Can We Shrink (or Eliminate) VMs to Suit Containers?
![]() VMs can help the container cause, but there's room for improvement, say speakers at OpenStack Silicon Valley.
VMs can help the container cause, but there's room for improvement, say speakers at OpenStack Silicon Valley.
Why Cisco?
Why do i keep focusing so much on Cisco, when there are clearly alot of different vendors out there with similar products and technologies?
There are several reasons for this.
1) I began the professional part of my networking career with Cisco.
2) Cisco has a proven track record when it comes to education and learning.
3) Even though not always the best match for all use-cases, Cisco is a big player in almost all areas of networking.
4) The networking opportunities provided by Cisco is by far the best of what ive seen. Take for example the Cisco Learning Network.
5) Cisco Press is really awesome in my opinion. They have alot of really high quality books out there.
6) Great opportunities to interact with the company. By this i mean to participate in programs like Cisco Champions and different SME (Subject Matter Expert) related activities.
7) Cisco documentation is not perfect, but its hands down the best I’ve seen across multiple vendors.
8) And ofcourse Cisco Live! 
That being said, recently i have begun to take a more neutral look at technologies. The reason being, that in this day and age, proprietary technologies become less prefered than open Continue reading
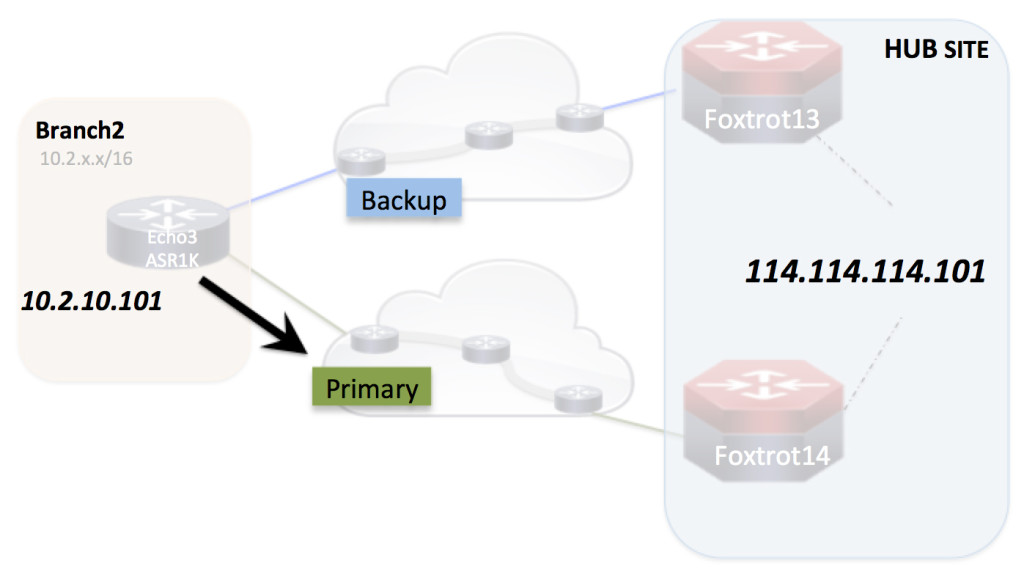
IWAN’s “Intelligent Path Control” & Using Your Backup Link
The blog I was going to post today was a blog about how PfRv3 (IWAN’s “Intelligent Path Control”) utilizes the GRE tunnel of the DMVPN underlay in order to make intelligent decisions about where to send business critical traffic based on knowledge of the health of the path that business critical traffic would take. …… But then I started realizing that while I have dug into a lot of DMVPN stuff recently on “Networking With Fish”…. I have not even really touched “Intelligent Path Control”. So……. let’s take a giant step backward.
“Intelligent Path Control” at the WAN – what can it do for you and why do you want it? In this blog I’m not going to try to be the definitive all encompassing guide of what all “Intelligent Path Control” is…. just enough to get us a little on the same page before we start “playing in the lab together” with it in future blogs.
The picture above is of a typical 1 router branch location with 2 WAN connections. One WAN connection is the primary and the other one sits there, unused, as just a backup … doing nothing Continue reading
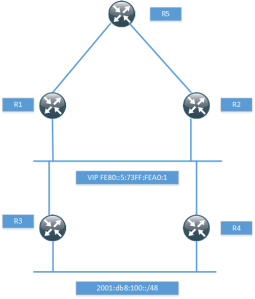
Busting Myths – IPv6 Link Local Next Hop into BGP
In some publications it is mentioned that a link local next-hop can’t be used when redistributing routes into BGP because routers receiving the route will not know what to do with the next-hop. That is one of the reason why HSRPv2 got support for global IPv6 addresses. One such scenario is described in this link.
The topology used for this post is the following.
