Chapterthon 2017 Winner: Closing the Digital Gap
We are excited to announce the winner of Chapterthon 2017.
As we truly believe that Internet Society and our community have an important role to promote the use of the Internet for education, we organized the Chapterthon 2017 on Digital Schools.
Chapterthon is a global Chapters marathon, where our chapters can participate by developing a project within a timeline and budget to achieve the common goal of improving education by using the Internet.
During the past months, 31 Chapters from all the regions have worked hard to extend the education benefits of the Internet to their communities. Connecting schools to the Internet, teaching coding to girls, training teachers and parents, raising awareness about the safe use of the Internet, developing an online platform for a school and helping to create educational, and local content are just some examples of the amazing work our chapters have done.
Each project has proven us once more that the Internet plays an important role in achieving the Sustainable Development Goal on Education. Each project has contributed to shaping the future of children, parents and teachers.
While all the projects have left an important mark on local schools, the Internet Society community members have voted Continue reading
8 Tech Books for Winter Reading
Got some downtime this winter? Check out these new releases on cloud, containers, and more.
Today’s Steps to Make a Better Tomorrow!
We are delighted to announce the launch of 2016 Beyond the Net Impact Report and 13 amazing new projects.
As we look at the past year, we are proud of the achievements our community has made with funding from the Beyond the Net Programme. We have some great examples of how the Internet can have a positive impact in people’s everyday lives. By building community networks in Africa and Europe, improving Internet connections in North America, or ensuring that people can trust their connection in Asia, we’re contributing to things like closing the gender gap, building partnerships, and helping kids stay in school.
In 2016, we took a huge step forward to consolidate the Beyond the Net Programme. When we see how the Internet can improve the lives of hundreds of farmers in Latin America or how children can develop new skills by learning how to use the Internet in the Middle East, the aim of the program and of our organization becomes crystal clear. The numbers and the stories behind them are a good reminder that the Internet was built as a force for good.
The projects highlighted in this report serve as a critical reminder that as long Continue reading
BGP: the Tragedy of the Commons
Every now and then someone looks at a few recent BGP incidents (from fat fingers to more dubious ones) and says “we need a better BGP”.
It’s like being unable to cope with your kids or your team members because you don’t have the guts to tell them NO and trying to solve the problem by implementing new procedures and rules.
Like anything designed on a few napkins BGP has its limit. They’re well known, and most of them have to do with trusting your neighbors instead of checking what they tell you.
The solutions to the problem are pretty simple and have been known for decades (BCP38 was published in May 2000). In a nutshell you have to:
- Build a global repository of who owns what address space;
- Document who connects to whom and what their peering policies are;
- Filter the updates received from your customers and peers based on the information from those repositories;
- Filter the traffic from addresses that are obviously spoofed.
We have most of the tools we need to get the job done; you’ll find them described in Best Current Practice (BCP) 194. It’s also not impossible to get the job done Continue reading
The Concept of Switch Virtual Interface – SVI
Before i started with SVI- Switch Virtual Interface followed by the configuration part, I would like to tell you guys that we have our own youtube channel for various network videos that can further help you guys to study further. I will going to add many more videos soon on the channel, Please subscribe to the channel for the study network related videos.
Monitoring your DANE deployment
In a previous series of articles (part 1, part 2) we described how to install and use DANE for verifying your email and web server certificates through the DNS. In this article, I discuss how to monitor whether your TLSA records still match the certificates used for your services.
The aim is help people doing something similar, as this monitoring system saved the DANE deployment in the Go6lab from being broken many times, especially at the very beginning of deployment when the automated systems we built didn’t work completely correctly all the time 
If we’re using self-signed certificates for our services and we manually change the underlying key, then we’ll probably also change the values of the TLSA records. If we forget to change them or are using, for example, Let’s Encrypt that automatically renews the certificate every 90 days, then we need to have some automatic DANE monitoring system that informs us of misalignment between the certificate being used and the TLSA record.
For this reason there are more and more online tools to check individual services by entering the URL and port, and with a press of a button tell if things are still working fine. A few Continue reading
PYEZ Script – Commit the configuration or Indicate the Diff
Requirement – Connect to a MX device to commit a configuration on the Device, if there is any un-committed configuration, Script should hold and display the un-committed configuration.
Basically,
JNPR.JUNOS – Device – helps us to connect to device
JNPR.JUNOS – Util.Config – helps to issue config related (Rollback/Config) etc
\033 – Helps the print statement to display in colored Format, [91m – Red , [1m – Bold , [0m indicates to end the color format
I have some uncommitted configuration on the device and hence we expect the script to indicate us the uncommitted configuration
Once i Fix the config, on the device, lets see if the configuration from the script gets fixed
This is an Intro to how we can start deploying or to check any devices which has any UnCommitted configuration on the Devices and Proceed Accordingly.
-Rakesh
ZFS on Linux with Encryption Part 2: The Compiling
First off: Warning. I don’t know what the stability of this feature is. It’s been in the code for a couple of months, it hasn’t been widely used. I’ve been testing it, and so far it’s worked as expected.
