Research: Intent Based SDN at ESnet
Demonstration of the ESnet research on a research project using intent based networking including an ontological engine for plain english requests. While this is specific to the ESnet requirements there is some really interesting ideas around interpreting user intent and the architecture of an intent-based system.
The post Research: Intent Based SDN at ESnet appeared first on EtherealMind.
Implementing VXLAN Routing- Arista Networks
Earlier we have so many technologies to do so like we have VPLS, MPLS and OTV( Cisco) in the Datacenter network. But VXLAN is used for the fabric network where you can have end to end tunnels within your LAN network. Now a days if you are looking the enterprise network you will find that VXLAN is used in the Datacenter and Campus networks with the Software defined.
Let's talk about the VXLAN implementation routing on Arista devices. We have two switches connected via core routers and end devices are connected to that switches. In the case of VXLAN you should aware about the three things and these things are
- VLAN : Virtual LAN and i guess everybody knows about it
- VNI: Virtual Network Identifier, VXLAN network identified by a unique VNI is Continue reading
Juniper Vagrant Box Install
Install a Juniper Vagrant boxes with the Virtualbox provider.Arista vEOS Vagrant Box Install
How to install an Arista vEOS Vagrant box.Juniper Vagrant Box Install
This blog covers how to install Juniper boxes for use with Vagrant. This post assumes that you already have a working vagrant install. Plugins Firstly install the Juniper plugins to enable Vagrant to communicate to the boxes correctly. cmd vagrant plugin install vagrant-host-shell...Arista vEOS Vagrant Box Install
This blog covers how to install Arista boxes for use with Vagrant. Although Arista does not provide Vagrant boxes on Vagrant cloud they do provide boxes that can be downloaded from the arista.com website. This post assumes that you already have a working vagrant install. Download Go to the...Using iTerm2 with Cisco VIRL
I love using VIRL to do quick self-check of a config, personal education, and learning the behavior of particular features. I also love using the iTerm2 Terminal Emulator on the Mac. Unfortunately, it isn’t obvious how to make the two play well together. I have had to re-educate myself on this over and over again as I get new computers, mess up my settings and do certain upgrades. I’m pretty sure I copied some of this configuration and the script that I will share from somewhere. So if this looks familiar, reach out to me and I will link back to the source.
This post meant to both share the config and caveats with others as well as to document the nuances for my future reference. In short, there is a standard configuration and a custom configuration for the terminal settings in VIRL’s VMMaestro. These are found in “VMMaestro -> Preferences.”

These settings control whether the built-in (VMMaestro’s client) is used or an external terminal client should be used. I much prefer an external client and iTerm2 is my current client of choice. To eliminate the need of manually launching and connecting, I have customized the Applescript code found below. Continue reading
SD-Access ( Fabric Network, Automation and Analytics LAN ) – Campus Networks
I knew you have some questions around it like
How traffic flows in Campus Network?
What and how fabric works?
Is there VLAN approach works?
Do we need to have SVIs ?
Well take a look into SD-Access approach you will come to know what approach Cisco takes to make it successful in the Campus
SD-Access = Campus Fabric+ DNA Center
Campus Fabric:
Campus Fabric have these three protocols works together to make it excellent way to communicate.
- LISP- Location/Identifier Seperation Protocol- Control Plane
- VXLAN- Virtual Extensible LAN - Data Plane
- Cisco Trustsec- Segmented Tags
Worth Reading: The next generation of whois
The post Worth Reading: The next generation of whois appeared first on rule 11 reader.
IETF Journal July 2017 Issue Available Online Now
The July 2017 issue of the IETF Journal is now online at http://www.ietfjournal.org/journal-issues/july-2017/. With IETF 99 in Prague just over one week away, this is the perfect time to get caught up on what's been happening in the world of Internet standards lately.
Security for Cloud and IoT is a Growing Concern for IT and Executives
 Global cloud security spend predicted to hit $3.5B by 2021.
Global cloud security spend predicted to hit $3.5B by 2021.
API Security Startup Elastic Beam Uses AI to Block Attacks
 The company is likely an acquisition target.
The company is likely an acquisition target.
SDxCentral Weekly News Roundup — July 7, 2017
 China Telecom and Ericsson launch an IoT platform; QualiTest Group acquires Experior Group.
China Telecom and Ericsson launch an IoT platform; QualiTest Group acquires Experior Group.
Apple Engineers Founded SnapRoute, Which Now Helps AT&T
 Nick McKeown helped SnapRoute get off the ground.
Nick McKeown helped SnapRoute get off the ground.
Kubernetes, Swarm, and Mesos Central in Container Orchestration Space
 Kubernetes may have the most users, but it's not considered the de facto standard.
Kubernetes may have the most users, but it's not considered the de facto standard.
