The Network Collective: State of the Podcast
In this edition of the Network Collective, Eyvonne, Jordan, and I talk about where the ‘cast has been, and share some thoughts on where it is going. While we like technology as much as anyone else, the NC is really all about community.
In particular, we discuss the upcoming subscription service. We have a lot of new, exciting, material being recorded around the skills needed to be a better engineer exclusively for the subscription service. For instance, we’ve started a series on communication that does not take the standard line, but looks at how to communicate from the perspective of our experience in living on every possible side of the network engineering world, and developing and delivering every possible kind of content. And we have our first Q&A guest lined up, as well as a lot of fantastic material from Rachel Traylor already being recorded. This is going to be fantastic material, designed to push your career forward in a way that includes technology, but goes beyond technical skills, as well.
Red Hat OpenStack HCI Targets Telco Hybrid Cloud, 5G Deployments
 The hyperconverged platform combines Red Hat OpenStack Platform 13 and Red Hat Ceph Storage 3 into one product.
The hyperconverged platform combines Red Hat OpenStack Platform 13 and Red Hat Ceph Storage 3 into one product.
Lavelle Networks’ Shyamal Kumar Discusses SD-WAN and the Principles of B4
 In this interview with Lavelle Networks CEO Shyamal Kumar he shares his views on SD-WAN and how Lavelle has incorporated some of the principles of B4 to create a pure networking software solution.
In this interview with Lavelle Networks CEO Shyamal Kumar he shares his views on SD-WAN and how Lavelle has incorporated some of the principles of B4 to create a pure networking software solution.
US Senate Makes Moves to Reinstate Net Neutrality, But Sustainable Rules Are Still Necessary
On May 16, the Senate passed a Congressional Review Act (CRA) to overturn the Federal Communication Commission’s (FCC) repeal of the 2015 Open Internet Order. A CRA allows Congress to review regulations issued by government agencies and overrule them with a majority vote. This vote, led by Senator Ed Markey (D-MA), is a step towards reinstating the FCC’s 2015 net neutrality rules.
The CRA will now move to the House, where it will require a majority vote in order to pass before heading to President Trump’s desk for his signature. If the CRA passes the House and gets the President’s signature, the 2015 Order will be reinstated.
Despite the CRA’s success in the Senate, it is unlikely that it will pass the House. In the Senate, every Democrat, two Independents, and three Republicans were needed to pass the CRA. In the House, Democrats hold just 193 of 435 seats and would need to be joined by 25 Republican or Independent Representatives to move the CRA to the President’s desk. Even then, the bill would face another major hurdle, as President Trump has previously expressed support for overturning the FCC’s Open Internet Order.
This is not to mention the court cases Continue reading
BiB 42 – Pica8 Releases PicaPilot and PicaFabric
Pica8 makes it first steps into network automation in a unique fashion with apps for its PicOS NOS. PicaFabric build a virtual switch chassis from an leaf/spine switch clister. The PicaPilot app builds vitual switch stack for fat tree L2 everywhere campus networks. All this is done with open hardware that you can mix & […]
The post BiB 42 – Pica8 Releases PicaPilot and PicaFabric appeared first on Packet Pushers.
Building the Digital Silk Road Together: Kyrgyz Chapter Proposes Ideas for Internet Development in Central Asia at Cambridge University Forum
Central Asia, the most remote landlocked mountainous region in the world, has some of the most expensive Internet in global comparison. The cost of it can easily reach 10-20% of average monthly salary. In absolute terms, the price of the Internet can reach triple digits for 1 Mbps.
Acknowledging such challenges and considering the benefits that the Internet can bring, Central Asian governments are embarking on national digitalization strategies. The Kyrgyz Republic has launched a national program on digital transformation “Taza Koom” (“Transparent Society”). The program focuses on building an open government and a digital economy.
