Managed Services Can Offset IT Burdens From An Explosion of Mobile Devices
The vast number of connected devices enterprises must support today creates a problem that’s been brewing for a while but has now hit a tipping point.Twenty-five open-source network emulators and simulators you can use in 2023
I surveyed the current state of the art in open-source network emulation and simulation. I also reviewed the development and support status of all the network emulators and network simulators previously featured in my blog.
Of all the network emulators and network simulators I mentioned in my blog over the years, I found that eighteen of them are still active projects. I also found seven new projects that you can try. See below for a brief update about each tool.
Active projects
Below is a list of the tools previously featured in my blog that are, in my opinion, still actively supported.
Cloonix
Cloonix version 28 was released in January 2023. Cloonix stitches together Linux networking tools to make it easy to emulate complex networks by linking virtual machines and containers. Cloonix has both a command-line-interface and a graphical user interface.
The Cloonix web site now has a new address at: clownix.net and theCloonix project now hosts code on Github. Cloonix adopted a new release numbering scheme since I reviewed it in 2017. So it is now at “v28”.
Cloudsim
CloudSim is still maintained. Cloudsim is a network simulator that enables modeling, simulation, and experimentation of emerging Cloud computing Continue reading
MUST READ: Machine Learning for Network and Cloud Engineers
Javier Antich, the author of the fantastic AI/ML in Networking webinar, spent years writing the Machine Learning for Network and Cloud Engineers book that is now available in paperback and Kindle format.
I’ve seen a final draft of the book and it’s definitely worth reading. You should also invest some time into testing the scenarios Javier created. Here’s what I wrote in the foreword:
Artificial Intelligence (AI) has been around for decades. It was one of the exciting emerging (and overhyped) topics when I attended university in the late 1980s. Like today, the hype failed to deliver, resulting in long, long AI winter.
MUST READ: Machine Learning for Network and Cloud Engineers
Javier Antich, the author of the fantastic AI/ML in Networking webinar, spent years writing the Machine Learning for Network and Cloud Engineers book that is now available in paperback and Kindle format.
I’ve seen a final draft of the book and it’s definitely worth reading. You should also invest some time into testing the scenarios Javier created. Here’s what I wrote in the foreword:
Artificial Intelligence (AI) has been around for decades. It was one of the exciting emerging (and overhyped) topics when I attended university in the late 1980s. Like today, the hype failed to deliver, resulting in long, long AI winter.
A look at Internet traffic trends during Super Bowl LVII


The Super Bowl has been happening since the end of the 1966 season, the same year that the ARPANET project, which gave birth to the Internet, was initiated. Around 20 years ago, 50% of the US population were Internet users, and that number is now around 92%. So, it's no surprise that interest in an event like Super Bowl LVII resulted in a noticeable dip in Internet traffic in the United States at the time of the game's kickoff, dropping to around 5% lower than the previous Sunday. During the game, Rihanna's halftime show also caused a significant drop in Internet traffic across most states, with Pennsylvania and New York feeling the biggest impact, but messaging and video platforms saw a surge of traffic right after her show ended.
In this blog post, we will dive into who the biggest winners were among Super Bowl advertisers, as well as examine how traffic to food delivery services, social media and sports and betting websites changed during the game. In addition, we look at traffic trends seen at city and state levels during the game, as well as email threat volume across related categories in the weeks ahead of the game.
Wireless Worth Watching in 2023
Wireless power transfer, Wi-Fi 6 versions, life after 3G network shutdowns, and home networking challenges top the list.Cloudflare mitigates record-breaking 71 million request-per-second DDoS attack


This was a weekend of record-breaking DDoS attacks. Over the weekend, Cloudflare detected and mitigated dozens of hyper-volumetric DDoS attacks. The majority of attacks peaked in the ballpark of 50-70 million requests per second (rps) with the largest exceeding 71 million rps. This is the largest reported HTTP DDoS attack on record, more than 35% higher than the previous reported record of 46M rps in June 2022.
The attacks were HTTP/2-based and targeted websites protected by Cloudflare. They originated from over 30,000 IP addresses. Some of the attacked websites included a popular gaming provider, cryptocurrency companies, hosting providers, and cloud computing platforms. The attacks originated from numerous cloud providers, and we have been working with them to crack down on the botnet.