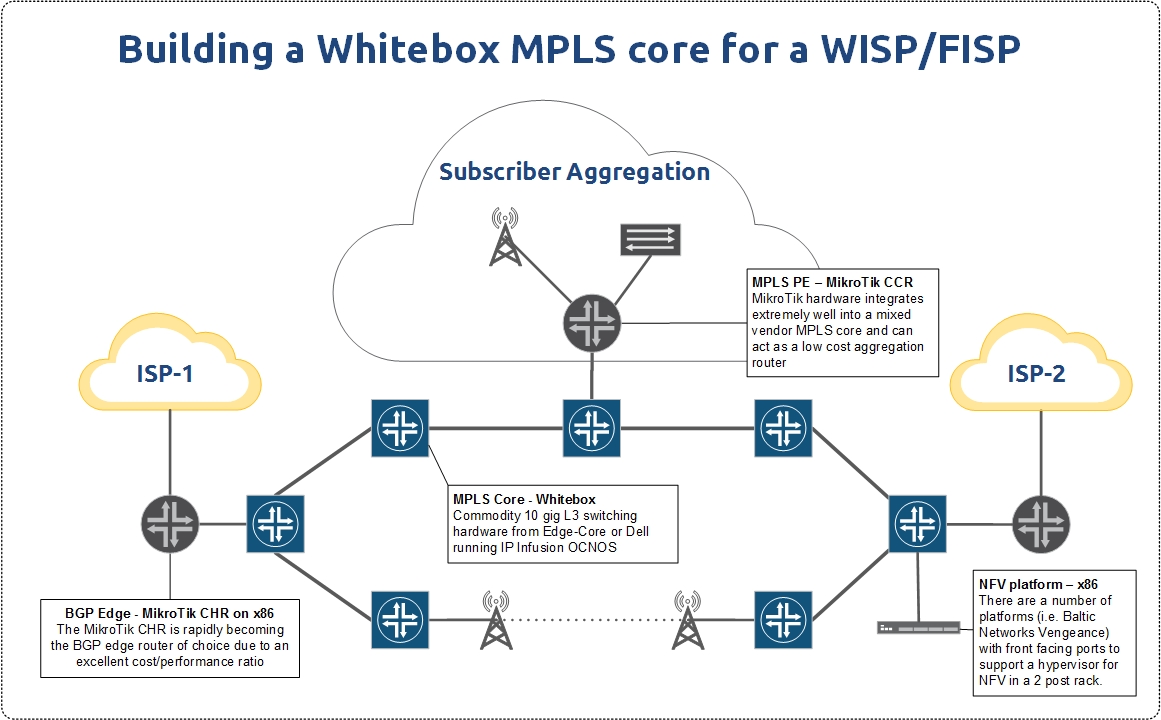
WISP/FISP Design – Building your future MPLS network with whitebox switching.
The role of whitebox in a WISP/FISP MPLS core
Whitebox, if you aren’t familiar with it, is the idea of separating the network operating system and switching hardware into commodity elements that can be purchased separately. There was a good overview on whitebox in this StubArea51.net article a while back if you’re looking for some background.
Lately, in my work for IP ArchiTechs, I’ve had a number of clients interested in deploying IP Infusion with either Dell, Agema or Edge Core switches to build an MPLS core architecture in lieu of an L2 ring deployment via ERPs. Add to that a production deployment of Cumulus Linux and Edge Core that I’ve been working on building out and it’s been a great year for whitebox.
There are a number of articles written that extoll the virtues of whitebox for web scale companies, large service providers and big enterprises. However, not much has been written on how whitebox can help smaller Tier 2 and 3 ISPs – especially Wireless ISPs (WISPs) and Fiber ISPs (FISPs).
And the line between those types of ISPs gets more blurry by the day as WISPs are heavily getting into fiber and FISPs are Continue reading
WISP/FISP Design – Building your future MPLS network with whitebox switching.
The role of whitebox in a WISP/FISP MPLS core
Whitebox, if you aren’t familiar with it, is the idea of separating the network operating system and switching hardware into commodity elements that can be purchased separately. There was a good overview on whitebox in this StubArea51.net article a while back if you’re looking for some background.
Lately, in my work for IP ArchiTechs, I’ve had a number of clients interested in deploying IP Infusion with either Dell, Agema or Edge Core switches to build an MPLS core architecture in lieu of an L2 ring deployment via ERPs. Add to that a production deployment of Cumulus Linux and Edge Core that I’ve been working on building out and it’s been a great year for whitebox.
There are a number of articles written that extoll the virtues of whitebox for web scale companies, large service providers and big enterprises. However, not much has been written on how whitebox can help smaller Tier 2 and 3 ISPs – especially Wireless ISPs (WISPs) and Fiber ISPs (FISPs).
And the line between those types of ISPs gets more blurry by the day as WISPs are heavily getting into fiber and FISPs are Continue reading