Monitoring CPU on firewalls
There is a trend in network monitoring toward Push Model (versus Pull Model) where network devices send metrics to a collector in a ‘netflow’ like fashion (read blog post of Matt Oswalt). It is up to the collector to interpret that data; no need to standardize what is being sent. The only agreement is on data format […]
The post Monitoring CPU on firewalls appeared first on Packet Pushers.
Monitoring CPU On firewalls
There is a trend in network monitoring toward Push Model (versus Pull Model) where network devices send metrics to a collector in a ‘netflow’ like fashion (read blog post of Matt Oswalt). It is up to the collector to interpret that data; no need to standardize what is being sent. The only agreement is on data format […]
The post Monitoring CPU On firewalls appeared first on Packet Pushers.
Network Monitoring And Advanced Analytics
EMA study shows that network pros are applying analytics to network data for security and other purposes.
What Are The Problems with Broadcom Tomahawk? We Don’t Know
One of my readers has customers that already experienced performance challenges with Tomahawk-based data center switches. He sent me an email along these lines:
My customers are concerned about buffer performance for packets that are 200 bytes and under. MORE IMPORTANTLY, a customer informed me that there were performance issues when running 4x25GE connections when one group of ports speaks to another group.
Reading the report Mellanox published not so long ago it seems there really is something fishy going on with Tomahawk.
Read more ...The LTE-U Vs. WiFi Debate
If carriers use unlicensed spectrum, it may not be the WiFi disaster that some expect.
Introducing HTTP Testing in ToDD
Now that ToDD has been in the public arena for two months, one of the things I’m happiest about is the fact that testing in ToDD is totally flexible. Thanks to the concept of testlets, ToDD doesn’t have an opinion on the specifics of your tests - all of that logic is contained within the testlet.
I believe there’s real value in going further than simple “ping” tests when validating that your network is working as you expect. Customers aren’t pinging you - they’re using your applications. To that end, I have introduced a new testlet to the ToDD project that makes HTTP calls and reports on application-level metrics.
There are some very real advantages to testing HTTP reachability instead of settling for simple “ping” tests. In addition to verifying network connectivity, HTTP testing also ensures that the web application is also up and able to produce the desired status code. We’re also able to get some insight into performance at the application level.
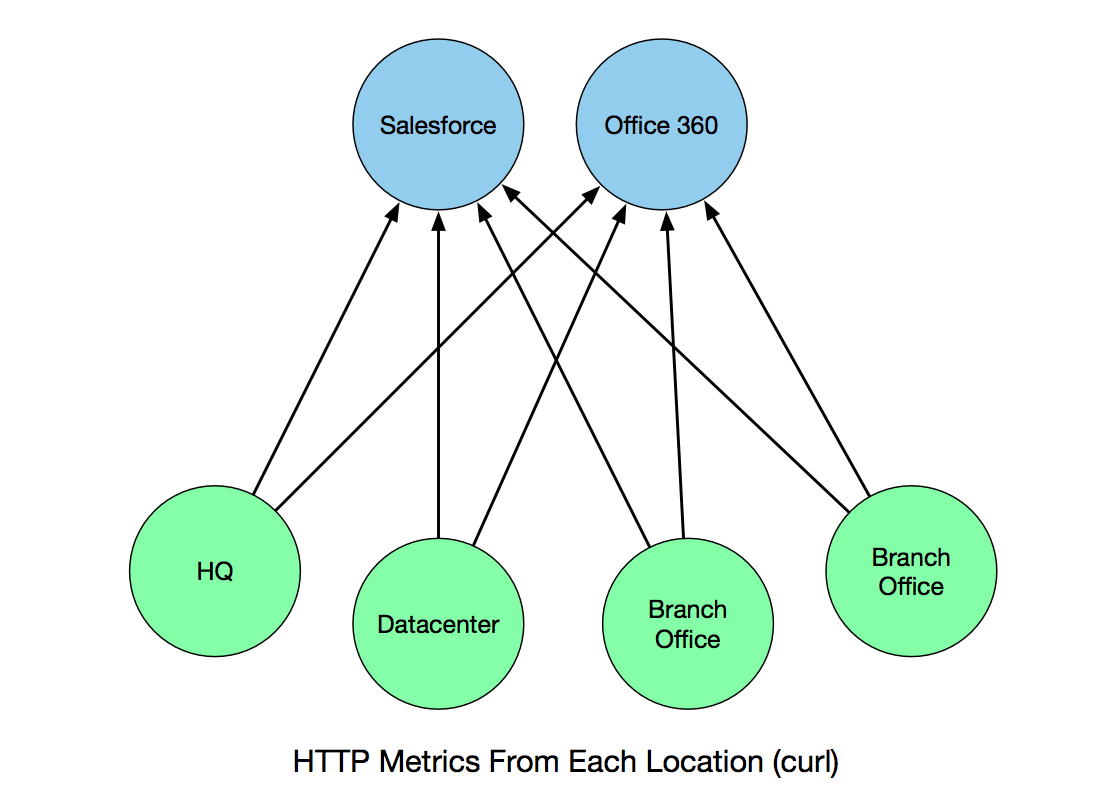
In my initial presentations on ToDD, I talked about a use case for being able to “keep your SaaS providers honest” by making HTTP requests against the services you use in a distributed manner:
The Continue reading
Introducing HTTP Testing in ToDD
Now that ToDD has been in the public arena for two months, one of the things I’m happiest about is the fact that testing in ToDD is totally flexible. Thanks to the concept of testlets, ToDD doesn’t have an opinion on the specifics of your tests - all of that logic is contained within the testlet.
I believe there’s real value in going further than simple “ping” tests when validating that your network is working as you expect. Customers aren’t pinging you - they’re using your applications. To that end, I have introduced a new testlet to the ToDD project that makes HTTP calls and reports on application-level metrics.
There are some very real advantages to testing HTTP reachability instead of settling for simple “ping” tests. In addition to verifying network connectivity, HTTP testing also ensures that the web application is also up and able to produce the desired status code. We’re also able to get some insight into performance at the application level.
In my initial presentations on ToDD, I talked about a use case for being able to “keep your SaaS providers honest” by making HTTP requests against the services you use in a distributed manner: