Could Knative Follow Kubernetes in Shaping Cloud Foundry’s Future?
 “In less than a year, here is a new PaaS with really cool features and nearly matching what we...
“In less than a year, here is a new PaaS with really cool features and nearly matching what we...
Ansible Networking: From Science Fair Project toward Mature Product
When I started working with Ansible networking modules they had a distinct science fair feel: everything was in flux, every new version of Ansible would break my playbooks, modules would disappear from one release to next, documentation was sketchy and describing the latest development code not a shipped release.
In the meantime, code, documentation, and release/deprecation management improved dramatically:
Read more ...NFV Challenges Abound, a Leaning Beckons
 Lean NFV says "current NFV efforts are drowning in a quicksand of complexity," and proposes a...
Lean NFV says "current NFV efforts are drowning in a quicksand of complexity," and proposes a...
OpenDaylight Kept Afloat by Downstream, End-User Support
 The OpenDaylight project recently released its tenth iteration, adding support for optical...
The OpenDaylight project recently released its tenth iteration, adding support for optical...
LF Networking Releases Compliance, Verification Testing
 The Open Platform for NFV now includes virtual network function compliance testing in conjunction...
The Open Platform for NFV now includes virtual network function compliance testing in conjunction...
SKT Gets Ready to Claim Global 5G First, as Verizon Muscles In
 Both carriers are this week launching commercial 5G networks that work on 5G smartphones, but only...
Both carriers are this week launching commercial 5G networks that work on 5G smartphones, but only...
Cloud Foundry Project Eirini Inches the Group Closer to Kubernetes
 The Project Eirini work also calls into question the future of Cloud Foundry's Diego container...
The Project Eirini work also calls into question the future of Cloud Foundry's Diego container...
NetApp’s Ingo Fuchs on the Hybrid Cloud’s Best-of-Breed Approach
 In this interview, Ingo Fuchs—Chief Technologist for Cloud and DevOps at NetApp—discusses the...
In this interview, Ingo Fuchs—Chief Technologist for Cloud and DevOps at NetApp—discusses the...
Day Two Cloud 006: Dealing With The Unknown Unknowns Of Building Cloud Applications
Today's Day Two Cloud podcast looks at how one developer dealt with surprises and unexpected issues that arose as his company built CMS application on Azure, including storage problems, user identity quirks, and more.Day Two Cloud 006: Dealing With The Unknown Unknowns Of Building Cloud Applications
Today's Day Two Cloud podcast looks at how one developer dealt with surprises and unexpected issues that arose as his company built CMS application on Azure, including storage problems, user identity quirks, and more.
The post Day Two Cloud 006: Dealing With The Unknown Unknowns Of Building Cloud Applications appeared first on Packet Pushers.
CNCF Remains Focused as Cloud Native Interest Soars
 Dan Kohn, executive director of CNCF, said the group this year is targeting the broader telecom...
Dan Kohn, executive director of CNCF, said the group this year is targeting the broader telecom...
Episode 48 – BGP Peering In The Real World
Internet BGP Peering relationships are a complicated mix of competing and complimentary motivations. In this Network Collective Community Roundtable we dive in to the world of public BGP peering to discuss how it works in the real world and when it might make sense for your organization to consider getting involved as well.
We would like to thank Cumulus Networks for sponsoring this episode of Network Collective. Cumulus Networks makes networking software for the open, modern data center. It’s the only open networking software that allows you to affordably build and efficiently operate your network like the worlds largest data center operators. Cumulus Networks wants you to build something epic. Whether you’re scaling your data center network or designing the next “big thing,” you have your sights set on building something that matters. To do that, you’ll need to use the absolute best resources. If you would like to learn more about how Cumulus Networks can help you build something epic, you should check out https://cumulusnetworks.com/epic
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3. Continue reading
Enabling the Next Generation of Community Network Builders: A Report on CNXAPAC 2018 and CN Champs
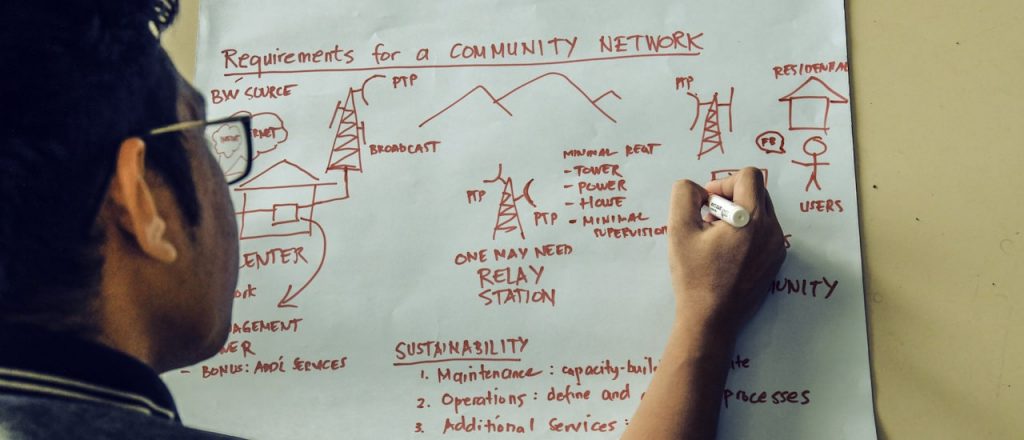
In October 2018, together with our partner Digital Empowerment Foundation (DEF), we organized the 2nd edition of CNXAPAC (Community Network eXchange Asia-Pacific) with a focus on how two sets of community operators – community radio network operators and community (Internet) network operators – could explore synergies in the work they do.
The event was kindly hosted by UNESCO at their Delhi office, and brought together over 50 participants from around the world to exchange knowledge and best practices, and see how the Internet can improve the lives of underserved and unserved communities.
In many parts of the world, community radio stations play an important role in providing information to the public – particularly in rural communities. The community radio community have expertise in setting up radio communications, as well as creating content relevant to their local communities. This presents a wonderful opportunity for this community to add Internet services to their repertoire, and 12 community radio operators from around India were brought to CNXAPAC to learn about Internet community networks, and how these could be deployed in their local communities.
The Internet Society Asia-Pacific Bureau has been working on community networks since 2010 as part of its Wireless for Continue reading




