developers, our product team as represented today by our special guest, Jen Taylor, our Global Head of Product, Business Leaders Xavier Cai, Head of China business, and Aliza Knox Head of our APAC Business, James Ball our Head of Solutions Engineers for APAC, most importantly, by the trust and faith that our partners, such as Baidu, and customers have placed in us.


Double Happiness, 双喜

On the same week, we embarked on another exciting journey in China with our grand office opening at WeWork. Beijing team consists of functions from Customer Development Continue reading
Network Break 235: Microsoft Issues Patch For Wormable Vulnerability; Intel Pursued By ZombieLoad
Today's Network Break tackles a string of vulnerabilities from Microsoft, Cisco, and Intel. We also look at a new 400G switch from Arista, an IoT security announcement from Extreme, Cisco financial results, and more tech news.
The post Network Break 235: Microsoft Issues Patch For Wormable Vulnerability; Intel Pursued By ZombieLoad appeared first on Packet Pushers.
Transparency Drives SDxCentral to Discontinue Publishing Analyst Columns and Contributor Content
After careful consideration, SDxCentral has decided it will discontinue publishing third-party...
FCC Chief Backs T-Mobile-Sprint Merger With Concessions
 FCC Chairman Ajit Pai says he backs the $26.5 billion transaction and is encouraging his fellow...
FCC Chairman Ajit Pai says he backs the $26.5 billion transaction and is encouraging his fellow...
Oracle Taps Kubernetes, Service Broker API to Automate Cloud Services
 The platform also allows users to access Oracle’s Generation 2 cloud infrastructure.
The platform also allows users to access Oracle’s Generation 2 cloud infrastructure.