Announcing workers.dev
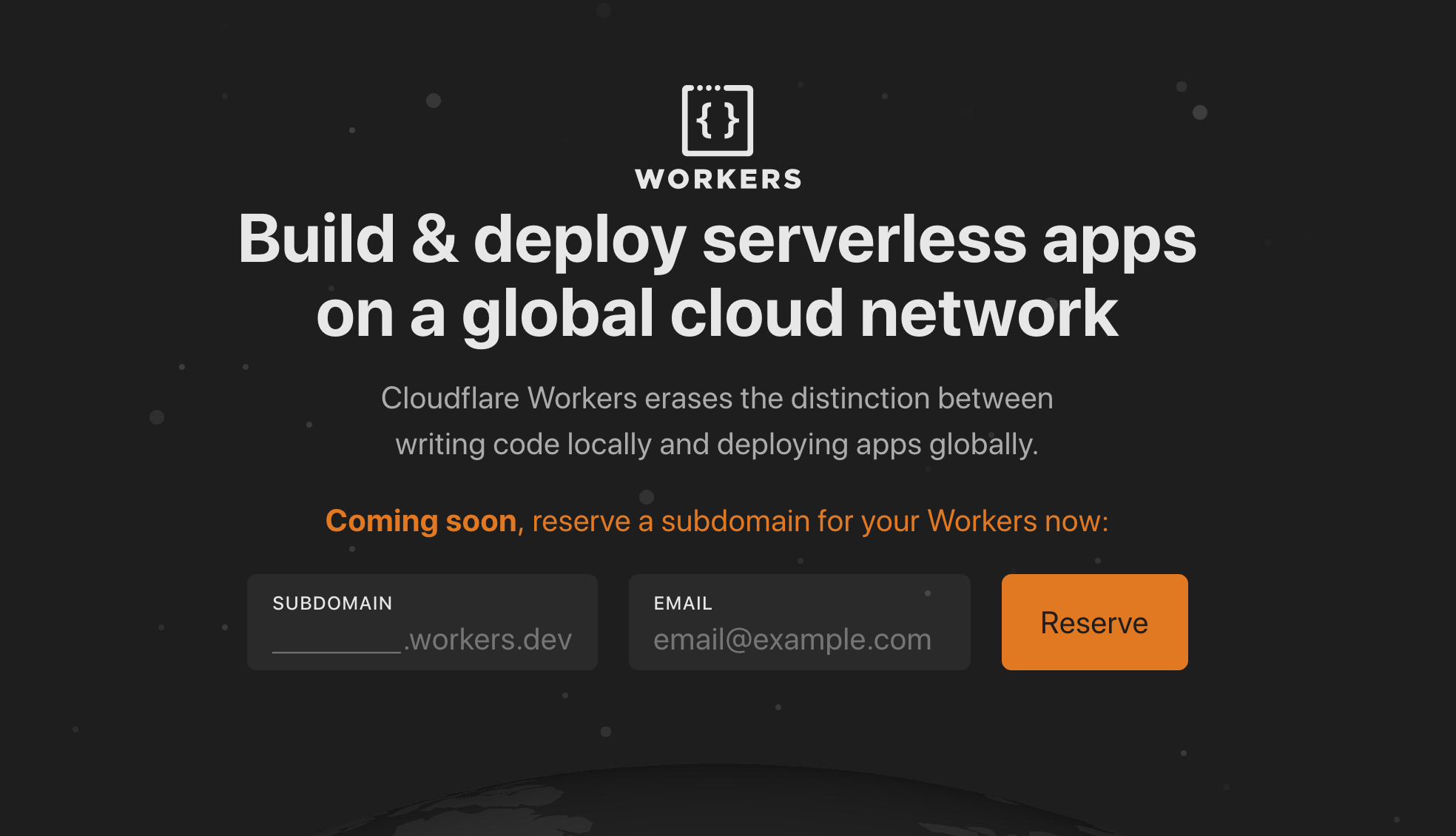
We are working really hard to allow you to deploy Workers without having a Cloudflare domain. You will soon be able to deploy your Cloudflare Workers to a subdomain-of-your-choice.workers.dev, which you can go claim now on workers.dev!
Why are we doing this?
You may have read the announcement blog post for Workers (or one of the many tutorials and guest posts), and thought “let me give this a try!”. If you’re an existing Cloudflare customer, you logged into the dashboard, and found a new icon called “Workers”, paid $5 and were on your way. If you’re not, you clicked “Sign Up”, but instead of getting to create and deploy a Worker, we asked you for your domain (if you didn’t have one, we had you register one), and move your nameservers.
