Building High-Available Web Services: Open Source Load Balancing Based on HAProxy + FRR and Origin Web Server Based on NGINX Connected to Arista EVPN/VXLAN. Part 2 – Configuration and Validation.
Hello my friend,
In the previous blogpost we have started discussion about the Open Source Load Balancing solution, which leverages HAProxy and FRR, which is connected to the data centre fabric running EVPN/VXLAN on Arista EOS switches and serving content from NGINX-based origin servers. In that blogpost we covered the architectural guidelines and design principles. Today we will cover the configuration and the validation of the solution.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
What Is More Important: Network Technologies or Network Automation?
The truth is that both disciplines are equally important. Knowledge and skills in network technologies will allow you to build great connectivity solutions to empower businesses across the globe and spread its capabilities as nowadays, perhaps, 99% of all business operations leverage IT and network technologies either entirely or at least partially. In its turn, network automation allows to make operational activities (e.g., configuration, troubleshooting, analysis, etc) much more precise and predictable, decreasing the probability of outages or Continue reading
Feedback Appreciated: Next-Generation Metro Area Networks
Etienne-Victor Depasquale, a researcher at University of Malta, is trying to figure out what technologies service providers use to build real-life metro-area networks, and what services they offer on top of that infrastructure.
If you happen to be involved with a metro area network, he’d love to hear from you – please fill in this survey – and he promised that he’ll share the results of the survey with the participants.
Feedback Appreciated: Next-Generation Metro Area Networks
Etienne-Victor Depasquale, a researcher at University of Malta, is trying to figure out what technologies service providers use to build real-life metro-area networks, and what services they offer on top of that infrastructure.
If you happen to be involved with a metro area network, he’d love to hear from you – please fill in this survey – and he promised that he’ll share the results of the survey with the participants.
Blocking Kiwifarms
We have blocked Kiwifarms. Visitors to any of the Kiwifarms sites that use any of Cloudflare's services will see a Cloudflare block page and a link to this post. Kiwifarms may move their sites to other providers and, in doing so, come back online, but we have taken steps to block their content from being accessed through our infrastructure.
This is an extraordinary decision for us to make and, given Cloudflare's role as an Internet infrastructure provider, a dangerous one that we are not comfortable with. However, the rhetoric on the Kiwifarms site and specific, targeted threats have escalated over the last 48 hours to the point that we believe there is an unprecedented emergency and immediate threat to human life unlike we have previously seen from Kiwifarms or any other customer before.
Escalating threats
Kiwifarms has frequently been host to revolting content. Revolting content alone does not create an emergency situation that necessitates the action we are taking today. Beginning approximately two weeks ago, a pressure campaign started with the goal to deplatform Kiwifarms. That pressure campaign targeted Cloudflare as well as other providers utilized by the site.
Cloudflare provides security services to Kiwifarms, protecting them from DDoS and Continue reading
Worth Reading: Latency Matters When Migrating Workloads
It’s so refreshing to find someone who understands the impact of latency on application performance, and develops a methodology that considers latency when migrating a workload into a public cloud: Adding latency: one step, two step, oops by Lawrence Jones.
Worth Reading: Latency Matters When Migrating Workloads
It’s so refreshing to find someone who understands the impact of latency on application performance, and develops a methodology that considers latency when migrating a workload into a public cloud: Adding latency: one step, two step, oops by Lawrence Jones.
AWS and Pulumi with Go Getting Started
Pulumi is an Infrastructure as Code (IaC) tool similar to Terraform, except that, rather than defining resources in a DSL, you defined them in a supported programming language. This means you have access to all of your chosen languages features as well as any supporting libraries...continue reading
Lessons Learned Working Abroad
This post was originally published in the Packet Pushers’ Human Infrastructure newsletter on September 1, 2022. You can subscribe to the newsletter for free here. Over a year ago, my wife and I moved from the eastern United States to Seoul, South Korea. A great opportunity presented itself for her career, and my US-based employer was […]
The post Lessons Learned Working Abroad appeared first on Packet Pushers.
When Were You Last a Beginner?

