GE Digital’s Edge Manager Relies on Machine Learning and Analytics
 The company’s 2015 Wise.io acquisition serves as the foundation for its ML expertise.
The company’s 2015 Wise.io acquisition serves as the foundation for its ML expertise.![]()
ETSI NFV Group Collaborates with OPNFV
 ETSI NFV endeavors to make VNFs as open as possible.
ETSI NFV endeavors to make VNFs as open as possible.![]()
AT&T Expands Network-Based SD-WAN to 150 Countries
 Companies can mix and match connectivity for different site types while maintaining a single network.
Companies can mix and match connectivity for different site types while maintaining a single network.
AWS Pushes Serverless Application Repository Platform to GA
 The repository acts like a package manager to ease serverless deployments.
The repository acts like a package manager to ease serverless deployments.
Short Take: The Broadcom SDKLT Announcement
My first short take at The Network Collective is up discussing the Broadcom SDKLT announcement. Does this really mean the end of vendors or network engineering? You can guess my answer, or you can watch the video and hear it for yourself.
Future Thinking: Niel Harper on Cyber Threats
In 2017, the Internet Society unveiled the 2017 Global Internet Report: Paths to Our Digital Future. The interactive report identifies the drivers affecting tomorrow’s Internet and their impact on Media & Society, Digital Divides, and Personal Rights & Freedoms. In February 2018, we interviewed two stakeholders – Cyrating, a cybersecurity ratings agency, and Niel Harper, Senior Manager, Next Generation Leaders at the Internet Society – to hear their different perspectives on the forces shaping the Internet.
Niel Harper is a Young Global Leader at the World Economic Forum. He has more than 20 years of experience in the areas of telecoms management, cybersecurity, IT governance and strategy, ICT policy research and advisory services, and program management. (You can read Cyrating’s interview here).
The Internet Society: Experts predict an increase of frequency and impact of cyberattacks. What form are they likely to take in the future?
Niel Harper: In the foreseeable future, attackers are likely to fall under three categories: organized criminals seeking to profit from malicious online activities, online protesters (also known as hacktivists), and governments who target their own citizens or target other governments, whether for cyberespionage or cyberwarfare.
Criminals will continue to become more organized, selling Continue reading
Wireless Doctors

Wireless is a complicated thing. Even when you try to distill it down to networking basics on the wired side of the access point, you still have a very hard problem to solve on the radio side. Even I’ve talked in the past about how wireless is now considered a “solved” problem. But, the more I interact with wireless professionals and the more I think about the problem, the issue isn’t that IT departments think wireless is solved, it’s that they don’t appreciate the value of a specialist.
The Last Place Doctor
There’s an old joke that goes, “What do you call the person that graduated last in their medical school class? Doctor.” Professionals spend a lot of their time learning a tradecraft and practicing it to get better. And it’s not just doctors. So do plumbers, electricians, and teachers. Anyone that has ever tried to do any of these trades will tell you that the basics are capable of being figured out by the average non-professional, but the details are a huge leap.
You’d never assume that being able to put on a Band-Aid on a scrape would qualify you to do brain surgery. Or that changing a Continue reading
Future Thinking: Cyrating on Cyber Threats
In 2017, the Internet Society unveiled the 2017 Global Internet Report: Paths to Our Digital Future. The interactive report identifies the drivers affecting tomorrow’s Internet and their impact on Media & Society, Digital Divides, and Personal Rights & Freedoms. In February 2018, we interviewed two stakeholders – Cyrating, a cybersecurity ratings agency, and Niel Harper, Senior Manager, Next Generation Leaders at the Internet Society – to hear their different perspectives on the forces shaping the Internet’s future.
Cyrating is the first cybersecurity ratings agency anchored in Europe, and helps forward-thinking organizations maximize their cybersecurity performance and investments. It identifies potential for improvement, benchmarks it against industry best practices, and provides standardized cybersecurity metrics. We spoke to François Gratiolet, one of Cyrating’s founders, about the future of a secure and trusted Internet.
(You can read Niel Harper’s interview here).
The Internet Society: Experts predict an increase of frequency and impact of cyberattacks. What form are they likely to take in the next three to five years?
François Gratiolet: We believe cyberattacks will intensify in the next three to five years; targeting both Internet users and the Internet’s underlying infrastructure. User attacks will move from phishing to social media, with Continue reading
Go Subscriber-Centric and Think Beyond the Legacy Network
 A new white paper from Hewlett Packard Enterprise discusses how today’s (and tomorrow’s) successful CSPs are harnessing the power of telecom data to simplify their customers’ lives.
A new white paper from Hewlett Packard Enterprise discusses how today’s (and tomorrow’s) successful CSPs are harnessing the power of telecom data to simplify their customers’ lives.![]()
#PressForProgress – International Women’s Day 2018 | A Cloudflare & Branch Event

