2019 Resolutions for a Healthier NFV and SD-WAN Ecosystem
 A collaborative approach from service providers might yield better results than one that seeks to disempower the vendors.
A collaborative approach from service providers might yield better results than one that seeks to disempower the vendors.
Related Stories
Zimbabwe Chapter Meetup on IoT: Converse / Create / Collaborate

On December 6th 2018, the Internet Society Zimbabwe Chapter held an Internet of Things (IoT) meetup supported by the Beyond the Net Small Grants, a programme intented to assist the Internet Society Chapters with financial support to organize initiatives that contribute to the development of their communities.
An exciting convening brought together Zimbabweans with a keen interest in solving some of the pressing issues facing the country using IoT. The meetup was a drive by the Zimbabwe Chapter to create a platform for conversations around IoT security and the potential benefits of Internet-connected devices. More so, it sought to harness innovation potential by creating a space for IoT creativity and collaboration. It ran under the tagline “Converse/Create/Collaborate.”
The meetup was engineered on the basis that in order to push the IoT Security agenda forward there is need to use a multistakeholder approach. The first section of the meetup was a conversation on the subject matter through a keynote presentation and a panel discussion. Solomon Kembo gave the keynote talk and really set the pace on what IoT was and how it would solve most of our challenges in society. He also talked about the IoT projects that the Continue reading
Why NFV Interoperability and APIs are Joined at the Hip
Intelligent network automation and an API-first approach are the answers to enabling NFV to make good on its numerous promises.
Cisco Champion for 2019
Again I made it to the list of Cisco Champions, making this the second year in a row! I am so glad that my effort to give back to the community and to all my networking fellows out there paid off again in the shape of this recognition from Cisco. This badge is only a small thing, relating to all the community connections and sharing that my involvement with networking community via social media and this blog, made possible. It only pushes me to get even more done in the future. In 2018 I was involved in a few very challenging new
The post Cisco Champion for 2019 appeared first on How Does Internet Work.
Un triste début d’année pour le Congo
À peine la page du calendrier tournée que nous constatons plus de troubles sur Internet.
Aujourd’hui, Cloudflare peut confirmer, chiffres à l’appui, qu’Internet a été coupé en République Démocratique du Congo, information précédemment révélée par de multiples organes de presse. Cette coupure a eu lieu alors que se déroulait l’élection présidentielle le 30 Décembre dernier, et perdure pendant la publication des résultats.
Tristement, cette situation est loin d’être une nouveauté. Nous avons fait état d'événements similaires par le passé, y compris lors d’une autre coupure d’Internet en RDC il y a moins d’un an. Une courbe malheureusement bien familière est aujourd’hui visible sur notre plateforme de gestion du réseau, montrant que le trafic dans le pays atteint péniblement un quart de son niveau habituel.

Notez que le diagramme est gradué en temps UTC, et que la capitale de la RDC Kinshasa est dans le fuseau horaire GMT+1.
La chute du trafic a démarré en milieu de journée le 31 Décembre 2018 (à environ 10h30 UTC, soit 11h30 heure locale à Kinshasa). Celà est d’autant plus frappant quand sont superposées toutes les courbes quotidiennes:

