Calico Whisker in Action: Reading and Understanding Policy Traces
Kubernetes adoption is growing, and managing secure and efficient network communication is becoming increasingly complex. With this growth, organizations need to enforce network policies with greater precision and care. However, implementing these policies without disrupting operations can be challenging.
That’s where Calico Whisker comes in. It helps teams implement network policies that follow the principle of least privilege, ensuring workloads communicate only as intended. Since most organizations introduce network policies after applications are already running, safe and incremental rollout is essential.
To support this, Calico Whisker offers staged network policies, which allow teams to preview a policy’s effect in a live environment before enforcing it. Alongside this, policy traces in Calico Whisker provide deep visibility into how both enforced and pending policies impact traffic. This makes it easier to understand policy behaviour, validate intent, and troubleshoot issues in real time. In this post, we’ll walk through real-world policy trace outputs and show how they help teams confidently deploy and refine network policies in production Kubernetes clusters.
Kubernetes Network Policy Behaviour
It’s important to reiterate the network policy behaviour in Kubernetes, as understanding this foundation is key to effectively interpreting policy traces and ensuring the right traffic flow decisions are Continue reading
Vector Packet Processor (VPP) dropped packet notifications
Vector Packet Processor (VPP) release 25.10 extends the sFlow implementation to include support for dropped packet notifications, providing detailed, low overhead, visibility into traffic flowing through a VPP router, see Vector Packet Processor (VPP) for performance information.
sflow sampling-rate 10000 sflow polling-interval 20 sflow header-bytes 128 sflow direction both sflow drop-monitoring enable sflow enable GigabitEthernet0/8/0 sflow enable GigabitEthernet0/9/0 sflow enable GigabitEthernet0/a/0The above VPP configuration commands enable sFlow monitoring of the VPP dataplane, randomly sampling packets, periodically polling counters, and capturing dropped packets and reason codes. The measurements are send via Linux netlink messages to an instance of the open source Host sFlow agent (hsflowd) which combines the measurements and streams standard sFlow telemetry to a remote collector.
sflow {
collector { ip=192.0.2.1 udpport=6343 }
psample { group=1 egress=on }
dropmon { start=on limit=50 }
vpp { }
}The /etc/hsflowd.conf file above enables the modules needed to receive netlink messages from VPP and send the resulting sFlow telemetry to a collector at 192.0.2.1. See vpp-sflow for detailed instructions.
docker run -p 6343:6343/udp sflow/sflowtoolRun sflowtool on the sFlow collector host to verify verify that the data is being received and Continue reading
New Project: Open-Source VXLAN/EVPN Labs
After launching the BGP labs in 2023 and IS-IS labs in 2024, it was time to start another project that was quietly sitting on the back burner for ages: open-source (and free) VXLAN/EVPN labs.
The first lab exercise is already online and expects you to extend a single VLAN segment across an IP underlay network using VXLAN encapsulation with static ingress replication.
TCG061: How Are You Using AI?
Join William Collins and Evyonne Sharp as they catch up on all things AI. They discuss the AI bubble and how it relates to venture capital, stock, and company evaluations. They talk about the AI experience for the average person, the adoption rate of AI tools, and how the AI infrastructure buildout might affect the... Read more »AI Is Just A Majordomo

The IT world is on fire right now with solutions to every major problem we’ve ever had. Wouldn’t you know it that the solution appears to be something that people are very intent on selling to you? Where have I heard that before? You wouldn’t know it looking at the landscape of IT right now but AI has iterated more times than you can think over the last couple of years. While people are still carrying on about LLMs and writing homework essays the market has moved on to agentic solutions that act like employees doing things all over the place.
The result is people are more excited about the potential for AI than ever. Well, that is if you’re someone that has problems that need to be solved. If you’re someone doing something creative, like making art or music or poetry you’re worried about what AI is going to do to your profession. That divide is what I’ve been thinking about for a while. I don’t think it should come as a shock to anyone but I’ve figured out why AI is hot for every executive out there.
AI appeals to people that have someone doing work for them.
Continue reading
NAN104: The Art and Science of Writing a Network Automation Book
Host Eric Chou talks with Jeff Kala, co-author of the newly released “Network Automation Cookbook 2nd Edition,” to discuss his book and the experiences that led him from networking to network automation author. They discuss Jeff’s learning style and why it was helpful when working on his book. Lastly, they dig into Jeff’s predictions on... Read more »Worth Reading: AI for Network Managers
Pat Allen wrote an interesting guide for managers of networking teams dealing with the onslaught of AI (HT: PacketPushers newsletter).