Almost a year ago, I began my journey in the tech industry at a growing company called Cloudflare. I’m a 30-something paralegal and although I didn’t know how to write code (yet), I was highly motivated and ready to crush. I had worked hard for the previous two years, focused on joining a thriving company where I could grow my intelligence, further develop my skill set and work alongside successful professionals. And finally, my hard work paid off; I landed the job at Cloudflare and booked a seat on the rocket ship.
After the initial whirlwind that accompanies this fast-paced field subsided, motivation, inspiration, success, momentum and endurance began to flood my neurons. I loved the inner workings of a successful startup, felt the good and bad of the tech industry, related to and admired the female executives and most importantly, wanted to give something back to the community that adopted me.

Venus Approaching the Sun Source: Flickr
During a routine chat with my dad, I pitched what I thought was a crazy idea. Crazy because I was so used to being told “no” at previous jobs, used to not having my ideas taken seriously, and also used to not Continue reading
PQ 140: OPNsense Wants To Be Your Open-Source Firewall
Today's Priority Queue looks at OPNsense, the open-source firewall and router. We examine features and capabilities, how it differs from other open firewalls, and more. The post PQ 140: OPNsense Wants To Be Your Open-Source Firewall appeared first on Packet Pushers.Big Changes Ahead for Core Internet Protocols – IETF Journal
 Excellent summary of what seems to be poorly understood. IPv6 is going nowhere slowly but the higher level protocols are changing today. Now, significant changes to the core Internet protocols are underway. While they are intended to be compatible with the Internet at large (since they won’t get adoption otherwise), they might be disruptive to […]
Excellent summary of what seems to be poorly understood. IPv6 is going nowhere slowly but the higher level protocols are changing today. Now, significant changes to the core Internet protocols are underway. While they are intended to be compatible with the Internet at large (since they won’t get adoption otherwise), they might be disruptive to […]Big Red Button for Network Automation
A while ago I was enjoying a few beers with a longtime friend of mine who happens to be running the networking team for one of the rare companies that understands how infrastructure should be built and operated.
Of course, I had to ask him what he thinks about the imminent death of CLI and all-encompassing automatic provisioning from some central orchestration system. Here’s the gist of his response:
Read more ...Ansible for Network Automation Tutorial
In this excerpt from "Practical Network Automation," learn how to get started with Ansible for networking.
Take Application Security to the Next Level – VMware and Carbon Black team up
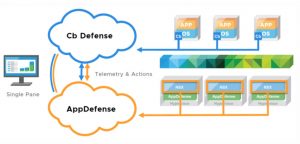
Perhaps you’ve already begun to secure virtualized applications by rolling out micro-segmentation with NSX, but segmentation of the network is only the beginning to embracing least privilege in your environment.
VMware has teamed up with Carbon Black to go beyond network protection and change the way your data center endpoints themselves are protected. By leveraging the unique properties of virtualization and the hypervisor, along with next-generation detection and response, VMware and Carbon Black are able to shrink your environment’s attack surface and respond to detected threats with precision and speed.
Learn more here, and come see the solution in action at the Cloud Force Security road show (coming to a city near you)!
The post Take Application Security to the Next Level – VMware and Carbon Black team up appeared first on Network Virtualization.