Traceroute and Not-so-Equal ECMP
I came across an odd little issue recently involving equal-cost multipath (ECMP) routing and traceroute. Traceroutes from within our network to destinations out on the Internet were following two different paths, with one path being one hop longer than the other. This resulted in mangled traceroute output, impeding our ability to troubleshoot.
The relevant network topology comprises a mesh of two edge routers and two core switches. Each edge router has a number of transit circuits to different providers, and advertises a default route via OSPF to the two core switches below. The core switches each load-balance traffic across both default routes to either edge routers.
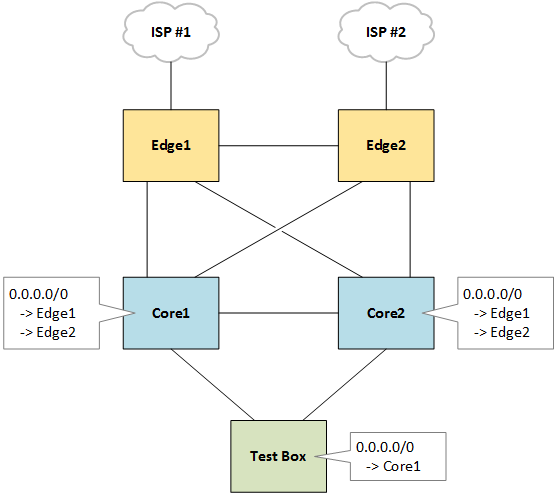
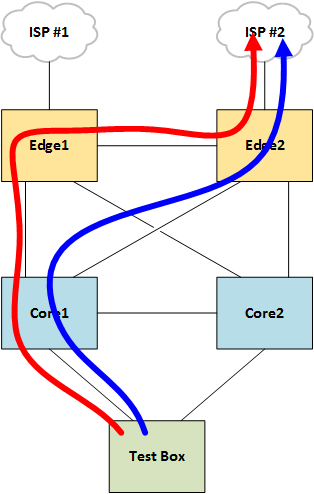
Because each edge router has different providers, some destinations are routed out via edge1 and others via edge2, which means sometimes a packet will be routed to edge2 via edge1, or vice versa.
Routers typically employ a hash function using layer three and four information from each packet to pseudo-randomly distribute traffic across equal links. Typically, all packets belonging to a flow (e.g. all packets with the same source and destination IP and port numbers) follow the same path.
However, in this case traceroute packets were being split across two path of unequal Continue reading
In theory…
I don’t normally peruse the reviews of my books — while I appreciate well thought out criticism, I normally find personal notes from folks who’ve read my books more profitable for mining out where I’m falling down on the job as a writer than reviews posted on book seller or book review sites. But one specific book review caught my eye the other day that I think points to a larger issue in the world of engineering, especially network engineering. The reviewer stated, in essence, that there was not enough practical application in my more recent tomes, and that I’m covering the same information over and over again.
Let me begin here — I’m not writing this as a defense of my own writing so much as to think through a habit of mind I think doesn’t really help us as an engineering community.
As far as the facts on the ground go, the reviewer is right on both counts, and wrong on both counts. Let’s imagine, for a moment, that you want to understand how a car works. You approach three different people — one a race car driver, another a top flight mechanic, and another an engineer who Continue reading
Wireshark Certified Network Analyst !!
Well, I finally took the time to buckle down and take the WCNA – Wireshark Certified Network Analyst. Once I finished up with the exam I can happily say I successfully past the exam which I have to admit is pretty cool. Protocol Analysis is definitely an interesting set of technologies to learn & know, it is also […]Three Areas of Impact on the Networking Industry
The state of the networking industry is undergoing a transformation. Both hardware and software have given way to the realization that applications and infrastructure are less about the individual functions of the sub-components of the overall system and more about the workflows that are being expressed against the technology as a whole.
Workflows, however, are also sub-components of the overall business logic that is being described, and ultimately expressed against the infrastructure. Micro-services and/or services oriented architectures are fundamentally changing many facets of technology, both in business practice and in features and functionality of the technology. They’re enabling a more agile and flexible technological landscape, and are helping to define administrative boundaries with respect to overall operations of the infrastructure.
Impact on Infrastructure
When looking at technology overall there is an obvious pattern emerging in all realms of the hardware that is enabling the industry. Programmability: the desire to express logic against infrastructure much in the same way that we’re able to express logic in the context of an application. “Infrastructure as code” is a phrase I’m sure we’ve all heard over the last couple of years, and this is something that is definitely being attained with the ecosystem of Continue reading
First steps with Python and Junos
I’m just spending the day trying to get my head around some very basic automation, so I thought I would install Python 2.7 and work through some of the tutorials on the Techwiki to see how I get on.
The tutorial I’m following is called Python for Non-Programmers and offers an easy way in for people like me. Of course as with a lot of open-source stuff, you don’t just download Python and get started – there are various dependencies, and dependencies with dependencies that you need to install first. If at the end of all that you’ve not forgotten what your name is or why you were doing all this shenanigans in the first place you can count yourself as winning.
Installation on a Windows machine is documented nicely here, but there are a few things which are out of date.
One part where it tells you run an executable to install ‘lxml’ but there isn’t one when you click the link provided. So instead you need to install it with a program called pip, which can be found in C:Python27scripts by default. pip is not in the PATH envirronment variable by default Continue reading
On SDN Controllers, Interconnectedness and Failure Domains
A long long time ago Colin Dixon wrote the following tweet in response to my Controller Cluster Is a Single Failure Domain blog post:
He’s obviously right, but I wasn’t talking about interconnected domains, but failure domains (yeah, I know, you could argue they are the same, but do read on).
Read more ...HP Gets Mobile with New Campus Networking Products
 HP is taking mobility to the campus with new products it announced today at Interop.
HP is taking mobility to the campus with new products it announced today at Interop.