Since launch, we have had tons of people who wanted to build a new serverless project from scratch or just try Workers out, but found it difficult to get started. We want to make it easier for anyone to get started building and deploying serverless applications.
How did we get here?
The way you get started on Workers today reflects our journey as a company. Continue reading
Arista BGP EVPN – Ansible Lab
In the previous two blog posts, I covered the concepts of EVPN and shared a detailed configuration example on Arista EOS. In this blog post, I’ll be covering how to automate the deployment of EVPN in a lab environment. After deployment, I want to run validations to make sure my intent is being met. Lastly, […]
The post Arista BGP EVPN – Ansible Lab appeared first on Overlaid.
HPE Partners With Samsung on 5G, Launches Telco Edge System
 The partners will jointly develop an edge-to-core vRAN product based on Samsung’s radio network...
The partners will jointly develop an edge-to-core vRAN product based on Samsung’s radio network...
DNS Privacy & IPv6 Security @ APTLD 75

The Internet Society will be actively contributing to the APTLD 75 meeting on 20-21 February 2019 in Dubai, United Arab Emirates.
Our colleague Jan Žorž will not only be presenting on DNS-over-TLS (DoT) and DNS-over-HTTPS (DoH) during the DNS Operations, Security, and Privacy session (20 February, 11.30-12.30 UTC+4), but will then be presenting on IPv6 connectivity issues during the Security in IPv6-enabled TLDs session (20 February, 14.30-15.30 UTC+4).
He’ll be in good company in what’s shaping up to be a great programme featuring a number of DNS luminaries covering technical, policy, internationalisation and data protection issues, as well as abuse handling and registry and registrar training. Other sessions of particular interest include 5G mobile networks, the implications of Alternative DNS Root Servers, and emerging trends in the DNS.
The Asia-Pacific Top-Level Domain (APTLD) Association is a non-profit organisation of ccTLD (Country Code Top-Level Domains) registries in the Asia-Pacific region that was founded in 1998. It organises two meetings each year for its members, with APTLD 75 being held in conjunction with the 6th Middle East DNS Forum.
If you’re interested in attending then you can register at http://www.aptld75.ae/reg/end.php
Further Information
Cross-Data-Center L4-7 Services with Cisco ACI
Craig Weinhold sent me his thoughts on using Cisco ACI to implement cross-data-center L4-7 services. While we both believe this is not the way to do things (because you should start with proper application architecture), you might find his insights useful if you have to deal with legacy environments that believe in Santa Claus and solving application problems with networking infrastructure.
An “easy button” for multi-DC is like the quest for the holy grail. I explain to my clients that the answer is right in front of them – local IP addressing, L3 routing, and DNS. But they refuse to accept that, draw their swords, and engage in a fruitless war against common sense. Asymmetry, stateful inspection, ingress routing, split-brain, quorums, host mobility, cache coherency, non-RFC complaint ARP, etc.
Read more ...Research: Service Fabric
Microservices architectures probably will not “take over the world,” in terms of solving every application you can throw at them, but they are becoming more widespread. Microservices and related “staged” design patterns are ideal for edge facing applications, where the edge facing services, in particular, need to scale quickly across broad geographical regions. Supporting microservices using a standard overlay model can be challenging; somehow the network control plane, container placement/spinup/cleanup, and service discovery must be coordinated. While most networks would treat each of these as a separate problem, service fabrics are designed to either interact with, or even replace, each of the systems involved with a single, unified overlay construct.
Kakivaya, et al., begin by considering the five major design principles of a service fabric: modular and layered design; self-* properties; decentralized operation; strong consistency; and support for stateful services. They then introduce Microsoft’s Service Fabric (SF) service, which they Continue reading
Tech Bytes: Thousand Eyes Shares Lessons Learned From A CenturyLink Outage (Sponsored)
CenturyLink suffered a major outage in December 2018 that affected services in large swathes of North America. On today's Tech Bytes episode, sponsored by ThousandEyes, we look at the causes of the outage and lessons learned, including the importance of ISP redundancy and why management networks are critical.
The post Tech Bytes: Thousand Eyes Shares Lessons Learned From A CenturyLink Outage (Sponsored) appeared first on Packet Pushers.
NSX-T Integration with Openshift
I am sometimes being approached with questions about NSX-T integration details for Openshift. It seems people are well aware how NSX-T works and integrates with Pivotal Container Service (aka PKS), Pivotal Application Service (PAS formerly known as PCF), and even with vanilla Kubernetes but there is no much information how we integrate with Redhat’s Openshift. This post aims to throw some light on the integration with this platform. In the examples below I am using Openshift Origin (aka OKD) but for a supported solution you need to go with Openshift Enterprise Platform. The same NSX-T instance can be used for providing networking, security, and visibility to multiple Openshift clusters.
