Upcoming webinar with Daniel Dib
Just wanted to let you know that Daniel from lostintransit.se is doing a webinar on network design. I will be attending and helping out any way i can.
Go here to learn more: https://learningnetwork.cisco.com/blogs/community_cafe/2015/01/21/network-design-fundamentals-webinar-with-ciscovip-daniel-dib
Quick ACL Entry Comparison Script
The ACL_compare function takes two lists of strings and compares the first to the second and returns a list comprising strings that are present in the first that are not in the second.
The listconvert function converts a file read into memory into a list of strings. Handy for when you use filenames as arguments when you run the script.
Essentially it’s all just string comparison really.
def ACL_compare(fwsm_ACL,asa_ACL):
comparison=[]
for line in fwsm_ACL:
if line in asa_ACL:
pass
else:
comparison.append(line)
return comparison
def listconvert(file):
newlist=file.readlines()
return newlist
Network Design Webinar With Yours Truly at CLN
I’m hosting a network design webinar at the Cisco Learning Network on Feb 19th, 20.00 UTC+1.
As you may know, I am studying for the CCDE so I’m focusing on design right now but my other reason for hosting this is to remind people that with all the buzzwords around SDN and NfV going around, the networking fundamentals still hold true. TCP/IP is as important as ever, building a properly designed network is a must if you want to have overlays running on it. If you build a house and do a sloppy job with the foundation, what will happen? The same holds true in networking.
I will introduce the concepts of network design. What does a network designer do? What tools are used? What is CAPEX? What is OPEX? What certifications are available? What is important in network design? We will also look at a couple of design scenarios and reason about the impact of our choices. There is always a tradeoff!
If you are interested in network design or just want to tune in to yours truly, follow this link to CLN.
I hope to see you there!
Kubernetes 101 – Networking
 One of the reasons that I’m so interested in docker and it’s associated technologies is because of the new networking paradigm it brings along with it. Kubernetes has a unique (and pretty awesome) way of dealing with these networking challenges but it can be hard to understand at first glance. My goal in this post is to walk you through deploying a couple of Kubernetes constructs and analyze what Kubernetes is doing at the network layer to make it happen. That being said, let’s start with the basics of deploying a pod. We’ll be using the lab we created in the first post and some of the config file examples we created in the second post.
One of the reasons that I’m so interested in docker and it’s associated technologies is because of the new networking paradigm it brings along with it. Kubernetes has a unique (and pretty awesome) way of dealing with these networking challenges but it can be hard to understand at first glance. My goal in this post is to walk you through deploying a couple of Kubernetes constructs and analyze what Kubernetes is doing at the network layer to make it happen. That being said, let’s start with the basics of deploying a pod. We’ll be using the lab we created in the first post and some of the config file examples we created in the second post.
Note: I should point out here again that this lab is built with bare metal hardware. The network model in this type of lab is likely slightly different that what you’d see with a cloud provider. However, the mechanics behind what Kubernetes is doing from a network perspective should be identical.