I have just setup enough of the topology to prove that it works with the next-hop, so I won’t be running any pings and so on. The routers R1 and R2 have a static route for the network behind R3 and R4.
ipv6 route 2001:DB8:100::/48 GigabitEthernet0/1 FE80::5:73FF:FEA0:1
When routing towards a link local address, the exit interface must be specified. R1 then runs BGP towards R5, notice that I’m not using next-hop-self.
router bgp 100 bgp router-id 1.1.1.1 bgp log-neighbor-changes neighbor 2001:DB8:1::5 remote-as 100 ! address-family ipv6 redistribute static neighbor 2001:DB8:1::5 activate exit-address-family
If we look in the BGP RIB, we can see that the route is installed with a link local next-hop.
R1#sh bgp ipv6 uni BGP table version is 2, local router ID is 1.1.1.1 Status codes: s suppressed, Continue reading
Don’t Optimize the Last 5%
Robin Harris described an interesting problem in his latest blog post: while you can reduce the storage access time from milliseconds to microseconds, the whole software stack riding on top still takes over 100 milliseconds to respond. Sometimes we’re optimizing the wrong part of the stack.
Any resemblance to SDN in enterprises or the magical cost-reduction properties of multi-vendor data center fabrics is obviously purely coincidental.
Yet Another new BGP NLRI: BGP-LS
Yes, that’s right, we have another new BGP NLRI: BGP-LS. In this post we will be looking at BGP with Link State (LS) extension which is an integral part of the Carrier SDN strategy. We will look at why we need BGP-LS, its internals and its applications. What I won’t cover is things like do we need SDN?, […]
The post Yet Another new BGP NLRI: BGP-LS appeared first on Packet Pushers.
Must Read: James Mickens on Security
A link on Bruce Schneier’s blog pointed me to the latest article by the truly awesome James Mickens, this time making great fun of security researchers. Exactly what you need with your coffee on a Saturday morning. Enjoy!
SDxCentral Weekly News Roundup — August 28, 2015
 VMware shuffles execs and ponders vCloud Air's future, all in advance of VMworld.
VMware shuffles execs and ponders vCloud Air's future, all in advance of VMworld.
Just How Big Is The SD-WAN Market? And Should We Care?
Incumbents and startups alike are rushing into the SD-WAN market. So how much of an opportunity is there? So far, the data points aren't very good. And maybe they don't matter anyway.
The post Just How Big Is The SD-WAN Market? And Should We Care? appeared first on Packet Pushers.
Mirantis CEO Says OpenStack Is Getting Real
![]() AT&T's massive NFV cloud is among a growing number of production OpenStack deployments, Adrian Ionel says.
AT&T's massive NFV cloud is among a growing number of production OpenStack deployments, Adrian Ionel says.
iPexpert’s Newest “CCIE Wall of Fame” Additions 8/28/2015
Please join us in congratulating the following iPexpert students who have passed their CCIE lab!
This Week’s CCIE Success Stories
- Mohan Mayilraj, CCIE #49942 (Data Center)
- Zahari Georgiev, CCIE #49996 (Wireless)
- Mohamed Enassiri, CCIE #46237 (Collaboration)
This Week’s Testimonial
Mohan Mayilraj CCIE #49942 (Data Center)
Thank you very much for help reach my goal. Your video and training and Boot camp helped lot and your proctor lab is gem and very much useful and I used your lab most of time and workbook.This is my first attempt on CCIE. I got through it .
We Want to Hear From You!
Have you passed your CCIE lab exam and used any of iPexpert’s self-study products, or attended a CCIE Bootcamp? If so, we’d like to add you to our CCIE Wall of Fame!
Show 252 – Design & Build 5 – BGP In The Data Center
BGP is typically found in the data center at the edge, but it keeps popping up in SDN conversations. For data centers of a certain size, maybe BGP makes sense. To find out, we gathered four engineers to discuss data center BGP.
The post Show 252 – Design & Build 5 – BGP In The Data Center appeared first on Packet Pushers.
PlexxiPulse—What are your VMworld Predictions?
If you caught our webinar on Thursday, you know that we believe the success of future networks will be a combination of hardware and software to form a dynamic, application aware, converged network fabric. We covered the evolution of the network as well as a few of our predictions for the future. If you missed it, don’t worry—there will be more to come. In the meantime, I will be at VMworld in San Francisco next week from August 30—September 3. I’m always open to chat about networking at large and how we’re disrupting the networking norm here at Plexxi. Let me know if you’ll be there! Do you have any predictions for VMworld this year?
Below please find a few of our top picks for our favorite news articles of the week. Enjoy!
No Jitter: Network Change: Evolutions and Revolutions
By Tom Noelle
Networking, and its transformation, is more than just technology. Broadband Internet came along during an unfortunate shift in the politics of networking. In the ’80s and ’90s we were moving from a global vision of communications as a regulated monopoly or even a government agency to one of a free market. The Internet exploded on the scene Continue reading
SDN Solutions Provide the Tools to Revolutionize the Enterprise
 Business and the infrastructure can finaly evolve in parallel.
Business and the infrastructure can finaly evolve in parallel.