Podcast: Network Control in the Multicloud Era
 In this podcast, you’ll hear from Sasha Ratkovic (CTO and Founder at Apstra), Josh George (VP Analytics, Data Science and Telemetry at Juniper Networks), and Ethan Banks (Co-founder at Packet Pushers) about the challenges and successes for network control.
In this podcast, you’ll hear from Sasha Ratkovic (CTO and Founder at Apstra), Josh George (VP Analytics, Data Science and Telemetry at Juniper Networks), and Ethan Banks (Co-founder at Packet Pushers) about the challenges and successes for network control.
SDxCentral’s Top 10 Articles — December 2018
 AT&T deploys white box cell-site routers in production; VMware CEO lists his top 3 priorities; Huawei's CFO is arrested.
AT&T deploys white box cell-site routers in production; VMware CEO lists his top 3 priorities; Huawei's CFO is arrested.
Alphabet’s Playbook Includes Pumping Billions Into Networking, AI
 Alphabet’s share of network and IT capex beat the two top cloud providers Amazon and Microsoft for the 12-month period ending Q3 2018.
Alphabet’s share of network and IT capex beat the two top cloud providers Amazon and Microsoft for the 12-month period ending Q3 2018.
ZTE Taps Former Senator Joe Lieberman to ‘Lobby’ on Its Behalf
 William Plummer, Huawei’s former VP of external affairs, said that company needs to diversify its leadership and not solely rely on Chinese nationals in its relations with the U.S.
William Plummer, Huawei’s former VP of external affairs, said that company needs to diversify its leadership and not solely rely on Chinese nationals in its relations with the U.S.
Whither Network Engineering? (Part 2)
In the first post of this series at the turn of 2019, I considered the forces I think will cause network engineering to radically change. What about the timing of these changes? I hear a lot of people say” “this stuff isn’t coming for twenty years or more, so don’t worry about it… there is plenty of time to adapt.” This optimism seems completely misplaced to me. Markets and ideas are like that old house you pass all the time—you know the one. No-one has maintained it for years, but it is so … solid. It was built out of the best timber, by people who knew what they were doing. The foundation is deep, and it has lasted all these years.
Then one day you pass a heap of wood on the side of the road and realize—this is that old house that seemed so solid just a few days ago. Sometime in the night, that house that was so solid collapsed. The outer shell was covering up a lot of inner rot. Kuhn, in The Structure of Scientific Revolutions, argues this is the way ideas always go. They appear to be solid one day, and then Continue reading
T-Mobile, Sprint Deal Approval Delayed by Government Shutdown
 The $26 billion deal sits about halfway through the FCC's informal timeline for its review process.
The $26 billion deal sits about halfway through the FCC's informal timeline for its review process.
Embattled Huawei and ZTE Get Spanish Boost
 Some sources told the Wall Street Journal that Ericsson and Nokia have been slow to capitalize on Huawei’s woes.
Some sources told the Wall Street Journal that Ericsson and Nokia have been slow to capitalize on Huawei’s woes.
The Transformations Shaping 2019
We don’t need new technologies in 2019, what we need is a complete vision for applying those new technologies. That’s a vision that our transformations will provide, at long last. In fact, in 2019, they’ll usher in the new age of computing.
Emerging Technologies: Bridging the Digital Gap in Africa

With all the excitement about the role of technology in contributing to social change and improved development outcomes across Africa, it is easy to forget that only 11% of the world’s Internet subscribers are Africans, while only 35.2% of Africans use the Internet. An effective science and innovation system in any country, and globally, I believe, depends on strong basic research and higher education infrastructure. In addition to knowledge production, basic research facilities, development of human resources, and applications are critical. But in the course of conducting, applying, and managing research, both researchers and managers of research and innovation have information needs. These needs must be satisfied in order for the scientists and the science innovation system to function effectively.
My recent participation at the 13th Internet Governance Forum (IGF) in Paris as a Youth@IGF Fellows brought me closer to the realization that technology has really increased the speed and reach of information everywhere – and now to communities in Africa.
Africa is leapfrogging information and communication technology development, which is also fueled by mobile broadband, but there are also worrying trends, such as a growing the digital divide between men and women, and between urban and rural areas.
2019 Resolutions for a Healthier NFV and SD-WAN Ecosystem
 A collaborative approach from service providers might yield better results than one that seeks to disempower the vendors.
A collaborative approach from service providers might yield better results than one that seeks to disempower the vendors.
Related Stories
Zimbabwe Chapter Meetup on IoT: Converse / Create / Collaborate

On December 6th 2018, the Internet Society Zimbabwe Chapter held an Internet of Things (IoT) meetup supported by the Beyond the Net Small Grants, a programme intented to assist the Internet Society Chapters with financial support to organize initiatives that contribute to the development of their communities.