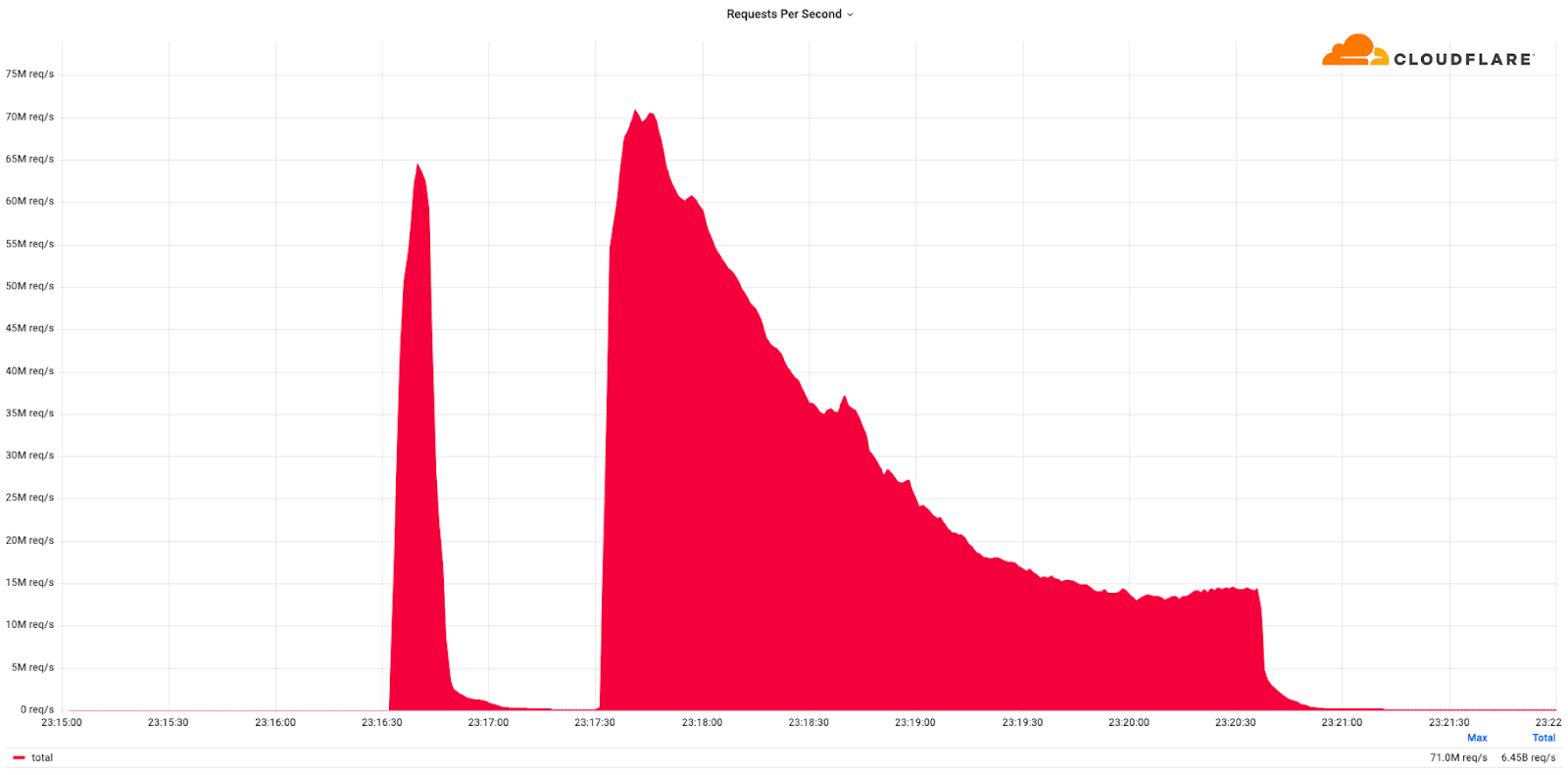
Over the past year, we’ve seen more attacks originate from cloud computing providers. For this reason, we will be providing service providers that own their own autonomous system a free Botnet threat feed. The feed will provide service providers threat intelligence about their own IP space; attacks originating from within their autonomous system. Service providers that operate their own IP space can now sign up to the Continue reading
Tech Bytes: Event-Driven Automation With Nokia’s SR Linux Event Handler Framework (Sponsored)
Today on the Tech Bytes podcast we talk about Event Handler, a new automation feature in Nokia’s SR Linux network OS that lets you automatically run scripts to fix problems when an event occurs. Nokia is our sponsor, and our guest is Roman Dodin, Product Line Manager at Nokia.
The post Tech Bytes: Event-Driven Automation With Nokia’s SR Linux Event Handler Framework (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Event-Driven Automation With Nokia’s SR Linux Event Handler Framework (Sponsored)
Today on the Tech Bytes podcast we talk about Event Handler, a new automation feature in Nokia’s SR Linux network OS that lets you automatically run scripts to fix problems when an event occurs. Nokia is our sponsor, and our guest is Roman Dodin, Product Line Manager at Nokia.Network Break 417: Zoom Chief Raises Bar For CEO Pay Cuts; Fortinet Rolls Out New Firewall Chips
Take a Network Break! On this week's episode we discuss new chip hardware from Fortinet, Extreme integrating its SD-WAN into its network fabric, the US and UK governments sanctioning members of the Trickbot malware gang, more tech layoffs, why tech CEOs should feel more financial pain, and more.
The post Network Break 417: Zoom Chief Raises Bar For CEO Pay Cuts; Fortinet Rolls Out New Firewall Chips appeared first on Packet Pushers.