So just to level set, here is what our lab looks like…
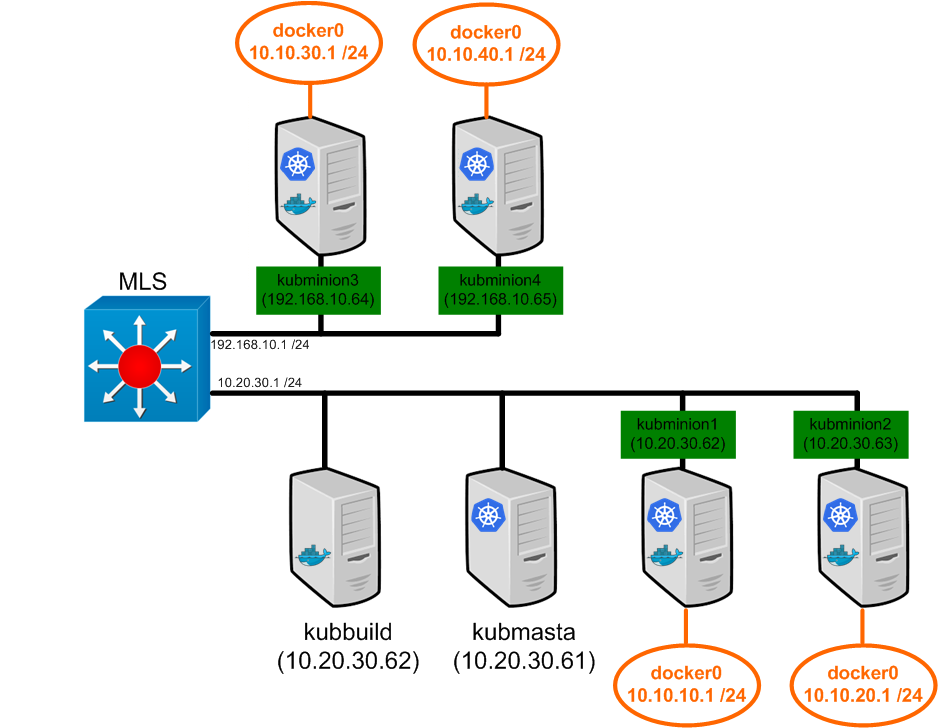
We touched on the topic of pod IP addressing before, but let’s provide Continue reading
Five Next-Gen Networker Skills
With all the flux that is going on in the networking space, it’s hard to figure out what to do next. You may want to add to your skillset, but you’re not sure where to throw your effort. I’d like to focus on five different areas you can focus on, without talking about a specific product - at the end of the day, that’s just implementation details. These areas are going to be increasingly more valuable and will help you be more marketable when added to your existing network knowledge and experience.Five Next-Gen Networker Skills
With all the flux that is going on in the networking space, it’s hard to figure out what to do next. You may want to add to your skillset, but you’re not sure where to throw your effort. I’d like to focus on five different areas you can focus on, without talking about a specific product - at the end of the day, that’s just implementation details. These areas are going to be increasingly more valuable and will help you be more marketable when added to your existing network knowledge and experience.How to run GUI applications on an Amazon AWS cloud server
In a previous post, I showed how easy it is to set up a remote server on Amazon’s AWS service. Now I would like see if I can run one or more of the open-source network simulators I’ve been using on this remote server. I want be able to access a network simulator from any device such as a personal computer, a tablet, or even a smart phone.
To accomplish this, I first need to install a Linux desktop environment on the remote Ubuntu server. Then, I need to set up the server and my client devices to allow the graphical user interface displayed on a remote server to be viewed on a local client.
In this post I will show how to install a Linux desktop (in this case, XFCE) and how to set up either VNC or X11 on a server and client.
Required software
Linux desktop
In this example, I chose to run the XFCE desktop environment on the Amzaon AWS remote server because XFCE uses less resources than other desktop environments such as Gnome or KDE.
Remote-access methods
There are two common methods for accessing a remote server’s graphical user interface:
- VNC, Virtual Network Computing, Continue reading
ONS Accelerate Workshop: Amazingly Refreshing
Sometimes the stars do align: Open Networking Summit organized their Service Provider Accelerate Workshop just a day prior to Network Field Day, so I had the fantastic opportunity to attend both.
I didn’t know what to expect from an event full of SDN/NFV thought leaders, and was extremely pleasantly surprised by the amount of realistic down-to-earth information I got.
Read more ...Community Show – Greg’s & Ethan’s Briefing Review for February 2015
In this show, we discuss recent briefings we received from CloudGenix, Light Cyber, VMware, and Meru. We also go on a little rabbit trail about Brocade, because they came to mind. You know how we are.
Author information
The post Community Show – Greg’s & Ethan’s Briefing Review for February 2015 appeared first on Packet Pushers Podcast and was written by Ethan Banks.
Community Show – Our Briefing Review for February 2015
In this show, we discuss recent briefings we received from CloudGenix, Light Cyber, VMware, and Meru. We also go on a little rabbit trail about Brocade, because they came to mind. You know how we are.
The post Community Show – Our Briefing Review for February 2015 appeared first on Packet Pushers.