Isolate browser-borne threats on any network with WAN-as-a-Service


Defending corporate networks from emerging threats is no easy task for security teams who manage complex stacks of firewalls, DNS and HTTP filters, and DLP and sandboxing appliances. Layering new defenses, such as Remote Browser Isolation to mitigate browser-borne threats that target vulnerabilities in unpatched browsers, can be complex for administrators who first have to plan how to integrate a new solution within their existing networks.
Today, we’re making it easier for administrators to integrate Cloudflare Browser Isolation into their existing network from any traffic source such as IPsec and GRE via our WAN-as-a-service, Magic WAN. This new capability enables administrators to connect on-premise networks to Cloudflare and protect Internet activity from browser-borne malware and zero day threats, without installing any endpoint software or nagging users to update their browsers.
Before diving into the technical details, let’s recap how Magic WAN and Browser Isolation fit into network perimeter architecture and a defense-in-depth security strategy.

Securing networks at scale with Magic WAN
Companies have historically secured their networks by building a perimeter out of on-premise routers, firewalls, dedicated connectivity and additional appliances for each layer of the security stack. Expanding the security perimeter pushes networks to their limits as centralized Continue reading
Cloudflare One Partner Program acceleration


Just a few short months ago, Cloudflare announced the launch of the Cloudflare One Partner Program. Many customers want to start their journeys to Zero Trust but are not sure where or how to start. It became clear there was a significant opportunity to partner with the channel – to combine Cloudflare’s complete Zero Trust portfolio with a broad set of Cloudflare-enabled, channel-delivered professional services to help customers navigate meaningful ways to adopt a Zero Trust architecture. Underscoring this need to partner was the fact that over the last six months we saw a 50% increase in new Cloudflare Zero Trust customers being won with the channel.
Clearly customers are ready to cut through the market hype of Zero Trust and start implementing - with the right platform of products and services - and the right value contribution of their channel partners.
Since the launch of the Cloudflare One Partner Program, we’ve engaged with hundreds of partners through our recruiting campaigns and in our Zero Trust Roadshow. This has provided a tremendous amount of feedback on what is working and why we believe we have the right program at the right time. This feedback has consistently centered around a few Continue reading
Cloudflare Data Loss Prevention now Generally Available

This post is also available in 简体中文, 日本語, Deutsch, Français and Español.

In July 2022, we announced beta access to our newest Zero Trust product, Data Loss Prevention (DLP). Today, we are even more excited to announce that DLP is Generally Available to customers! Any customer can now get visibility and control of sensitive data moving into, out of, and around their corporate network. If you are interested, check out the bottom of this post.
What is DLP?
Data Loss Prevention helps you overcome one of their biggest challenges: identifying and protecting sensitive data. The migration to the cloud has made tracking and controlling sensitive information more difficult than ever. Employees are using an ever-growing list of tools to manipulate a vast amount of data. Meanwhile, IT and security managers struggle to identify who should have access to sensitive data, how that data is stored, and where that data is allowed to go.
Data Loss Prevention enables you to protect your data based on its characteristics, such as keywords or patterns. As traffic moves into and out of corporate infrastructure, the traffic is inspected for indicators of sensitive data. If the indicators are found, the traffic is Continue reading
Detect security issues in your SaaS apps with Cloudflare CASB

This post is also available in 简体中文, 日本語, Deutsch, Français and Español.