In exploring native encryption, I attempted to get it on Linux/ZFS using the instruction on this site: https://blog.heckel.xyz/2017/01/08/zfs-encryption-openzfs-zfs-on-linux/. While I’m sure they worked at the time, the code in the referenced non-standard repos has changed and I couldn’t get anything to compile correctly.
After trying for about a day, I realized (later than I care to admit) that I should have just tried the standard repos. They worked like a charm. The instructions below compiled and successfully installed ZFS on Linux with dataset encryption on both Ubuntu 17.10 and CentOS 7.4 in the November/December 2017 time frame.
Compiling ZFS with Native Encryption
The first step is to make sure a development environment is installed on your Linux system. Make sure you have compiler packages, etc. installed. Here’s a few packages for CentOS you’ll need (you’ll need similar packages/libraries for whatever platform you run).
- openssl-devel
- attr, libattr-devel
- libblkid-devel
- zlib-devel
- libuuid-devel
The builds were pretty good at telling Continue reading
ZFS and Linux and Encryption Part 1: Raining Hard Drives
(Skip to Part II to learn how to install ZFS with encryption on Linux)
Best Buy has been having a constant series of sales on WD Easy Store 8 TB drives. And it turns out, inside many of them (though not all) are WD Red NAS 5400 RPM drives. For $130-180 a piece, that’s significantly less than the regular price on Amazon/Newegg for these drives bare, which is around $250-$275.
(For updates on the sales, check out the subreddit DataHoarder.)

Over the course of several months, I ended up with 6 WD Red NAS 8 TB drives. Which is good, because my current RAID array is starting to show its age, and is also really, really full.
If you’re not familiar with the WD NAS Red’s, they’re drives specifically built to run 24/7. The regular WD Reds are 5400 RPM, so they’re a bit slower than a regular desktop drive (the Red Pro are 7200 RPM), but I don’t really care for my workload. For speed I use SSDs, and these drives for bulk storage. Plus, the slower speeds mean less heat and less power.
My current array is made of (5) 3 TB drives operating at Continue reading
A Workshop on Internet Economics
In the United States the debate between advocates of market-based resolution of competitive tensions and regulatory intervention has seldom reached the fever pitch that we've seen over the vexed on-again off-again question of Net Neutrality in recent weeks. How can we assist and inform that debate? One way is to bring together the various facets of how we build, operate and use the Internet and look at these activities from a perspective of economics. This is the background to a relatively unique gathering, hosted each year by CAIDA, the Centre for Applied Internet Data Analysis, at the University of California, San Diego, at WIE, the Workshop on Internet Economics. These are my notes from the 8th such workshop, held in December 2017.VMware SDDC with NSX Expands to AWS
I prior shared this post on the LinkedIN publishing platform and my personal blog at HumairAhmed.com. There has been a lot of interest in the VMware Cloud on AWS (VMC on AWS) service since its announcement and general availability. Writing this brief introductory post, the response received confirmed the interest and value consumers see in this new service, and I hope to share more details in several follow-up posts.
VMware Software Defined Data Center (SDDC) technologies like vSphere ESXi, vCenter, vSAN, and NSX have been leveraged by thousands of customers globally to build reliable, flexible, agile, and highly available data center environments running thousands of workloads. I’ve also discussed prior how partners leverage VMware vSphere products and NSX to offer cloud environments/services to customers. In the VMworld Session NET1188BU: Disaster Recovery Solutions with NSX, I discussed how VMware Cloud Providers like iLand and IBM use NSX to provide cloud services like DRaaS. In 2016, VMware and AWS announced a strategic partnership, and, at VMworld this year, general availability of VMC on AWS was announced; this new service, and, how NSX is an integral component to this service, is the focus of this post.
VMware SDDC with NSX Expands to AWS
 I prior shared this post on the LinkedIN publishing platform and my personal blog at HumairAhmed.com. There has been a lot of interest in the VMware Cloud on AWS (VMC on AWS) service since its announcement and general availability. Writing this brief introductory post, the response received confirmed the interest and value consumers see in this new service,... Read more →
I prior shared this post on the LinkedIN publishing platform and my personal blog at HumairAhmed.com. There has been a lot of interest in the VMware Cloud on AWS (VMC on AWS) service since its announcement and general availability. Writing this brief introductory post, the response received confirmed the interest and value consumers see in this new service,... Read more →
Raspberry Pi3 WIFI Router Based on Linux piCore
Recently I have bought a Christmas present for myself from GearBest, costing only $49,21 USD. It includes Raspberry Pi 3 single board computer along with 2.5A power supply, case and several heat sinks. Pi3 is the latest and the most powerful Raspberry model, equipped with 1.2GZ 64-bit ARM processor, 1GB RAM and integrated 10/100 Ethernet port and Wifi 802.11n. Although I can simply use it as a cheap desktop computer, I have different goal in my mind.
Six years ago, I built my own SOHO router/switch base on Intel Pentium III - 733Mhz. It was working great but to save electricity consumption I have never used it in production. However, I have never completely given up idea to build and use my own router. It comes true thanks to Raspberry Pi3 computer as it consumes maximum 1.34 A or 6.7 W under stress when peripherals and WiFi are connected.
