Coriant SDN Controller: Lower Layers Say ‘Howdy’ to Higher Layers
 A Coriant CTO says the YANG model is key to its controller enhancements.
A Coriant CTO says the YANG model is key to its controller enhancements.
Paving The Way For SDN Interoperability
Two new abstraction frameworks ensure interoperability between OpenFlow v.3-enabled hardware-based switches from different vendors.Single RX queue kernel bypass in Netmap for high packet rate networking
In a previous post we discussed the performance limitations of the Linux kernel network stack. We detailed the available kernel bypass techniques allowing user space programs to receive packets with high throughput. Unfortunately, none of the discussed open source solutions supported our needs. To improve the situation we decided to contribute to the Netmap project. In this blog post we'll describe our proposed changes.
CC BY-SA 2.0 image by Binary Koala
Our needs
At CloudFlare we are constantly dealing with large packet floods. Our network constantly receives a large volume of packets, often coming from many, simultaneous attacks. In fact, it is entirely possible that the server which just served you this blog post is dealing with a many-million packets per second flood right now.
Since the Linux Kernel can't really handle a large volume of packets, we need to work around it. During packet floods we offload selected network flows (belonging to a flood) to a user space application. This application filters the packets at very high speed. Most of the packets are dropped, as they belong to a flood. The small number of "valid" packets are injected back to the kernel and handled in the same way Continue reading
AWS IoT vs Cisco Fog Computing – Cloud vs Network IoT
Amazon Internet of Things PaaS platform was announced yesterday with the buzz line "Cloud Services for Connected Devices". I am comparing the strategic differences with Cisco Fog Computing.
The post AWS IoT vs Cisco Fog Computing – Cloud vs Network IoT appeared first on EtherealMind.
Corporate VPNs In The Bullseye
Two newly discovered attacks targeted at corporate VPNs demonstrate how attackers can abuse and use these networks for their own purposes.Enterprise Content-over-IPv6 Deployment Scenarios
After ARIN ran out of IPv4 address space (in a totally uncontrolled “let’s party till it’s over” way) US enterprise IT shops (RFC 6919) OUGHT TO learn how to spell IPv6 (US service providers are already ahead of the pack).
You may also decide to ignore IPv6 indefinitely, but do keep in mind that consultants love panicking clients.
Read more ...Risky Business #386 — Katie Moussouris on the (groan) disclosure debate
On this week's show we're checking in with Katie Moussouris of HackerOne. She's an ex Microsoftie who's spent something like a decade working on vulnerability disclosure policies. She even helped get a vuln disclosure ISO standard ratified!
And she'll be joining us this week to discuss disclosure politics, I guess you'd call it... for those of us who've been around infosec for a while, most of us would rather stick our face in a blender than talk about it, but Katie will be along to point out why people should fight their "disclosure debate fatigue" and get involved.
Brocade BNA API
Brocade Network Advisor (BNA) has a REST API for accessing Fibre Channel-related data. The documentation includes a sample Python script showing how to connect to the API to retrieve Fabric info. The script given only works with Python 3.x. It’s also a pain to copy out of the documentation as you end up with a few extra characters in there. Here’s a version that will work with Python 2.7. I’ve also made a few other modifications – in this one, you can set the BNA IP, Username & Password at the top of the script. I’ve also made it PEP8-compliant.
#!/usr/bin/env python
import httplib
import json
import sys
BNAServer = "10.200.5.181"
BNAUsername = "Administrator"
BNAPassword = "password"
# Create HTTPConnection object and connect to the server.
connection = httplib.HTTPConnection(BNAServer)
###########################
# Log in to Network Advisor
###########################
# Send login request
connection.request(
'POST',
'/rest/login',
headers={
"WSUsername": BNAUsername,
"WSPassword": BNAPassword,
"Accept": "application/vnd.brocade.networkadvisor+json;version=v1"}
)
print()
print("Sending login request to Network Advisor...")