It’s GA Week here at Cloudflare, meaning some of our latest and greatest endeavors are here and ready to be put in the hands of Cloudflare customers around the world. One of those releases is Cloudflare’s API-driven Cloud Access Security Broker, or CASB, one of the newest additions to our Zero Trust platform.
Starting today, IT and security administrators can begin using Cloudflare CASB to connect, scan, and monitor their third-party SaaS applications for a wide variety of security issues - all in just a few clicks.
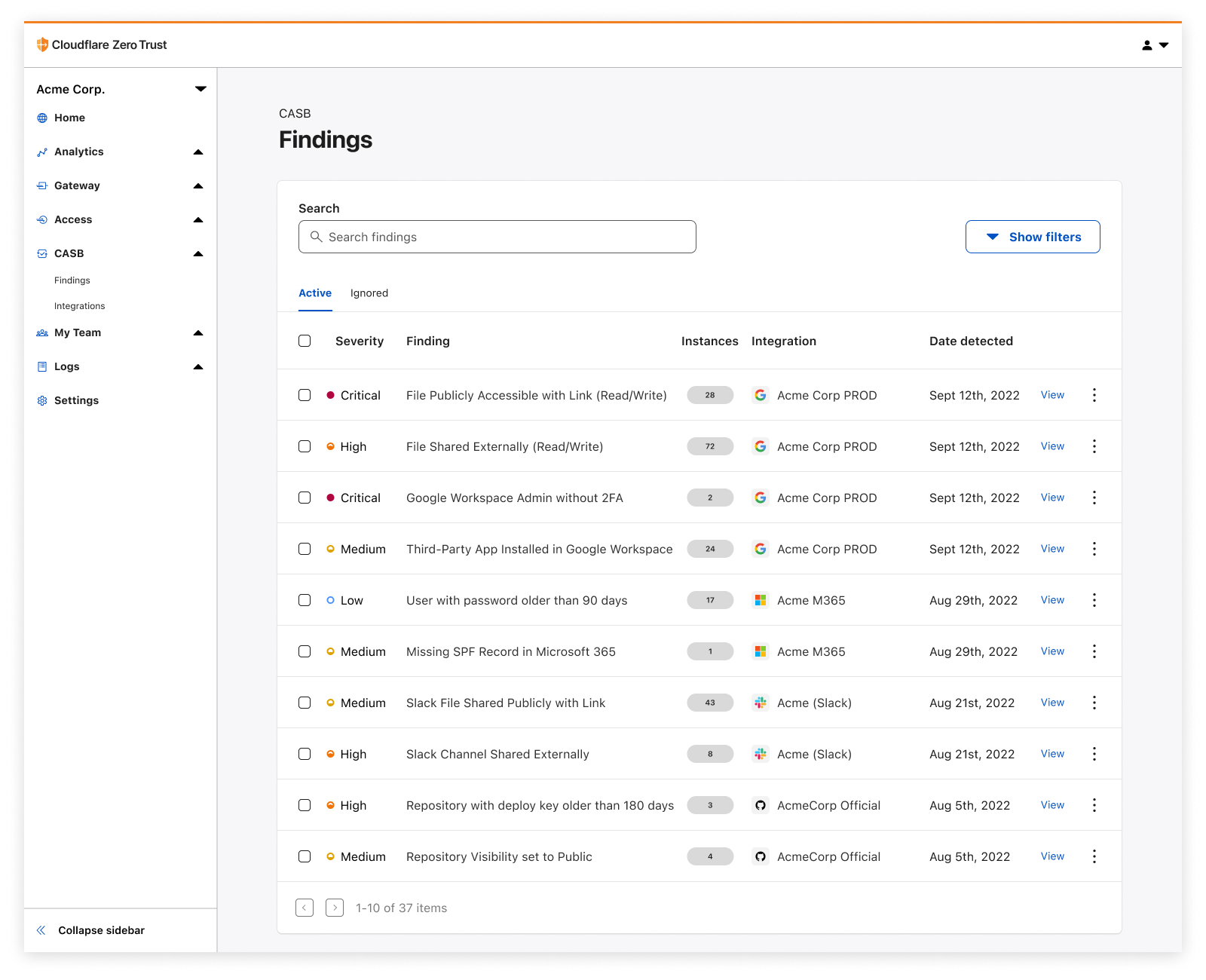
Whether it’s auditing Google Drive for data exposure and file oversharing, checking Microsoft 365 for misconfigurations and insecure settings, or reviewing third-party access for Shadow IT, CASB is now here to help organizations establish a direct line of sight into their SaaS app security and DLP posture.
The problem
Try to think of a business or organization that uses fewer than 10 SaaS applications. Hard, isn’t it?
It’s 2022, and by now, most of us have noticed the trend of mass SaaS adoption balloon over recent years, with some organizations utilizing hundreds of third-party services across a slew Continue reading
EVPN/VXLAN or Bridged Data Center Fabric?
An attendee in the Building Next-Generation Data Center online course sent me an interesting dilemma:
Some customers don’t like EVPN because of complexity (it is required knowledge BGP, symmetric/asymmetric IRB, ARP suppression, VRF, RT/RD, etc). They agree, that EVPN gives more stability and broadcast traffic optimization, but still, it will not save DC from broadcast storms, because protections methods are the same for both solutions (minimize L2 segments, storm-control).
We’ll deal with the unnecessary EVPN-induced complexity some other time, today let’s start with a few intro-level details.
EVPN/VXLAN or Bridged Data Center Fabric?
An attendee in the Building Next-Generation Data Center online course sent me an interesting dilemma:
Some customers don’t like EVPN because of complexity (it is required knowledge BGP, symmetric/asymmetric IRB, ARP suppression, VRF, RT/RD, etc). They agree, that EVPN gives more stability and broadcast traffic optimization, but still, it will not save DC from broadcast storms, because protections methods are the same for both solutions (minimize L2 segments, storm-control).
We’ll deal with the unnecessary EVPN-induced complexity some other time, today let’s start with a few intro-level details.
How to Logically Evaluate an IT Job Offer
You just got a job offer. Now what can you do to make sure it's an acceptable deal?Tech Bytes: Aruba Navigates 6Ghz Spectrum Challenges With AFC Demo (Sponsored)
Wi-Fi 6E gear can take advantage of the 6GHz band, but there are incumbent entities that also have a stake in the spectrum. To prevent interference, the Automated Frequency Coordination database coordinates among licensed and unlicensed users. On today’s Tech Bytes podcast, sponsored by Aruba, we’ll hear about Aruba’s participation in the first public demonstration of Wi-Fi 6E and the AFC database. My guest is Dave Wright, Head of Global Wireless Policy at Aruba.
The post Tech Bytes: Aruba Navigates 6Ghz Spectrum Challenges With AFC Demo (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Aruba Navigates 6Ghz Spectrum Challenges With AFC Demo (Sponsored)
Wi-Fi 6E gear can take advantage of the 6GHz band, but there are incumbent entities that also have a stake in the spectrum. To prevent interference, the Automated Frequency Coordination database coordinates among licensed and unlicensed users. On today’s Tech Bytes podcast, sponsored by Aruba, we’ll hear about Aruba’s participation in the first public demonstration of Wi-Fi 6E and the AFC database. My guest is Dave Wright, Head of Global Wireless Policy at Aruba.Network Break 399: Apstra Goes Freeform For DC Automation; Arista Launches Encryption-Friendly Routers
This week's Network Break podcast covers new capabilities for data center automation in Juniper Apstra, new encryption-friendly Arista routers, and why climate change risks should factor into your IT planning. The startup Veego is pitching an end user experience app to ISPs, the Google spin-out Aalyria looks to build networks using free-space optics, and Microsoft announces Azure Orbital Cloud Access that uses Starlink to connect remote sites to Azure.
The post Network Break 399: Apstra Goes Freeform For DC Automation; Arista Launches Encryption-Friendly Routers appeared first on Packet Pushers.
Network Break 399: Apstra Goes Freeform For DC Automation; Arista Launches Encryption-Friendly Routers
This week's Network Break podcast covers new capabilities for data center automation in Juniper Apstra, new encryption-friendly Arista routers, and why climate change risks should factor into your IT planning. The startup Veego is pitching an end user experience app to ISPs, the Google spin-out Aalyria looks to build networks using free-space optics, and Microsoft announces Azure Orbital Cloud Access that uses Starlink to connect remote sites to Azure.Service Mesh and Ingress In Kubernetes: Lesson 5 – Service Mesh Install And App Deployment With Istio – Video
In this video, host Michael Levan walks through the basics of installing the Istio service mesh and deploying a simple application. Host Michael Levan brings his background in system administration, software development, and DevOps to this video series. He has Kubernetes experience as both a developer and infrastructure engineer. He’s also a consultant and Pluralsight […]
The post Service Mesh and Ingress In Kubernetes: Lesson 5 – Service Mesh Install And App Deployment With Istio – Video appeared first on Packet Pushers.
Introducing Advanced DDoS Alerts


