How We Measure: RPKI ROA Signing and Route Origination Validation
t APNIC Labs we publish a number of measurements of the deployment of various technologies that are being adopted on the Internet. Here we will look at how we measure the adoption of the signing of Route Origination Attestations (ROAs) as part of the framework for securing inter-domain routing on the Internet using the digital credential framework provided by the Resource Public Key Infrastructure (RPKI).How We Measure: DNSSEC Validation
At APNIC Labs we publish a number of measurements of the deployment of various technologies that are being adopted on the Internet. Here we will look at how we measure the adoption of DNSSEC validation.D2C219: Building A Multi-Cloud Network With A Cloud-Native Approach (Sponsored)
What if you could have a multi-cloud network that was cloud-native, but you didn’t have to know the nitty-gritty details for each of the clouds? That is, you work with a single cloud network interface, and that platform handles the networking so you can focus on things like improving the velocity of application rollouts, architecture, security, and efficiency? Sponsor Prosimo says its platform can do this. On today's show we look under hood to get details on its multi-cloud networking platform.
The post D2C219: Building A Multi-Cloud Network With A Cloud-Native Approach (Sponsored) appeared first on Packet Pushers.
D2C219: Building A Multi-Cloud Network With A Cloud-Native Approach (Sponsored)
What if you could have a multi-cloud network that was cloud-native, but you didn’t have to know the nitty-gritty details for each of the clouds? That is, you work with a cloud network interface, and that platform handles the networking–in a cloud-native way–for you. You wouldn’t need to know the nuances of AWS, Azure, and... Read more »QoS in the Era of Pervasive Video and Edge Apps
With the explosion of edge computing and more mission-critical applications like video and telecalls, is it time to revisit your network quality of service?Open BGP Daemons: There’s So Many of Them
A while ago, the Networking Notes blog published a link to my “Will Network Devices Reject BGP Sessions from Unknown Sources?” blog post with a hint: use Shodan to find how many BGP routers accept a TCP session from anyone on the Internet.
The results are appalling: you can open a TCP session on port 179 with over 3 million IP addresses.
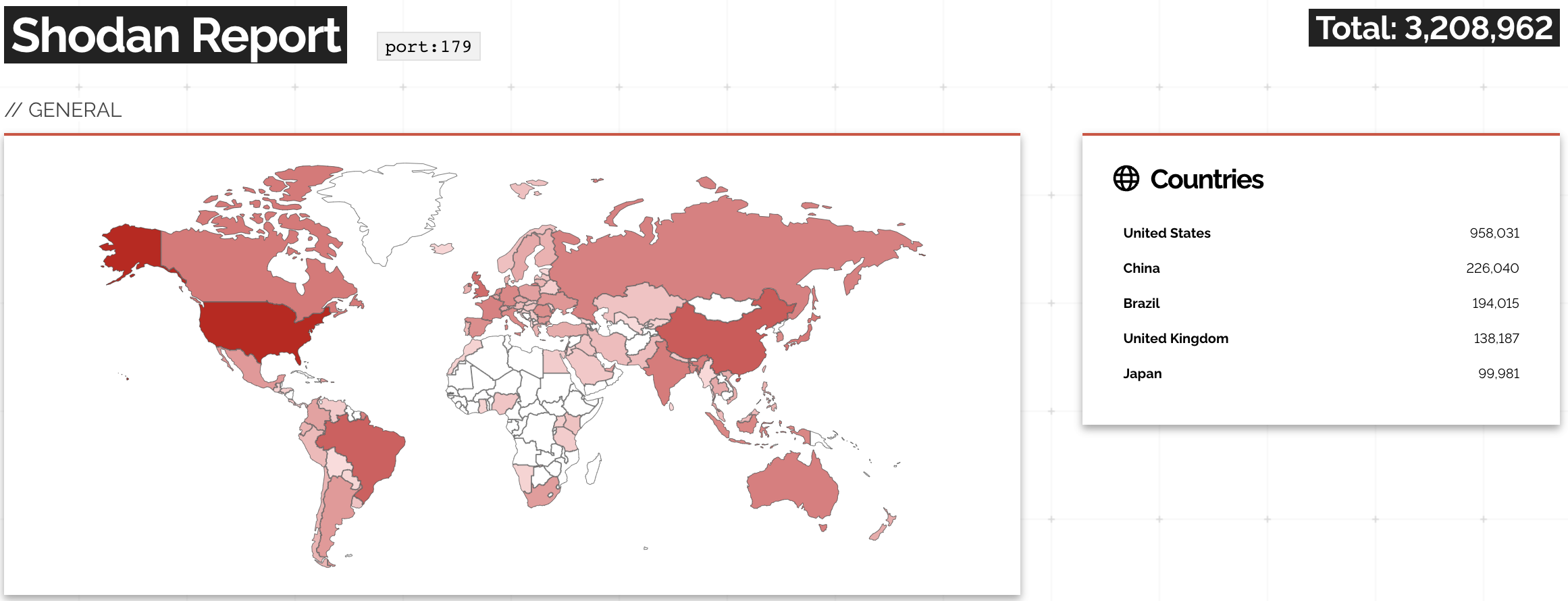
A report on Shodan opening TCP session to port 179
Open BGP Daemons: There’s So Many of Them
A while ago, the Networking Notes blog published a link to my “Will Network Devices Reject BGP Sessions from Unknown Sources?” blog post with a hint: use Shodan to find how many BGP routers accept a TCP session from anyone on the Internet.