In a couple of weeks I’m taking the opportunity to broaden my leadership horizons by attending the BSA leadership course known as Philmont Leadership Challenge. It’s a course that builds on a lot of the things that I’ve been learning and teaching for the past five years. It’s designed to be a sort of capstone for servant leadership and learning how to inspire others. I’m excited to be a part of it in large part because I get to participate for a change.
Being a member of the staff for my local council Wood Badge courses has given me a great opportunity to learn the material inside and out. I love being able to teach and see others grow into leaders. It’s also inspired me to share some of those lessons here to help others in the IT community that might not have the chance to attend a course like that. However the past 3 years have also shown me the value of being a beginner at something from time to time.
Square One
Everyone is new at something. No one is born knowing every piece of information they’ll need to know for their entire lives. We learn language and Continue reading
Heavy Networking 645: Secure Wireless Planning And Design
On today’s episode of Heavy Networking, we discuss secure wireless planning and design with Jennifer "JJ Minella. JJ is the author of the book "Wireless Security Architecture." We talk about the goals for planning a wireless design, why it's worth the upfront investment, keeping operators in mind as you design your deployment, the importance of communication, design iteration, and more.
The post Heavy Networking 645: Secure Wireless Planning And Design appeared first on Packet Pushers.
Heavy Networking 645: Secure Wireless Planning And Design
On today’s episode of Heavy Networking, we discuss secure wireless planning and design with Jennifer "JJ Minella. JJ is the author of the book "Wireless Security Architecture." We talk about the goals for planning a wireless design, why it's worth the upfront investment, keeping operators in mind as you design your deployment, the importance of communication, design iteration, and more.Log analytics using ClickHouse
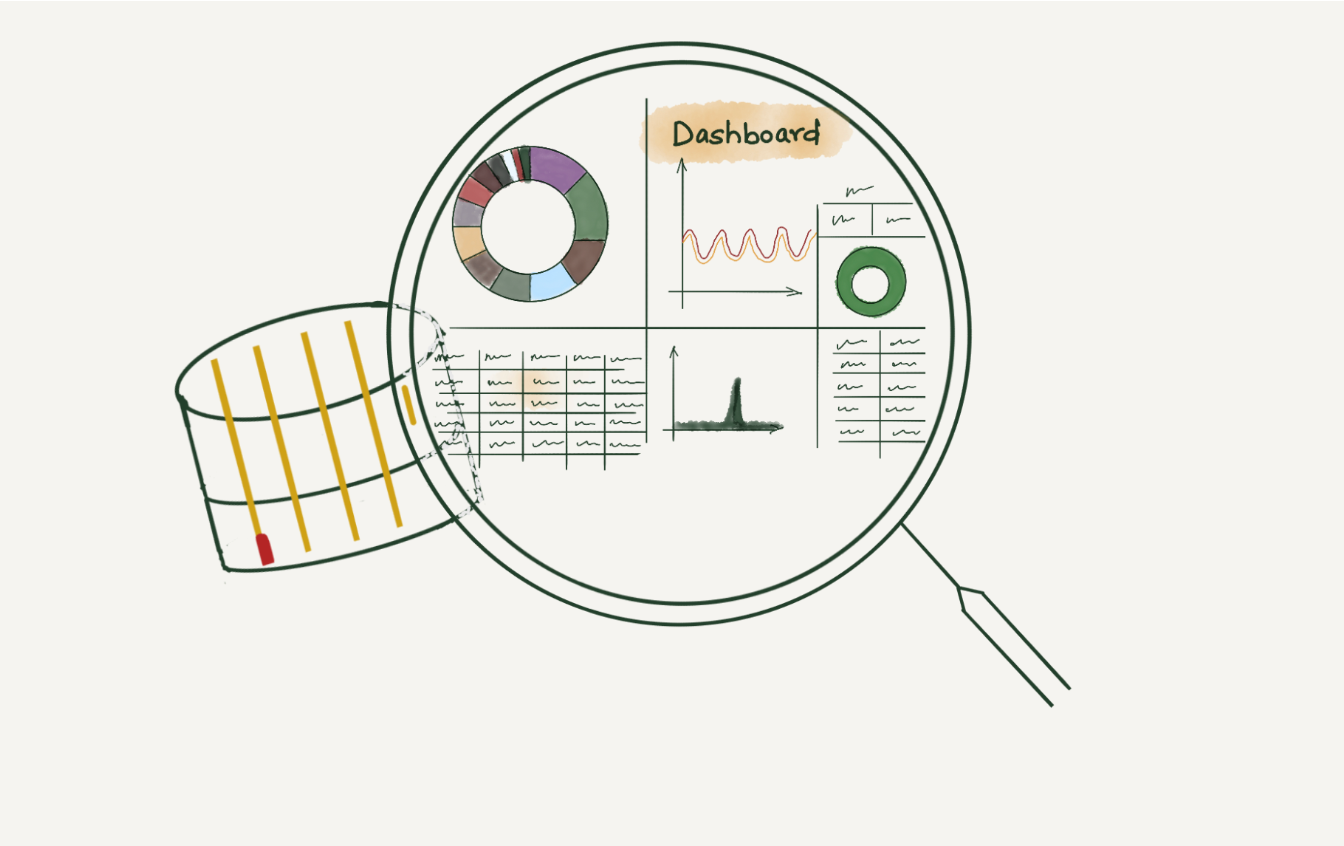
This is an adapted transcript of a talk we gave at Monitorama 2022. You can find the slides with presenter’s notes here and video here.