An exciting convening brought together Zimbabweans with a keen interest in solving some of the pressing issues facing the country using IoT. The meetup was a drive by the Zimbabwe Chapter to create a platform for conversations around IoT security and the potential benefits of Internet-connected devices. More so, it sought to harness innovation potential by creating a space for IoT creativity and collaboration. It ran under the tagline “Converse/Create/Collaborate.”
The meetup was engineered on the basis that in order to push the IoT Security agenda forward there is need to use a multistakeholder approach. The first section of the meetup was a conversation on the subject matter through a keynote presentation and a panel discussion. Solomon Kembo gave the keynote talk and really set the pace on what IoT was and how it would solve most of our challenges in society. He also talked about the IoT projects that the Continue reading
Why NFV Interoperability and APIs are Joined at the Hip
Intelligent network automation and an API-first approach are the answers to enabling NFV to make good on its numerous promises.
Cisco Champion for 2019
Again I made it to the list of Cisco Champions, making this the second year in a row! I am so glad that my effort to give back to the community and to all my networking fellows out there paid off again in the shape of this recognition from Cisco. This badge is only a small thing, relating to all the community connections and sharing that my involvement with networking community via social media and this blog, made possible. It only pushes me to get even more done in the future. In 2018 I was involved in a few very challenging new
The post Cisco Champion for 2019 appeared first on How Does Internet Work.
Un triste début d’année pour le Congo
À peine la page du calendrier tournée que nous constatons plus de troubles sur Internet.
Aujourd’hui, Cloudflare peut confirmer, chiffres à l’appui, qu’Internet a été coupé en République Démocratique du Congo, information précédemment révélée par de multiples organes de presse. Cette coupure a eu lieu alors que se déroulait l’élection présidentielle le 30 Décembre dernier, et perdure pendant la publication des résultats.
Tristement, cette situation est loin d’être une nouveauté. Nous avons fait état d'événements similaires par le passé, y compris lors d’une autre coupure d’Internet en RDC il y a moins d’un an. Une courbe malheureusement bien familière est aujourd’hui visible sur notre plateforme de gestion du réseau, montrant que le trafic dans le pays atteint péniblement un quart de son niveau habituel.

Notez que le diagramme est gradué en temps UTC, et que la capitale de la RDC Kinshasa est dans le fuseau horaire GMT+1.
La chute du trafic a démarré en milieu de journée le 31 Décembre 2018 (à environ 10h30 UTC, soit 11h30 heure locale à Kinshasa). Celà est d’autant plus frappant quand sont superposées toutes les courbes quotidiennes:

Ci-dessus, la courbe rouge représente le trafic du 31 Décembre, et les courbes grises celui des 8 Continue reading
Sad start to the new year in the Democratic Republic of the Congo
The calendar has barely flipped to 2019 and already we’re seeing Internet disruptions.
Today, Cloudflare can quantitatively confirm that Internet access has been shut down in the Democratic Republic of the Congo, information already reported by many press organisations. This shutdown occurred as the presidential election was taking place on December the 30th, and continues as the results are published.
Sadly, this act is far from unprecedented. We have published many posts about events like this in the past, including a different post about roughly three days of Internet disruption in the Democratic Republic of the Congo less than a year ago. A painfully familiar shape can be seen on our network monitoring platform, showing that the traffic in the country is barely reaching a quarter of its typical level:
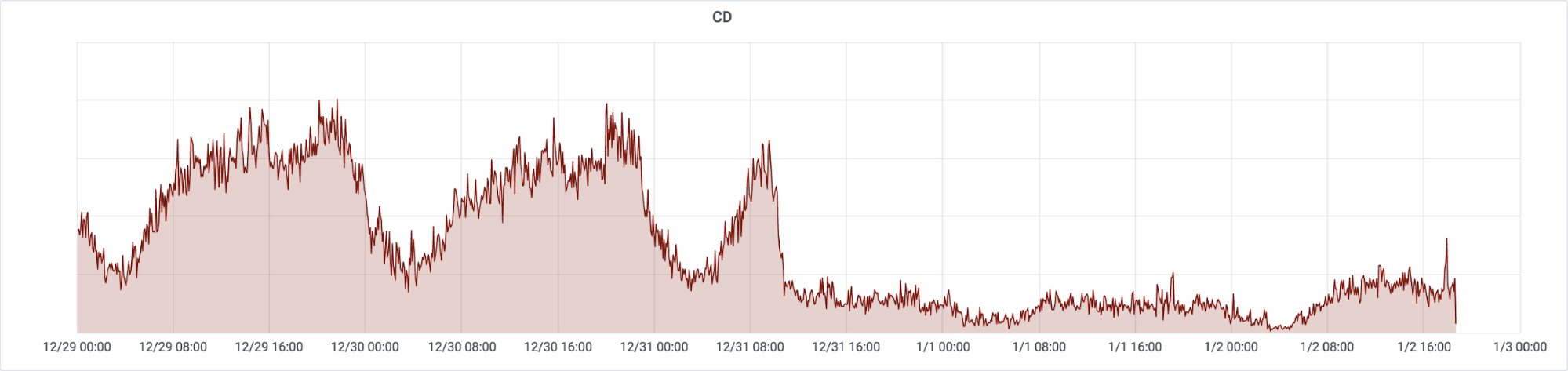
Note that the graph is based on UTC and Democratic Republic of the Congo’s capital Kinshasa has the timezone of GMT+1.