# Get the response
response = connection.getresponse()
# Display the response status print()
print ("Status= ", response.status)
# If successful (status = 200), display the returned session token
if response.status Continue reading
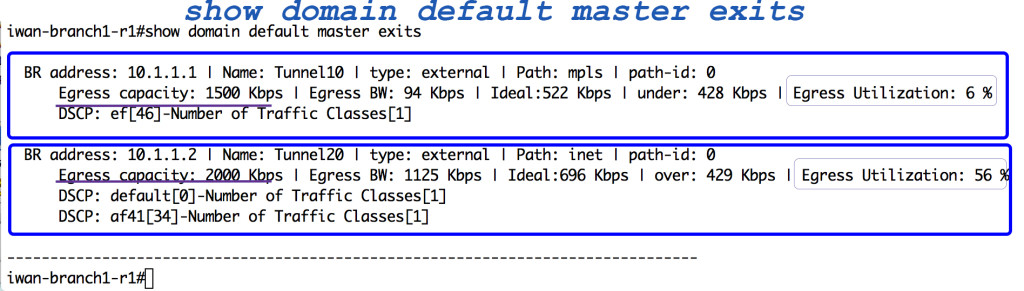
Intelligent Bandwidth Decisions at the WAN Edge
Business Critical Applications and Intelligent Decision Making at the WAN Edge….. these are the things I’ve been focusing on in the past few blogs. To me, PfRv3 and DMVPN are the dynamic duo of Cisco’s IWAN that help you learn about and avoid impairments (delay, loss, jitter) along the path that business critical traffic takes.
Let’s take this even further though. How else can IWAN’s Intelligent Path Control help us apply the mentality of the 7Ps (“Prior proper preparation prevents piss poor performance”) to our network and to business critical traffic?
Knowledge… information gathering… awareness. These are the first steps. Once you have the knowledge you can make intelligent decisions based on that knowledge at the WAN edge.
What knowledge?  How about the bandwidth of your WAN links? Wouldn’t it be nice to have facts, such as what their current bandwidth utilization is, be a part of the Intelligent decision making at the WAN edge?
How about the bandwidth of your WAN links? Wouldn’t it be nice to have facts, such as what their current bandwidth utilization is, be a part of the Intelligent decision making at the WAN edge?
We can do that for you now. We can use what your current egress utilization is on your WAN links in the intelligent decision making process that PfRv3 does for you at Continue reading
MikroTik CCR1072-1G-8S+ Review – Part 3 – 80 Gbps Throughput testing
[adrotate banner=”5″]
[metaslider id=249]
The 80 Gbps barrier has finally been broken (and yes we are rounding up) !!!!
Well at least it has been reached by someone other than MikroTik. It’s taken us quite a while to get all the right pieces to push 80 Gbps of traffic through the CC1072 but with the latest round of servers that just got delivered to our lab, we were able to go beyond our previous high water mark of 54 Gbps all the way to just under 80 Gbps. There have been a number of questions about this particular router and what the performance will look like in the real world. While this is still a lab test, we are using non-MikroTik equipment and iperf which is considered an extremely accurate performance measuring tool for TCP and UDP.
Video of the CCR1072-1G-8S+ in action (Turn up your volume to hear the roar of the ESXi servers as they approach 80 Gbps)
How we did it – The Hardware
CCR1072-1G-8S+ – Obviously you can’t have a test of the CCR1072 without one to test on. Our CCR1072-1G-8S+ is a pre-production model so there are some minor differences between it and the Continue reading
MikroTik CCR1072-1G-8S+ Review – Part 3 – 80 Gbps Throughput testing
[adrotate banner=”5″]
[metaslider id=249]
The 80 Gbps barrier has finally been broken (and yes we are rounding up) !!!!
Well at least it has been reached by someone other than MikroTik. It’s taken us quite a while to get all the right pieces to push 80 Gbps of traffic through the CC1072 but with the latest round of servers that just got delivered to our lab, we were able to go beyond our previous high water mark of 54 Gbps all the way to just under 80 Gbps. There have been a number of questions about this particular router and what the performance will look like in the real world. While this is still a lab test, we are using non-MikroTik equipment and iperf which is considered an extremely accurate performance measuring tool for TCP and UDP.
Video of the CCR1072-1G-8S+ in action (Turn up your volume to hear the roar of the ESXi servers as they approach 80 Gbps)
How we did it – The Hardware
CCR1072-1G-8S+ – Obviously you can’t have a test of the CCR1072 without one to test on. Our CCR1072-1G-8S+ is a pre-production model so there are some minor differences between it and the Continue reading
Xirrus Offers New Security Option For Public Wi-Fi
Xirrus is launching a new security feature to encrypt wireless connections between a device and an AP on a public Wi-Fi network. While it's easy to use, it does have limitations.
The post Xirrus Offers New Security Option For Public Wi-Fi appeared first on Packet Pushers.