When it comes to digital development strategies, cooperation among countries is a mutually beneficial approach. To foster such collaboration, Cambridge University initiated a common platform called Digital Dialogue for Central Asia. The first meeting of this platform Making Inroads into Digital Transformation took place in Astana in April 2018.
Speaking at the forum on behalf of the Internet Society’s Kyrgyz Chapter, I proposed to jointly build the Digital Silk Road guided by the slogan: “free movement of ideas, people, creativity, technology and innovation”. Central Asia, with its favourable geographical location in Eurasia, could become the connecting host and focal point – a Continue reading
Dissecting IBGP+EBGP Junos Configuration
Networking engineers familiar with Junos love to tell me how easy it is to configure and operate IBGP EVPN overlay on top of EBGP IP underlay. Krzysztof Szarkowicz was kind enough to send me the (probably) simplest possible configuration (here’s another one by Alexander Grigorenko)
To learn more about EVPN technology and its use in data center fabrics, watch the EVPN Technical Deep Dive webinar.
Read more ...OpenStack Members Argue About the Definition of ‘the Edge’
 Many of the groups working on edge computing are associated with telco networking. But edge computing is definitely not limited to telco networks.
Many of the groups working on edge computing are associated with telco networking. But edge computing is definitely not limited to telco networks.
Rate Limiting: Delivering more rules, and greater control
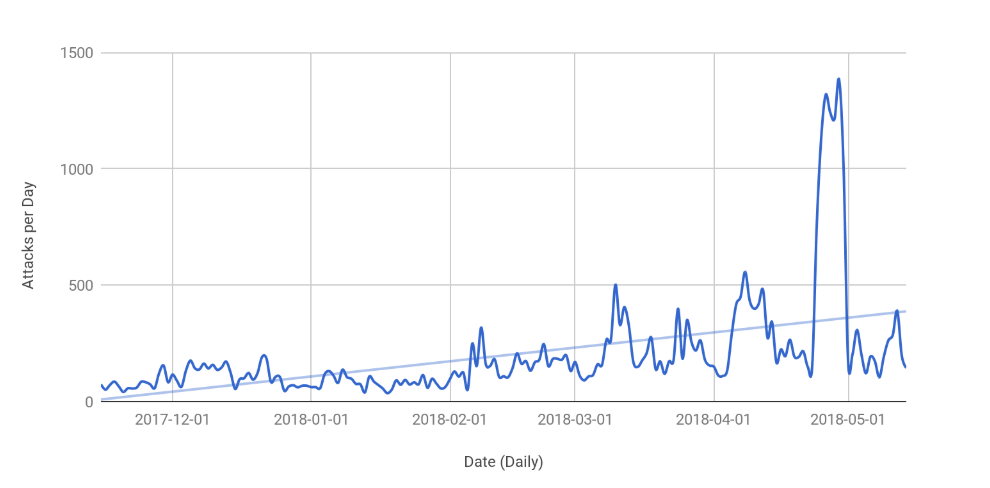
With more and more platforms taking the necessary precautions against DDoS attacks like integrating DDoS mitigation services and increasing bandwidth at weak points, Layer 3 and 4 attacks are just not as effective anymore. For Cloudflare, we have fully automated Layer 3/4 based protections with our internal platform, Gatebot. In the last 6 months we have seen a large upward trend of Layer 7 based DDoS attacks. The key difference to these attacks is they are no longer focused on using huge payloads (volumetric attacks), but based on Requests per Second to exhaust server resources (CPU, Disk and Memory). On a regular basis we see attacks that are over 1 million requests per second. The graph below shows the number of Layer 7 attacks Cloudflare has monitored, which is trending up. On average seeing around 160 attacks a day, with some days spiking up to over 1000 attacks.
A year ago, Cloudflare released Rate Limiting and it is proving to be a hugely effective tool for customers to protect their web applications and APIs from all sorts of attacks, from “low and slow” DDoS attacks, through to bot-based attacks, such as credential stuffing and content scraping. We’re pleased about the Continue reading