The leitmotif: use AI to generate a rough solution, then review and improve it. That makes perfect sense and works as long as we don’t forget we can’t trust AI, assuming you save time doing it this way.
5 Essential Steps to Strengthen Kubernetes Egress Security
Securing what comes into your Kubernetes cluster often gets top billing. But what leaves your cluster, outbound or egress traffic, can be just as risky. A single compromised pod can exfiltrate data, connect to malicious servers, or propagate threats across your network. Without proper egress controls, workloads can reach untrusted destinations, creating serious security and compliance risks. This guide breaks down five practical steps to strengthen Kubernetes egress security, helping teams protect data, enforce policies, and maintain visibility across clusters.
Why Egress Controls Matter
|
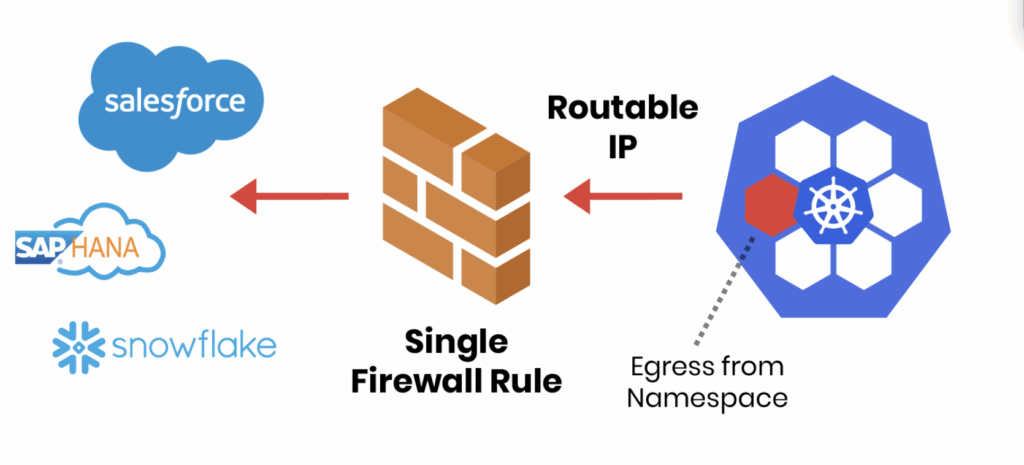
Your Kubernetes Egress Security Checklist
To help teams tackle this challenge, we’ve put together a Kubernetes Egress Security Checklist, based on best practices from real-world Continue reading
HS115: Cyber-Risk Assessment and Cybersecurity Budgeting: You’re (Probably) Doing It Wrong
To understand how much to spend on cybersecurity, you have to accurately assess or quantify your risks. Too many people still peg their cybersecurity spend to their IT budget; that is, they’ll look at what they’re spending on IT, and then allocate a percentage of that to cybersecurity. That may have made some sense when... Read more »Some Notes from RIPE-91
The 91st meeting of the RIPE community was held in Bucharest in October this year. It was a busy week and, as usual, there were presentations on a wide variety of topics, including routing, the DNS, network operations, security, measurement and address policies. The following are some notes on presentations that I found to be of interest to me.OMG: Automatic OSPFv3 Router ID on Cisco IOS
Found this incredible gem1 hidden in the Usage Guidelines for the OSPFv3 router-id configuration command part of the Cisco IOS IPv6 reference guide.
The whole paragraph seems hallucinated2, but that couldn’t be because the page was supposedly last updated in 2019, and LLMs weren’t good enough to write well-structured nonsense at that time:
OSPFv3 is backward-compatible with OSPF version 2.
No, it is not.
NB549: Startups Take on Switch, ASIC Incumbents; Google Claims Quantum Advantage
Take a Network Break! Companies spying on…I mean, monitoring…their employees via software called WorkExaminer should be aware of a login bypass that needs to be locked down. On the news front, we opine on whether it’s worth trying to design your way around AWS outages, and speculate on the prospects of a new Ethernet switch... Read more »Tech Bytes: Why Equinix Should Be Part of Your AI Network Strategy (Sponsored)
AI infrastructure conversations tend to be dominated by GPUs, data center buildouts, and power and water consumption. But networks also play a crucial role, whether to support huge file transfers to a compute cluster, stream telemetry from edge locations to feed AI pipelines, or provide high-speed, low latency connectivity for AI agents. On today’s Tech... Read more »Adding a Syslog Server to a netlab Lab Topology
netlab does not support a Syslog server (yet), but it’s really easy to add one to your lab topology, primarily thanks to the Rsyslog team publishing a ready-to-run container. Let’s do it ;)
Adding a Syslog Server
Rsyslog is an open-source implementation of a Syslog server (with many bells and whistles, most of which we won’t use) that can (among other things) log incoming messages to a file. Even better (for our use case), the Rsyslog team regularly publishes Rsyslog containers; we’ll use the rsyslog/rsyslog-collector container because it can “receive logs via UDP, TCP, and optionally RELP, and can send them to storage backends or files.”