Ci-dessus, la courbe rouge représente le trafic du 31 Décembre, et les courbes grises celui des 8 Continue reading
Sad start to the new year in the Democratic Republic of the Congo
The calendar has barely flipped to 2019 and already we’re seeing Internet disruptions.
Today, Cloudflare can quantitatively confirm that Internet access has been shut down in the Democratic Republic of the Congo, information already reported by many press organisations. This shutdown occurred as the presidential election was taking place on December the 30th, and continues as the results are published.
Sadly, this act is far from unprecedented. We have published many posts about events like this in the past, including a different post about roughly three days of Internet disruption in the Democratic Republic of the Congo less than a year ago. A painfully familiar shape can be seen on our network monitoring platform, showing that the traffic in the country is barely reaching a quarter of its typical level:
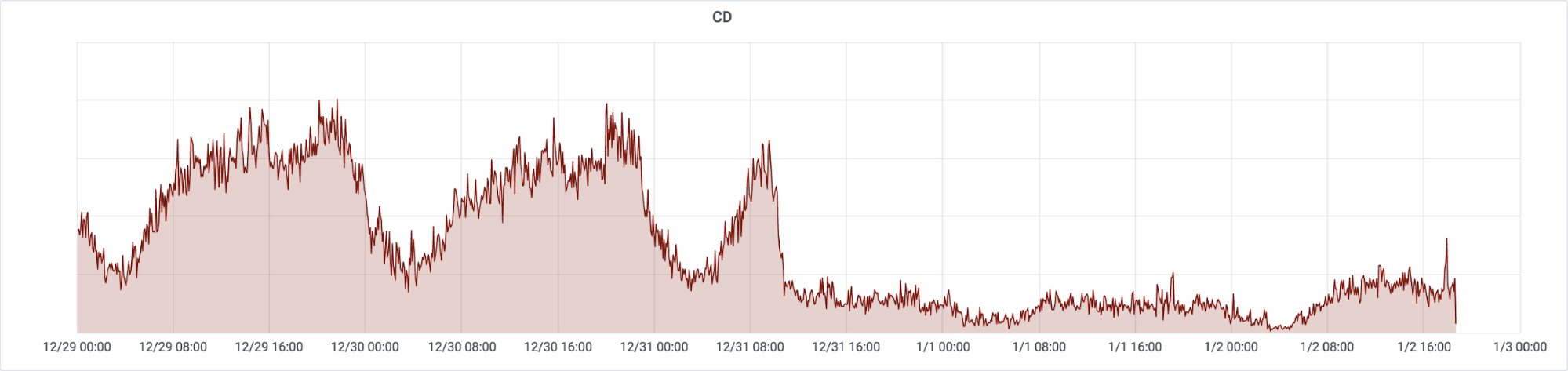
Note that the graph is based on UTC and Democratic Republic of the Congo’s capital Kinshasa has the timezone of GMT+1.
The drop in bandwidth started just before midday on 31 December 2018 (around 10:30 UTC, 11:30 local time in Kinshasa). This can be clearly seen if we overlay each 24 hour day over each other:
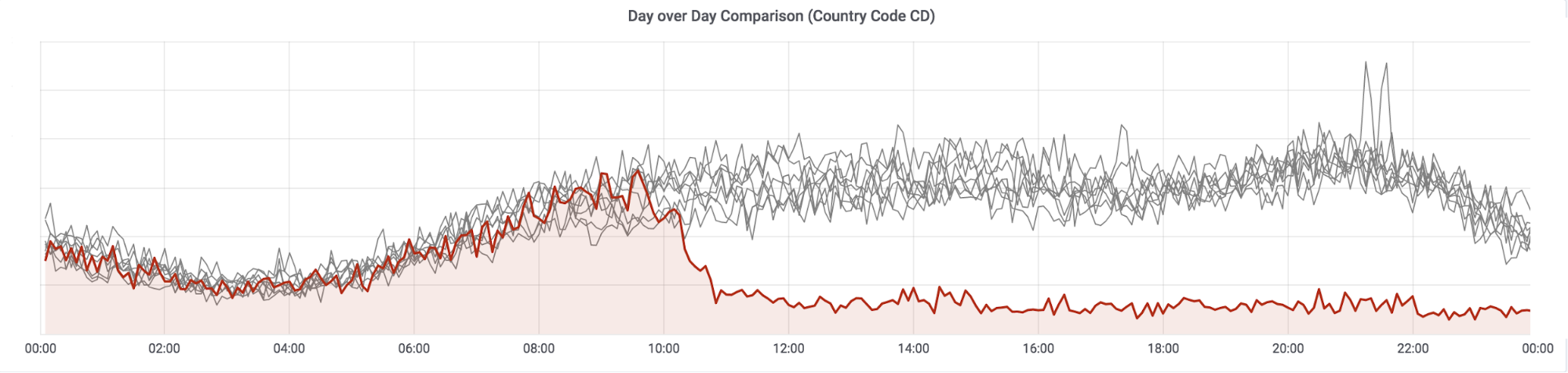
The red line is 31 December, the gray lines the previous eight days. Looking Continue reading
Ryuk Ransomware Takes Down Cloud Hosting Provider’s Systems
 Threat researchers linked Ryuk to the North Korean state-sponsored Lazarus Group believed to be behind the WannaCry attack.
Threat researchers linked Ryuk to the North Korean state-sponsored Lazarus Group believed to be behind the WannaCry attack.
Kernel of Truth episode 10: 2019 predictions
Subscribe to Kernel of Truth on iTunes, Google Play, Spotify, Cast Box and Sticher!
Click here for our previous episode.
As we enter the year, many, if not most, organizations have already been engaging in 2019 planning and strategizing. With that in mind, we thought what better way to wrap up our first season of Kernel of Truth than with an episode dedicated to trends and predictions straight from the brains of some of Cumulus’ brightest — CTO and Co-founder, JR Rivers, TME manager Pete Lumbis, and consultant David Marshall.
Join as we as discuss EVPN, virtualization, keeping up with the demands of digital transformation and more. This will be our last episode of the season, with our next season kicking off later this month.
Guest Bios
JR Rivers: JR is a co-founder and CTO of Cumulus Networks where he works on company, technology, and product direction. JR’s early involvement in home-grown networking at Google and as the VP of System Architecture for Cisco’s Unified Computing System both helped fine tunehis perspective on networking for the modern datacenter. Follow him on Twitter at @JRCumulus
Pete Lumbis: Pete is a Technical Marketing Engineer at Cumulus Networks. He helps Continue reading
2018 was a good and busy year ! Things I have done during the last year
2018 is done! I wanted to share what I have done during the last year. During 2018, probably the biggest decision for me was establishing a company in Turkey. This photo was taken during a CCDE Bootcamp 10 days after I opened an office in Istanbul. Before I established an Office, I was …
Continue reading "2018 was a good and busy year ! Things I have done during the last year"
The post 2018 was a good and busy year ! Things I have done during the last year appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Asterisk on Raspberry Pi