The drop in bandwidth started just before midday on 31 December 2018 (around 10:30 UTC, 11:30 local time in Kinshasa). This can be clearly seen if we overlay each 24 hour day over each other:
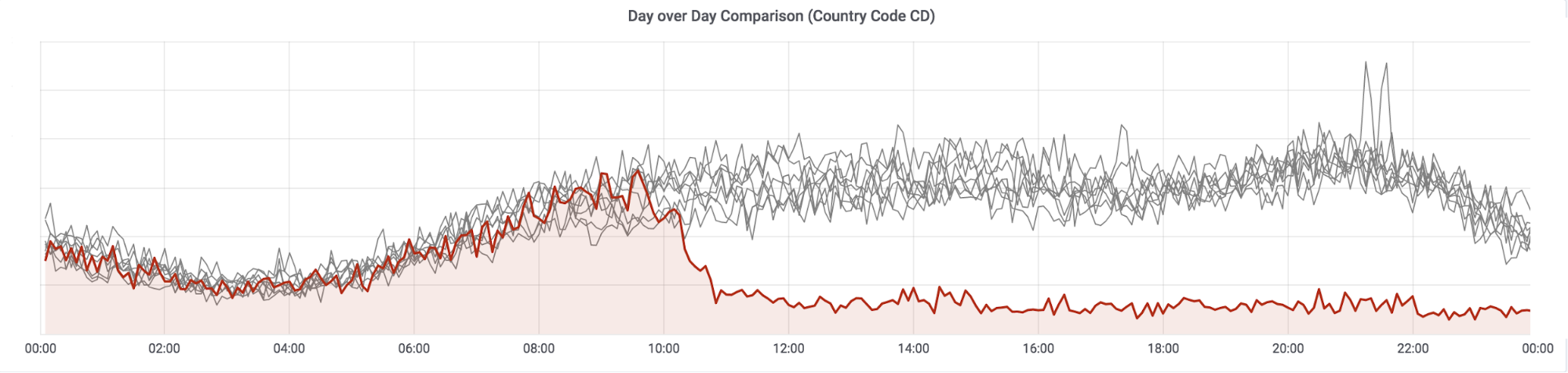
The red line is 31 December, the gray lines the previous eight days. Looking Continue reading
Ryuk Ransomware Takes Down Cloud Hosting Provider’s Systems
 Threat researchers linked Ryuk to the North Korean state-sponsored Lazarus Group believed to be behind the WannaCry attack.
Threat researchers linked Ryuk to the North Korean state-sponsored Lazarus Group believed to be behind the WannaCry attack.
Kernel of Truth episode 10: 2019 predictions
Subscribe to Kernel of Truth on iTunes, Google Play, Spotify, Cast Box and Sticher!
Click here for our previous episode.
As we enter the year, many, if not most, organizations have already been engaging in 2019 planning and strategizing. With that in mind, we thought what better way to wrap up our first season of Kernel of Truth than with an episode dedicated to trends and predictions straight from the brains of some of Cumulus’ brightest — CTO and Co-founder, JR Rivers, TME manager Pete Lumbis, and consultant David Marshall.
Join as we as discuss EVPN, virtualization, keeping up with the demands of digital transformation and more. This will be our last episode of the season, with our next season kicking off later this month.
Guest Bios
JR Rivers: JR is a co-founder and CTO of Cumulus Networks where he works on company, technology, and product direction. JR’s early involvement in home-grown networking at Google and as the VP of System Architecture for Cisco’s Unified Computing System both helped fine tunehis perspective on networking for the modern datacenter. Follow him on Twitter at @JRCumulus
Pete Lumbis: Pete is a Technical Marketing Engineer at Cumulus Networks. He helps Continue reading