Migrating to BGP
The post Migrating to BGP appeared first on Noction.
MIT WiFi Technology Promises Precise Location Tracking
Researchers develop Chronos, a new method for determining the location of WiFi devices with decimeter accuracy.
Strain relief
I’ve got a problem with sagging cables, and I’ve got a simple solution. Examine the side-by-side images below which show the same fiber connection between a switch and a firewall. The image on the left shows a sagging cable which crosses in front of … Continue reading
The post Strain relief appeared first on The Network Sherpa.
Strain relief
I’ve got a problem with sagging cables, and I’ve got a simple solution. Examine the side-by-side images below which show the same fiber connection between a switch and a firewall. The image on the left shows a sagging cable which crosses in front of the switch in the rack unit just below it.
As you may know, this cabling install is a violation of the 167th rule of networking:
Thou shalt contain your cables to your own rack unit and shalt not, under any circumstances, impede access to other rack units or blades.
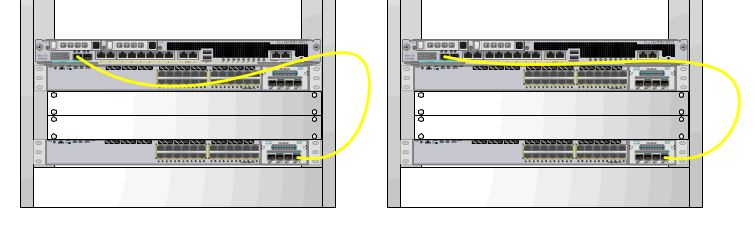 The image on the right ticks the box for me. There’s no room for a dedicated 1RU horizontal cable manager, but there is room for a zero-RU strain relief bar (as seen below). The result is a relatively neat cabling job. It’s no work of art, but it’s functional.
The image on the right ticks the box for me. There’s no room for a dedicated 1RU horizontal cable manager, but there is room for a zero-RU strain relief bar (as seen below). The result is a relatively neat cabling job. It’s no work of art, but it’s functional.
 A strain-relief bar is a cheap metal bar that you can bolt on when you rack-mount your switch. It allows you to velcro your fiber patches to the bar, taking the strain to help prevent breaks and preventing the dreaded cable droop. You should, of course, take care to ensure you don’t block access to any field-replaceable units, cards or ports on your network device.
A strain-relief bar is a cheap metal bar that you can bolt on when you rack-mount your switch. It allows you to velcro your fiber patches to the bar, taking the strain to help prevent breaks and preventing the dreaded cable droop. You should, of course, take care to ensure you don’t block access to any field-replaceable units, cards or ports on your network device.
The strain-relief bar Continue reading
Building a L2 Fabric on top of VXLAN: Arista or Cisco?
One of my readers working as an enterprise data center architect sent me this question:
I've just finished a one-week POC with Arista. For fabric provisioning and automation, we were introduced to CloudVision. My impression is that there are still a lot of manual processes when using CloudVision.
Arista initially focused on DIY people and those people loved the tools Arista EOS gave them: Linux on the box, programmability, APIs… However
Read more ...31 – Multiple approaches interconnecting VXLAN Fabrics
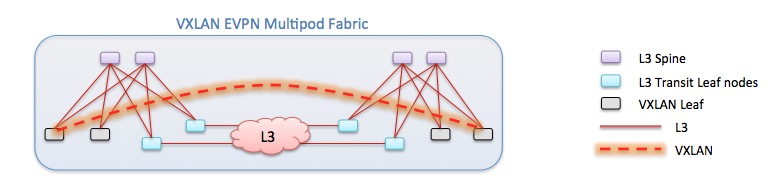
As discussed in previous articles, VXLAN data plane encapsulation in conjunction with its control plane MP-BGP AF EVPN is becoming the foremost technology to support the modern network Fabric.
It is therefore interesting to clarify how to interconnect multiple VXLAN/EVPN fabrics geographically dispersed across different locations.
Three approaches can be considered:
| The 1st option is the extension of multiple sites as one large single stretched VXLAN Fabric. There is no network overlay boundary per se, nor VLAN hand-off at the interconnection, which simplifies operations. This option is also known as geographically dispersed VXLAN Multiple PoD. However we should not consider this solution as a DCI solution as there is no demarcation, nor separation between locations. Nonetheless this one is very interesting for its simplicity and flexibility. Consequently we have deeply tested and validated this design. |
- The second option to consider is multiple VXLAN/EVPN-based Fabrics interconnected using a DCI Layer 2 and layer 3 extension. Each greenfield DC located on different site is deployed as an independent fabric, increasing autonomy of each site and enforce global resiliency. This is often called Multisite. A Data Center Interconnect technology (OTV, VPLS, PBB-EVPN, or even VXLAN/EVPN) is therefore used to extend Layer 2 and Layer Continue reading