We’re pleased to introduce Advanced DDoS Alerts. Advanced DDoS Alerts are customizable and provide users the flexibility they need when managing many Internet properties. Users can easily define which alerts they want to receive — for which DDoS attack sizes, protocols and for which Internet properties.
This release includes two types of Advanced DDoS Alerts:
- Advanced HTTP DDoS Attack Alerts - Available to WAF/CDN customers on the Enterprise plan, who have also subscribed to the Advanced DDoS Protection service.
- Advanced L3/4 DDoS Attack Alerts - Available to Magic Transit and Spectrum BYOIP customers on the Enterprise plan.
Standard DDoS Alerts are available to customers on all plans, including the Free plan. Advanced DDoS Alerts are part of Cloudflare’s Advanced DDoS service.
Why alerts?
Distributed Denial of Service attacks are cyber attacks that aim to take down your Internet properties and make them unavailable for your users. As early as 2017, Cloudflare pioneered the Unmetered DDoS Protection to provide all customers with DDoS protection, without limits, to ensure that their Internet properties remain available. We’re able to provide this level of commitment to our customers thanks to our automated DDoS protection systems. But if the systems operate automatically, why even be Continue reading
Introducing Cloudflare Adaptive DDoS Protection – our new traffic profiling system for mitigating DDoS attacks