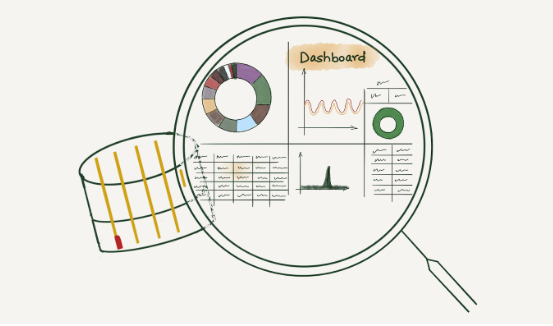
When a request at Cloudflare throws an error, information gets logged in our requests_error pipeline. The error logs are used to help troubleshoot customer-specific or network-wide issues.
We, Site Reliability Engineers (SREs), manage the logging platform. We have been running Elasticsearch clusters for many years and during these years, the log volume has increased drastically. With the log volume increase, we started facing a few issues. Slow query performance and high resource consumption to list a few. We aimed to improve the log consumer's experience by improving query performance and providing cost-effective solutions for storing logs. This blog post discusses challenges with logging pipelines and how we designed the new architecture to make it faster and cost-efficient.
Before we dive into challenges in maintaining the logging pipelines, let us look at the characteristics of logs.
Characteristics of logs
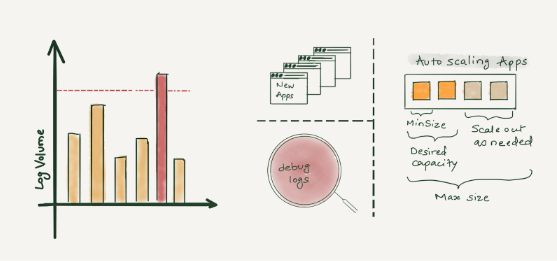
Unpredictable - In today's world, where there are tons of microservices, the amount of logs a centralized logging system will receive is very unpredictable. There are various reasons why capacity estimation of log volume is so difficult. Continue reading
Why Migrating a Database to the Cloud is Like a Heart Transplant
Migrating your organization's on-premises database to a native-cloud database is fraught with challenges and potential benefits. Here are recommendations to ensure this ‘heart transplant’ doesn't fail.A Second Look at QUIC Use
A couple of months ago, in July 2022, I wrote about our work in measuring the level of use of QUIC in the Internet. Getting this measurement “right” has been an interesting exercise, and it’s been a learning experience that I’d like to relate here. We’ll start from the end of the previous article and carry on from there.Video: Kubernetes Services Overview
After completing the discussion of basic Kubernetes networking with a typical inter-pod traffic scenario, Stuart Charlton tackled another confusing topic: an overview of what Kubernetes services are.
 interest in 5G private wireless,†said ABI Research. “In turn, the lack of enthusiasm has discouraged hardware suppliers from creating the necessary devices.â€
interest in 5G private wireless,†said ABI Research. “In turn, the lack of enthusiasm has discouraged hardware suppliers from creating the necessary devices.â€