Example Topology
In this topology we have a T0 router that connects physical with virtual world. We also have T1 router acting as a default gateway for the Openshift VMs. Those VMs have two vNICs each. One vNIC is connected to Management Logical Switch for accessing the VMs. The second vNIC is connected to a disconnected Logical Switch and is used by nsx-node-agent to uplink the POD networking. The LoadBalancer used for configuring Openshift Routes plus all project’s T1 routers and Logical Switches are created automatically later when we Continue reading
Short Take – Long-Tail DoS Attacks
In this Network Collective Short Take, Russ White shares what a long-tail denial of service attack is and why network engineers need to be thinking about them when designing their networks.
The post Short Take – Long-Tail DoS Attacks appeared first on Network Collective.
Metaswitch Senior VP of 5G Shubh Agarwal Discusses the Challenges Operators Face in Transitioning to 5G and the Technologies Key to Success
 Metaswitch Senior VP of 5G Shubh Agarwal Discusses the Challenges Operators Face in Transitioning...
Metaswitch Senior VP of 5G Shubh Agarwal Discusses the Challenges Operators Face in Transitioning...
Network Break 222: SnapRoute Launches Network OS; Carbonite Buys Webroot
Today's Network Break covers a brand new network OS from SnapRoute, new features in VMware's SD-WAN appliances, Carbonite's acquisition of Webroot, Cisco and Arista financial results, and more tech news.
The post Network Break 222: SnapRoute Launches Network OS; Carbonite Buys Webroot appeared first on Packet Pushers.
SOCKMAP – TCP splicing of the future

Recently we stumbled upon the holy grail for reverse proxies - a TCP socket splicing API. This caught our attention because, as you may know, we run a global network of reverse proxy services. Proper TCP socket splicing reduces the load on userspace processes and enables more efficient data forwarding. We realized that Linux Kernel's SOCKMAP infrastructure can be reused for this purpose. SOCKMAP is a very promising API and is likely to cause a tectonic shift in the architecture of data-heavy applications like software proxies.

But let’s rewind a bit.
Birthing pains of L7 proxies
Transmitting large amounts of data from userspace is inefficient. Linux provides a couple of specialized syscalls that aim to address this problem. For example, the sendfile(2) syscall (which Linus doesn't like) can be used to speed up transferring large files from disk to a socket. Then there is splice(2) which traditional proxies use to forward data between two TCP sockets. Finally, vmsplice can be used to stick memory buffer into a pipe without copying, but is very hard to use correctly.
Sadly, sendfile, splice and vmsplice are very specialized, synchronous and solve only one part Continue reading
Last Week on ipSpace.net (2019W7)
Last Tuesday we continued the deep dive into new Ansible networking modules functionality introduced in recent software releases (up to 2.7), including a demonstration of a few simple playbooks that collect printouts from network devices and check software version or end-to-end connectivity.
In the second half of the live session we started digging into the intricacies of device configuration management, ending with the truly “fun part”: changing access control lists on Cisco IOS.
The Ansible for Networking Engineers webinar is part of standard ipSpace.net subscription and Building Network Automation Solutions online course.
Connecting Python To Slack For Testing, Development, and Chat
Plugging Python Code Into Slack, Maybe For A Chatbot
The scripting language Python can retrieve information from or publish information to the messaging app Slack. This means you can write a chatbot that puts info into Slack for you, or accepts your queries using Slack as the interface. This is useful if you spend a lot of time in Slack, as I do.
The hard work of integrating Slack and Python has been done already. Slack offers an API, and there are at least two open source Python libraries that make leveraging these APIs in your Python code easy.
When searching for Slack projects using Python, most of the top hits are using Slack’s official python-slackclient. Github reveals that python-slackclient is an active project, with recent commits. In addition, most code examples I turned up are using python-slackclient. But it’s not a preference borne of experience. Maybe you’d prefer an alternate library like slacker.
Securing The Slack App Security Token
The slackclient library is security-conscious. Some other library sample code shows putting the Slack access token right in the source code as a static variable assignment, which is a terrible, horrible, no good, very bad idea. Why? If you publish Continue reading
Juniper AAA
Junos has a robust authentication, authorization and accounting (AAA) system ensuring authenticated users have access to only the things their permissions allow. Authentication Junos supports two categories of user authentication. Local - On box user database Remote -...continue reading