Every Internet property is unique, with its own traffic behaviors and patterns. For example, a website may only expect user traffic from certain geographies, and a network might only expect to see a limited set of protocols.
Understanding that the traffic patterns of each Internet property are unique is what led us to develop the Adaptive DDoS Protection system. Adaptive DDoS Protection joins our existing suite of automated DDoS defenses and takes it to the next level. The new system learns your unique traffic patterns and adapts to protect against sophisticated DDoS attacks.
Adaptive DDoS Protection is now generally available to Enterprise customers:
- HTTP Adaptive DDoS Protection - available to WAF/CDN customers on the Enterprise plan, who have also subscribed to the Advanced DDoS Protection service.
- L3/4 Adaptive DDoS Protection - available to Magic Transit and Spectrum customers on an Enterprise plan.
Adaptive DDoS Protection learns your traffic patterns
The Adaptive DDoS Protection system creates a traffic profile by looking at a customer’s maximal rates of traffic every day, for the past seven days. The profiles are recalculated every day using the past seven-day history. We then store the maximal traffic rates seen for every predefined dimension value. Every profile Continue reading
Account WAF now available to Enterprise customers


Do you manage more than a single domain? If the answer is yes, now you can manage a single WAF configuration for all your enterprise domains.
Cloudflare has been built around the concept of zone, which is broadly equivalent to a domain. Customers can add multiple domains to a Cloudflare account, and every domain has its own independent security configuration. If you deploy a rule to block bots on example.com, you will need to rewrite the same rule on example.org. You’ll then need to visit the dashboard of every zone when you want to update it. This applies to all WAF products including Managed, Firewall and Rate Limiting rules.
If you have just two domains that’s not a big deal. But if you manage hundreds or thousands of domains like most large organizations do. Dealing with individual domains becomes time-consuming, expensive or outright impractical. Of course, you could build automation relying on our API or Terraform. This will work seamlessly but not all organizations have the capabilities to manage this level of complexity. Furthermore, having a Terraform integration doesn’t fully replicate the experience or give the confidence provided by interacting with a well-designed UI.
Following Cloudflare Continue reading