The results are appalling: you can open a TCP session on port 179 with over 3 million IP addresses.

A report on Shodan opening TCP session to port 179
MPLS TE Deadlock
The post MPLS TE Deadlock appeared first on Noction.
AI Is Making Data Cost Too Much

You may recall that I wrote a piece almost six years ago comparing big data to nuclear power. Part of the purpose of that piece was to knock the wind out of the “data is oil” comparisons that were so popular. Today’s landscape is totally different now thanks to the shifts that the IT industry has undergone in the past few years. I now believe that AI is going to cause a massive amount of wealth transfer away from the AI companies and cause startup economics to shift.
Can AI Really Work for Enterprises?
In this episode of Packet Pushers, Greg Ferro and Brad Casemore debate a lot of topics around the future of networking. One of the things that Brad brought up that Greg pointed out is that data being used for AI algorithm training is being stored in the cloud. That massive amount of data is sitting there waiting to be used between training runs and it’s costing some AI startups a fortune in cloud costs.
AI algorithms need to be trained to be useful. When someone uses ChatGPT to write a term paper or ask nonsensical questions you’re using the output of the GPT training run. Continue reading
How Data Center Infrastructures Must Change to Support AI
How are enterprises big and small adapting their data center infrastructure to handle AI workloads?Understanding the Role of the Network in Sustainability
Extreme Networks is embracing a multi-pronged sustainability strategy to achieve its environmental objectives for the company itself and its networking solutions.Rapid Progress in BGP Route Origin Validation
In 2022, I was invited to speak about Internet routing security at the DEEP conference in Zadar, Croatia. One of the main messages of the presentation was how slow the progress had been even though we had had all the tools available for at least a decade (RFC 7454 was finally published in 2015, and we started writing it in early 2012).
At about that same time, a small group of network operators started cooperating on improving the security and resilience of global routing, eventually resulting in the MANRS initiative – a great place to get an overview of how many Internet Service Providers care about adopting Internet routing security mechanisms.
Rapid Progress in BGP Route Origin Validation
In 2022, I was invited to speak about Internet routing security at the DEEP conference in Zadar, Croatia. One of the main messages of the presentation was how slow the progress had been even though we had had all the tools available for at least a decade (RFC 7454 was finally published in 2015, and we started writing it in early 2012).
At about that same time, a small group of network operators started cooperating on improving the security and resilience of global routing, eventually resulting in the MANRS initiative – a great place to get an overview of how many Internet Service Providers care about adopting Internet routing security mechanisms.
Getting Aggressive with Cloud Cybersecurity
Cloud cybersecurity should be addressed proactively in order to detect lurking vulnerabilities before threat actors can attack. Here’s what IT leaders need to know to get the upper hand on cloud cybersecurity.Tech Bytes: How VMware And HPE Greenlake Tackle AI And Multi-Cloud For Customers (Sponsored)
VMware and HPE are partnering on HPE Greenlake for VMware Cloud Foundation. On today's episode we discuss how the HPE and VMware partnership benefits customers’ multi-cloud initiatives and how VMware and HPE Greenlake can help customers take advantage of AI by providing scalable hardware and software infrastructure for training and inference. VMware is our sponsor.
The post Tech Bytes: How VMware And HPE Greenlake Tackle AI And Multi-Cloud For Customers (Sponsored) appeared first on Packet Pushers.