RaspPBX is a project which brings the free and open source Asterisk and FreePBX into Raspberry Pi board. RaspPBX turns Pi into a communications server which can be used by small businesses with up to 12 extensions. FreePBX is a web-based open source GUI that controls and manages Asterisk. Our goal is to show installation of the latest RaspPBX into Raspberry Pi 3 Model B Rev 1.2.
The latest image available for download includes Asterisk 13.20.0 and FreePBX 14.0.2.10.
1. Download, Extract and Copy RaspPBX Image to SD Card
$ wget http://download.raspberry-asterisk.org/raspbx-04-04-2018.zip
$ sudo dd bs=4M if=raspbx-04-04-2018.img of=/dev/mmcblk0 status=progress conv=fsync
$ unzip raspbx-04-04-2018.zip
2. Utilize all space on your SD card
By default the image utilizes only 4GB of your SD card space. Login to the console with username root and password raspberry and issue the command below.
# raspi-config
Navigate to Advanced Options-> A1 Expand Filesystem Ensures that all of the SD card storage is available to the OS. The filesystem will be enlarged upon the next reboot.
3. Configure Static IP Address
Set static IP address for interface eth0.
# echo "interface eth0" >> /etc/dhcpcd.conf
# echo Continue reading
BGP Implicit and Explicit Withdraw
BGP Implicit and Explicit Withdraw are important BGP messages. Understanding these two mechanisms not only help for understanding BGP convergence but also helps for BGP path diversity. While I was explaining BGP Add-Path in my Instructor Led CCDE course, I used the term ‘BGP Implicit Withdraw’ Then someone asked what is ‘ BGP Explicit …
Continue reading "BGP Implicit and Explicit Withdraw"
The post BGP Implicit and Explicit Withdraw appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Whither Network Engineering? (Part 1)
An article on successful writers who end up driving delivery trucks. My current reading in epistemology for an upcoming PhD seminar. An article on the bifurcation of network engineering skills. Several conversations on various slacks I participate in. What do these things have in common? Just this:
What is to become of network engineering?
While it seems obvious network engineering is changing, it is not so easy to say how it is changing, and how network engineers can survive those changes. To better understand these things, it is good to back up and take in a larger view. A good place to start is to think about how networks are built today.
Networks today are built using an appliance and circuit model. To build a network, an “engineer” (we can argue over the meaning of that word) tries to gauge how much traffic needs to be moved between different points in the business’ geographical space, and then tries to understand the shape of that traffic. Is it layer 2, or layer 3? Which application needs priority over some other application?
Once this set of requirements is drawn up, a long discussion over the right appliances and circuits to purchase to Continue reading
Response: Modchips, Hardware Implants and Bloomberg falsehoods