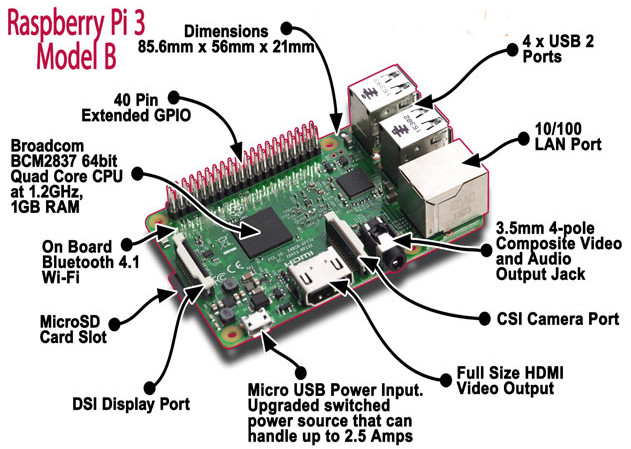
Picture1 - Raspberry Pi 3 Model B
Source: http://fosssig.com/tinkerers/1-raspberry-pi-and-kodi/
To shorten the story, I have built a wifi router that runs piCore 9.0.3 on Raspberry PI3. The clients are connected via wireless network to the router that runs hostapd. The hostapd is configured Continue reading
Please Respond: Survey on Interconnection Agreements
Marco Canini is working on another IXP-related research project and would like to get your feedback on inter-AS interconnection agreements, or as he said in an email he sent me:
As academics, it would be extremely valuable for us to receive feedback from network operators in the industry.
It’s fantastic to see researchers who want to base their work on real-life experience (as opposed to ideas that result in great-looking YouTube videos but fail miserably when faced with reality), so if you’re working for an ISP please take a few minutes and fill out this survey.
Highlights from Cloudflare’s Weekend at YHack

Along with four other Cloudflare colleagues, I traveled to New Haven, CT last weekend to support 1,000+ college students from Yale and beyond at YHack hackathon.
Throughout the weekend-long event, student attendees were supported by mentors, workshops, entertaining performances, tons of food and caffeine breaks, and a lot of air-mattresses and sleeping bags. Their purpose was to create projects to solve real world problems and to learn and have fun in the process.
How Cloudflare contributed
Cloudflare sponsored YHack. Our team of five wanted to support, educate, and positively impact the experience and learning of these college students. Here are some ways we engaged with students.
1. Mentoring
Our team of five mentors from three different teams and two different Cloudflare locations (San Francisco and Austin) was available at the Cloudflare table or via Slack for almost every hour of the event. There were a few hours in the early morning when all of us were asleep, I'm sure, but we were available to help otherwise.
2. Providing challenges
Cloudflare submitted two challenges to the student attendees, encouraging them to protect and improve the performance of their projects and/or create an opportunity for exposure to 6 million+ potential users of Continue reading
Highlights from Cloudflare’s Weekend at YHack

Along with four other Cloudflare colleagues, I traveled to New Haven, CT last weekend to support 1,000+ college students from Yale and beyond at YHack hackathon.
Throughout the weekend-long event, student attendees were supported by mentors, workshops, entertaining performances, tons of food and caffeine breaks, and a lot of air-mattresses and sleeping bags. Their purpose was to create projects to solve real world problems and to learn and have fun in the process.
How Cloudflare contributed
Cloudflare sponsored YHack. Our team of five wanted to support, educate, and positively impact the experience and learning of these college students. Here are some ways we engaged with students.
1. Mentoring
Our team of five mentors from three different teams and two different Cloudflare locations (San Francisco and Austin) was available at the Cloudflare table or via Slack for almost every hour of the event. There were a few hours in the early morning when all of us were asleep, I'm sure, but we were available to help otherwise.
2. Providing challenges
Cloudflare submitted two challenges to the student attendees, encouraging them to protect and improve the performance of their projects and/or create an opportunity for exposure to 6 million+ potential users of Continue reading
Web-scale data: Are you letting stability outweigh innovation?
At Cumulus Networks, we’re dedicated to listening to feedback about what people want from their data centers and developing products and functionality that the industry really needs. As a result, in early 2017, we launched a survey all about trends in data center and web-scale networking to get a better understanding of what the landscape looks like. With over 130 respondents from various organizations and locations across the world, we acquired some pretty interesting data. This blog post will take you through a little teaser of what we discovered (although if you just can’t wait to read the whole thing, you can check out the full report here) and a brief analysis of what this data means. So, what exactly are people looking for in their data centers this coming year? Let’s look over some of our most fascinating findings.
What initiatives are organizations most invested in?
There are a lot of exciting ways to optimize a data center, but what major issues are companies most concerned with? Well, according to the data we acquired, cost-effective scalability is the most pressing matter on organizations’ minds. Improved security follows behind at a close second, as we can tell from the Continue reading





