Arista Hoards Inventory During Cisco Litigation
 Its Q2 earnings were impressive.
Its Q2 earnings were impressive.
Google Open Sources Its 48V Data Center Rack
 Bridging the transition to (and Google's desire for) 48-volt racks.
Bridging the transition to (and Google's desire for) 48-volt racks.
Forensics Challenge for CSIRT Team – Part 2 Solution
The goal of the tutorial is to provide a solution to the forensic challenge game that I created for testing forensic skills of CSIRT team. Please be careful and run a suspicious binary file located inside a provided virtual machine only in a secured environment in order to avoid unwanted damage or loss.
As you can notice, some files are being encrypted right after boot of a virtual machine. All these files have suffix .enc001. You can easily located them with the command:
$ find / -name "*.enc001" -type f 2>/dev/null
There is also a file named encryption_warning.txt located in a home directory of an actual user and it contains a following warning message.
*** Your files have been encrypted! ***
*** To decrypt them, run '/usr/local/bin/ls %1a%your_decryption_key ***
Without any doubts a utility ls is not a cryptography tool so it is a good place where we can start our investigation. The command /usr/local/bin/ls -la shows files in a actual directory.
ubuntu@ubuntu:~$ /usr/local/bin/ls -la
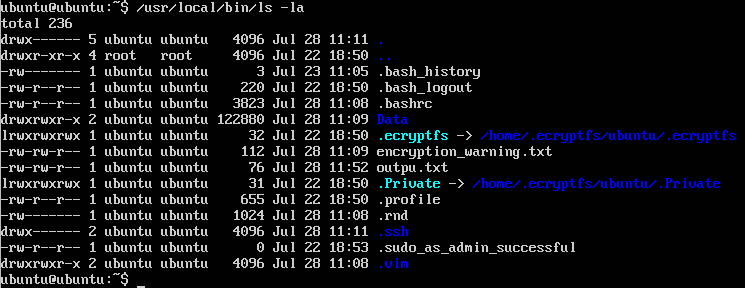
Picture 1 - Content of Actual Directory
The output looks good. But what does happen if we display a non-existing file kdkdkdkdk?
ubuntu@ubuntu:~$ /usr/local/bin/ls kdkdkdkdk
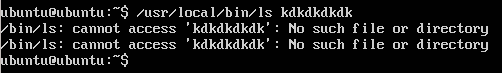
Picture 2 - Two Error Messages
They are two interesting facts shown in the output of the command /usr/local/bin/ls . Firstly, two Continue reading