Solving the Problem in the Right Place
Sometimes I have this weird feeling that I’m the only loony in town desperately preaching against the stupidities heaped upon infrastructure, so it’s really nice when I find a fellow lost soul. This is what another senior networking engineer sent me:
I'm belonging to a small group of people who are thinking that the source of the problem are the apps and the associated business/security rules: their nature, their complexity, their lifecycle...
Sounds familiar (I probably wrote a few blog posts on this topic in the past), and it only got better.
Read more ...Deploy360 @ ENOG 14
 Our colleague Jan Žorž from the Deploy360 team will be presenting at the 14th Eurasia Network Operators Groups (ENOG 14) on 9-10 October 2017 in Minsk, Belarus. This is being preceded by workshops on Best Practices in IPv6 BGP and DNSSEC Operations.
Our colleague Jan Žorž from the Deploy360 team will be presenting at the 14th Eurasia Network Operators Groups (ENOG 14) on 9-10 October 2017 in Minsk, Belarus. This is being preceded by workshops on Best Practices in IPv6 BGP and DNSSEC Operations.
Jan will be talking about his real life experiences with NAT64/DNS64 and will be demonstrating the NAT64check tool on Monday evening (17.00-18.15). Following after his talk is a BoF on the Internet-of-Things (18.30-19.30), which is also sure to include discussions about the importance of IPv6 to scale the expected many billions of devices in future.
We’d also like to highlight the Cloudflare update on IPv6, DNS, DNSSEC, CA certs from Martin Levy (Cloudflare) on the Tuesday (10.00-11.30), who seems to be managing to cover just about all the Deploy360 topics in one talk. And for routing security, Kirill Malevanov, (Selectel) will be discussing his experiences of IPv4 prefix hijacking.
More Information
The post Deploy360 @ ENOG 14 appeared first on Internet Society.
Support New Ways of Working To Connect The World
The World Telecommunications Conference (WTDC) begins today. This is a key moment to remind the world that together we can shape a digital future that puts humanity at the heart of the Internet. But to do this we need your help.
Help send the message that to close the digital divide we’ll need new ways of working, new ways of thinking, and new policies support it all.
Much of what we are speaking on at WTDC serve as real-world examples of the kinds of things we need policy and decision makers to support – community networking being a key focus.
We will keep you up-to-date on what is happening and what we need to do next the conference.
Here’s how you can help:
Take part in a Pre-Event Roundtable
On Sunday, October 8, 17:20 UTC (4:20 PM Argentina Local Time) Internet Society’s Vice President, Global Engagement Raúl Echeberría will speak on the importance of community networks at a Pre-Event-Private Sector Roundtable on Partnering for the SDGs. Watch it here.
Share Raul’s Blog
Raul’s wrote a critical blog to launch our WTDC message. Please share it across your channels.
“Every Connection Matters – Shape Tomorrow and Help Close Digital Continue reading
BGP ADD-PATH – Summary
Hi,
First things first, I have been getting a lot of requests to upload the lab’s which i illustrate as is, so i shall be uploading them to a Github page with initial and final-configs and Instead of vagrant i shall be using EVE-NG as a tool so that you guys can import them easily.
Going through Fabric-Path and CLOS concepts, got myself started with 3 Stage Clos and as a part of understanding it, discovered something.
Why – To make sure Servers at one end have equal cost path to the servers-at other end, at scale the spine accordingly optimizing the CAPEX.
Simple words, in the below topology, we need to make sure that R6 has equal cost to R7 and vice-versa.
Protocols and setup
-> OSPF for the entire domain and Ibgp to peer between RR (R2) and all other loopbacks, we use OSPF so that Ibgp peering will be over Loopback and also for load-balancing protocol Next-hops
-> Default routes on R6 and R7, load-balance (per-packet) on all-routers (where technically required)
-> R3 AND R4,R5 has static back to loopbacks of R6 and R7 respectively, advertising them into OSPF will defeat the purpose obviously Continue reading
Introduction to DHCP (Dynamic host configuration protocol)
- IP address
- Subnet mask
- Default gateway
- DNS server IP
 |
| Fig 1.1- DHCP Server |
Worth Reading: Is More Technology Good for Your Business?