This video was presented at the 35C3 conference in Germany last week. The presenter is highly credible on the topic. Hardware implants and supply chain attacks have been in the news recently, but how feasible are they and what can we do about them? In this talk we’ll examine the design of a proof of […]
The post Response: Modchips, Hardware Implants and Bloomberg falsehoods appeared first on EtherealMind.
AT&T Sells Its Colocation Data Centres

AT&T has finally found a buyer for its colocation business. AT&T Inc announced today that it has completed the sale of its data center colocation operations and assets to Brookfield Infrastructure and its institutional partners (“Brookfield”). The company previously announced a strategic alliance with Brookfield that included the transfer of these operations and assets. Why […]
The post AT&T Sells Its Colocation Data Centres appeared first on EtherealMind.
Nokia Names Fixed Networks Biz Leader, Access Networks Remains Headless
 Sandra Motley was named president of the Fixed Networks Business organization. She previously served as COO of that group and will now report directly to Nokia President and CEO Rajeev Suri.
Sandra Motley was named president of the Fixed Networks Business organization. She previously served as COO of that group and will now report directly to Nokia President and CEO Rajeev Suri.
Flor de Ceibo Conecta2: Sharing Experiences

Today’s guest author is María Julia Morales González, the “Flor de Ceibo Conecta2” project manager and a professor at the Department of Sociology and Interdisciplinary Space of the University of the Republic Uruguay.
The Internet Society Uruguay Chapter, in partnership with the The University of the Republic and the Consejo de Formación en Educación, as well as with financial support from the Beyond the Net Funding Programme, has taken significant steps to help children and teenagers to develop digital skills in a creative and innovative way in three of the nineteen segments in which Uruguay is politically divided: Paysandú, Rivera, and Salto. Their project Flor de Ceibo Conecta2 aims to train young people from disadvantaged communities using digital resources in creative and challenging classes to help them improve their everyday lives and expand their chances for a better future.
Hoy queremos acercarles 2 experiencias que estamos transitando en el Proyecto Flor de Ceibo Conecta2.
Una de ellas se desarrolla en la ciudad de Salto en el liceo N° 7 del Barrio Artigas, zona de alta vulnerabilidad. Allí el equipo está trabajando en el uso de redes sociales y en particular en este taller en referencia al uso de whatsapp.
SK Telecom Gets the 5G Ball Rolling in 2019
 The 5G juggernaut rumbles on with South Korea getting a headstart on announcements in the new year. Meanwhile, posts on Reddit indicate AT&T's 5G is underwhelming, so far.
The 5G juggernaut rumbles on with South Korea getting a headstart on announcements in the new year. Meanwhile, posts on Reddit indicate AT&T's 5G is underwhelming, so far.
History Of Networking – EVPN – Rahul Aggarwal
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post History Of Networking – EVPN – Rahul Aggarwal appeared first on Network Collective.