A Unified ARP Table (and how to get one when you don’t have one)
How to get one when you don't have one and what happens when its gone! There is so much propaganda out there today (and I am not even referring to politics), it feels good to go back to fundamentals. Few things are more foundational to networking than Address Resolution Protocol (ARP). It is inconceivable to READ MORE
The post A Unified ARP Table (and how to get one when you don’t have one) appeared first on The Gratuitous Arp.
Network Labs on a Budget

"Can you suggest some specs for a server for my network labs?" is probably the question I get asked the most. People reach out all the time asking for recommendations. The thing is, I never really know their exact situation or what they’re trying to do in their lab. So, I usually just share what I have and what worked best for me, and let them decide what fits their setup.
In this post, I’ll go over the cheapest way to build your own network lab without spending too much.
What We Will Cover?
- Buying a used mini PC
- Proxmox as the hypervisor (optional)
- Linux as a VM
- Containerlab/Netlab, EVE-NG, Cisco CML
- Proxmox Backup Server (optional)
- Simplest Option for Absolute Beginners

TL;DR
You don’t need expensive hardware to build a solid network lab. A used mini PC with decent specs is more than enough to run tools like Proxmox, Continue reading
Contributing to NTC templates
This guide is the steps I follow when adding or updating NTC templates. Contributing to a project in Github is still a learning curve for me, the days of learning CLI by repetition seem long gone so when using or contributing to any of these NetOps type tools I have to keep guides as it is a bit of a struggle to remember with so many new and alien things to know and the sporadic nature that I use them.
The strange webserver hot potato — sending file descriptors
I’ve previously mentioned my io-uring webserver tarweb. I’ve now added another interesting aspect to it.
As you may or may not be aware, on Linux it’s possible to send a file descriptor from one process to another over a unix domain socket. That’s actually pretty magic if you think about it.
You can also send unix credentials and SELinux security contexts, but that’s a story for another day.
My goal
I want to run some domains using my webserver “tarweb”. But not all. And I want to host them on a single IP address, on the normal HTTPS port 443.
Simple, right? Just use nginx’s proxy_pass?
Ah, but I don’t want nginx to stay in the path. After SNI (read: “browser saying which domain it wants”) has been identified I want the TCP connection to go directly from the browser to the correct backend.
I’m sure somewhere on the internet there’s already an SNI router that does this, but all the ones I found stay in line with the request path, adding a hop.
Why?
A few reasons:
- Having all bytes bounce on the SNI router triples the number of total file descriptors for the connection. (one on the backend, Continue reading
What’s New in Calico v3.31: eBPF, NFTables, and More
We’re excited to announce the release of Calico v3.31,  which brings a wave of new features and improvements.
which brings a wave of new features and improvements.
For a quick look, here are the key updates and improvements in this release:
- Calico NFTables Dataplane is now Generally Available
- Calico eBPF Dataplane Enhancements
- Simplified installation: new template defaults to
eBPF, automatically disableskube-proxyviakubeProxyManagementfield, and addsbpfNetworkBootstrapfor auto API endpoint detection. - Configurable cgroupv2 path: support for immutable OSes (e.g., Talos).
- >>Learn More: See how Calico v3.31 makes eBPF installation frictionless and simplifies setup in our Zero-Trust with Zero-Friction eBPF in Calico v3.31 blog
- Simplified installation: new template defaults to
- Calico Whisker (Observability Stack)
- Improved UI and performance in Calico v3.31.
- New policy trace categories: Enforced vs Pending.
- Lower memory use, IPv6 fixes, and more efficient flow streaming.
- Networking & QoS
- New bandwidth and packet rate QoS controls across all dataplanes.
- DiffServ (
DSCP) support: prioritize traffic by marking packets (e.g.,EFfor VoIP). - Introduces new
QoSPolicyAPI for declarative traffic control.
- Encapsulation & Routing
- Tech Preview: Felix now handles encapsulation routes (
IP-in-IP,no-encap) directly — no BIRD required!
- Tech Preview: Felix now handles encapsulation routes (
- NAT Control
- New
natOutgoingExclusionsconfig for granular NAT management. - Choose between
Continue reading
- New