Gian Paolo Boarina published a great article following my Are You Solving the Right Problem rant.
Long story short: everyone in the networking game has their own agenda, and it’s not necessarily good for you or your business.
Red Hat Updates Container Storage Platform as Market Strives for Maturity
 The update allows customers to manage, scale, and upgrade their storage needs using a single control plane.
The update allows customers to manage, scale, and upgrade their storage needs using a single control plane.
“Keep those eyebrows up!” – Cybersecurity at the Global Women’s Forum
News of cyberattacks is slowly becoming a new normal. We are still at a stage where high-profile cases, like the recent attack against the American credit reporting company Equifax, in which 145.5 million users had their personal information compromised, raise eyebrows. But we need those eyebrows to stay up because we should never accept cyber threats as the new normal.
This week in Paris, hundreds of leaders met at the Women’s Forum to discuss some of the key issues that will shape the future of a world in transition, including cybersecurity. But this topic is not just a concern for the experts – it’s a concern to all men and women leading any business today.
New risks on the horizon
A recent report by the Internet Society, “Paths to Our Digital Future”, points out that now is a big moment for the Internet. The revolution we already see could accelerate in the coming years, not only due to the increasing digitalization of services and businesses, but also through the expansion of objects being connected to the Internet – the Internet of Things (IoT). By 2020 more than 20 billion “things” could be connected.
Suddenly it’s not only Continue reading
SDxCentral Weekly News Roundup — October 6, 2017
 BT and SK Telecom partner with the Telecom Infra Project; CenturyLink and Level 3 merger gets DOJ approval.
BT and SK Telecom partner with the Telecom Infra Project; CenturyLink and Level 3 merger gets DOJ approval.
Gartner Survey: CIOs Move from Cost Savers to Revenue Generators
 For 2018, 26 percent of CIOs say growth is their number one priority.
For 2018, 26 percent of CIOs say growth is their number one priority.
Nokia Using Startup Pensa’s Automation Software
 The SaaS spins up virtual data centers “within minutes.”
The SaaS spins up virtual data centers “within minutes.”
Telenor, Cisco Launch Mobile-Focused Neutral Cloud Platform
 WG2 is looking to bring cloud ecosystems closer to mobile telecom operators.
WG2 is looking to bring cloud ecosystems closer to mobile telecom operators.
Show 360: All About Optics With InterOptic (Sponsored)
On today's sponsored Weekly Show, InterOptic CEO Tim Dixon joins the Packet Pushers for a lively discussion about the world of optics. The post Show 360: All About Optics With InterOptic (Sponsored) appeared first on Packet Pushers.Traceroute Lies! A Typical Misinterpretation Of Output
Sometimes a user with performance issues will proudly present me with a traceroute and point to a particular hop in the network and accuse it of being the problem because of high latency on the link. About 1 time in 1000 they are correct and the link is totally saturated. The other 999 times, well, let me explain.
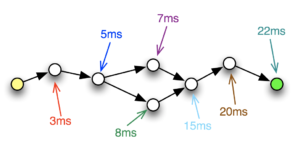
Traceroute Output
Here’s a typical traceroute I might be sent by a user (IPs and hostnames are altered to protect the innocent):
$ traceroute www-europe traceroute to www-europe (18.9.4.17), 64 hops max, 52 byte packets 1 gateway (57.239.196.133) 11.447 ms 18.371ms 25.057 ms 2 us-atl-edge (137.16.151.202) 13.338 ms 20.070 ms 19.119 ms 3 us-ga-core (57.239.129.37) 103.789 ms 105.998 ms 103.696 ms 4 us-nyc-core (57.239.128.189) 107.601 ms 103.116 ms 103.934 ms 5 us-east-core (57.239.13.42) 103.099 ms 104.215 ms 109.042 ms 6 us-east-bb1 (57.239.111.58) 107.824 ms 104.463 ms 103.482 ms 7 uk-south-bb1 (57.240.117.81) 106.439 ms 111.156 ms 104.761 ms Continue reading
Back In The Saddle Of A Horse Of A Different Color

I’ve been asked a few times in the past year if I missed being behind a CLI screen or I ever got a hankering to configure some networking gear. The answer is a guarded “yes”, but not for the reason that you think.
Type Casting
CCIEs are keyboard jockeys. Well, the R&S folks are for sure. Every exam has quirks, but the R&S folks have quirky QWERTY keyboard madness. We spend a lot of time not just learning commands but learning how to input them quickly without typos. So we spend a lot of time with keys and a lot less time with the mouse poking around in a GUI.
However, the trend in networking has been to move away from these kinds of input methods. Take the new Aruba 8400, for instance. The ArubaOS-CX platform that runs it seems to have been built to require the least amount of keyboard input possible. The whole system runs with an API backend and presents a GUI that is a series of API calls. There is a CLI, but anything that you can do there can easily be replicated elsewhere by some other function.
Why would a company do this? To Continue reading
Google, Barefoot Networks Add Legs to P4 with Runtime API
 P4 Runtime overcomes SDN shortfall of a programmable forwarding plane.
P4 Runtime overcomes SDN shortfall of a programmable forwarding plane.
Level 3 Expands Its Network Security in APAC, Africa
 The security platform is designed to be compatible with SD-WAN.
The security platform is designed to be compatible with SD-WAN.
A Fast, Secure Migration to Google Cloud Platform using Cloudflare
OnAir Video Presentation
Abstract

Looking to host your website, application, or API in the cloud, or migrate to a new cloud provider while keeping your data secure? In this webinar, Trey Guinn, Head of Solutions Engineering at Cloudflare, will discuss how companies should approach security, during and after migration. We'll highlight the migration story of LUSH, one of the largest global e-Commerce cosmetic retailers, and how they took the right steps to migrate from their previous cloud provider to Google Cloud Platform, in less than 3 weeks. Trey will be performing a live demo on setting up Cloudflare load balancing across cloud providers, as well as
Speakers
Asad Baheri
Security & Networking Partner Manager
Google Cloud Platform
Trey Guinn
Head of Solutions Engineering
Cloudflare
Webinar Transcription and Load Balancing Demo
Asad Baheri
 Today we're going to talk about LUSH's migration to Google Cloud and how Cloudflare, one of our top security and performance partners, can help you with your own cloud migration. Throughout our presentation, we'll be talking about security best practices, how CDNs and the CDN Interconnect program works, and we're also going to also give you a demo of Cloudflare's load balancing to start your migration.
Today we're going to talk about LUSH's migration to Google Cloud and how Cloudflare, one of our top security and performance partners, can help you with your own cloud migration. Throughout our presentation, we'll be talking about security best practices, how CDNs and the CDN Interconnect program works, and we're also going to also give you a demo of Cloudflare's load balancing to start your migration.

One of Continue reading
IPv6, DNSSEC, Security and More at ION Malta
The Deploy360 team is back from ION Malta, which took place on 18 September alongside an ICANN DNSSEC Training Workshop. We again thank our sponsor Afilias for making this possible, and are now working toward our final ION Conference of the year, ION Belgrade in November. All the presentations from ION Malta are available online.
I opened the event with an introduction to Deploy360 and an invitation for everyone to get involved with the Internet Society’s 25th anniversary the next day. We also heard from Jasper Schellekens, the president of the ISOC Malta Chapter about their activities and how to get more involved. They have a small but mighty presence in Malta and are looking forward to getting more members and increasing their activity.
Next, Nathalie Trenaman from RIPE NCC gave a fascinating presentation on the status of IPv6 in Malta. Unfortunately, IPv6 penetration in Malta is extremely low, but ISPs are transferring IPv4 address space around and, interestingly, have purchased over 30,000 IPv4 addresses from Romania. She encouraged ISPs to begin moving to IPv6 now, as RIPE NCC estimates that full transition takes about 2.5 years to complete.
Next up, Klaus Nieminen from the Finnish Communications Continue reading
