IPv6 Buzz 107: IPv6 Unique Local Addresses (ULA) At IETF 114
In this episode, Ed and Tom talk with Nick Buraglio about ongoing efforts within the IETF to improve ULA. Nick is co-author of the IETF draft "Unintended Operational Issues With ULA" and recently presented at IETF 114 in Philadelphia.
The post IPv6 Buzz 107: IPv6 Unique Local Addresses (ULA) At IETF 114 appeared first on Packet Pushers.
IPv6 Buzz 107: IPv6 Unique Local Addresses (ULA) At IETF 114
In this episode, Ed and Tom talk with Nick Buraglio about ongoing efforts within the IETF to improve ULA. Nick is co-author of the IETF draft "Unintended Operational Issues With ULA" and recently presented at IETF 114 in Philadelphia.Day Two Cloud 158: On Leadership With Chris Wahl
According to Chris Wahl, everyone in an organization can lead--not just those with "chief" or "manager" in their job title. Leadership isn't about telling everyone else what to do. Not at all. Have a listen as Chris explains what it is to lead, and how you can do so yourself while enabling others around you to do the same.Can a Weighted Eye Mask Relieve Tired Eyes?
If you’re anything like most people, you probably spend a lot of time staring at screens. Whether you’re working on a computer, scrolling through your phone, or watching TV, all that screen time can take a toll on your eyes. If you’re looking for a way to relieve tired eyes, you may want to try a weighted eye mask.
Weighted eye masks are filled with a material, such as plastic beads, that add a gentle pressure to the eyes. This pressure can help to relax the muscles around the eyes and reduce tension headaches. Additionally, the weight of the mask can help to block out light, which can further improve relaxation.
Different Types of Weighted Eye Masks and Their Benefits
There are a few different types of weighted eye masks on the market, each with its own benefits.
Pure hydration eye masks
Pure hydrating eye masks are filled with gel or liquid, rather than beads. These masks are often used to help with dry eyes, as the gel can help to increase moisture around the eyes.
Warming eye masks
Warming eye masks are filled with a material that retains heat. These masks can help to soothe tired eyes and reduce Continue reading
Reality Check: Why Your Cloud Provider Won’t Be Providing Multi-Cloud Failover
Your IT organization may view failing over from one hyperscaler's cloud to another as the ultimate security when it comes to cloud resiliency. Here's why that's not going to happen, plus a look at alternatives.Hedge 142: George Michaelson and the Pace of IPv6 Deployment
IPv6 is still being deployed, years after the first world IPv6 day, even more years after its first acceptance as an Internet standard by the IETF. What is taking so long? George Michaelson (APNIC) joins Tom Ammon and Russ White on this episode of the Hedge to discuss the current pace of IPv6 deployment, where there are wins, and why things might be moving more slowly in other areas.
What You Need to Know About Predictive Network Technology
You may not be able to peek into the future, but predictive network technology can spot and troubleshoot potential problems before they occur.Tanzu Service Mesh Acceleration using eBPF
Performance and Security Optimizations on Intel Xeon Scalable Processors – Part 1
Contributors
Manish Chugtu — VMware
Ramesh Masavarapu, Saidulu Aldas, Sakari Poussa, Tarun Viswanathan — Intel
Introduction
VMware Tanzu Service Mesh built on open source Istio, provides advanced, end-to-end connectivity, security, and insights for modern applications—across application end-users, microservices, APIs, and data—enabling compliance with Service Level Objectives (SLOs) and data protection and privacy regulations.
Service Mesh architecture pattern solves many problems, which are well known and extensively documented – so we won’t be talking about those in this blog. But it also comes with its own challenges and some of the top focus areas that we will discuss in this series of blogs are around:
- Performance
- Security
Intel and VMware have been working together to optimize and accelerate the microservices middleware and infrastructure with software and hardware to ensure developers have the best-in-class performance and low latency experience when building distributed workloads with a focus on improving the performance, crypto accelerations, and making it more secure.
In Part 1 of this blog series, we will talk about one such performance challenge (with respect to service mesh data path performance) and discuss our solution around that.
The current implementation Continue reading
Quick and easy vulnerability management with Calico Cloud
As more enterprises adopt containers, microservices, and Kubernetes for their cloud-native applications, they need to be aware of the vulnerabilities in container images during build and runtime that can be exploited. In this blog, I will demonstrate how you can implement vulnerability management in CI/CD pipelines, perform image assurance during build time, and enforce runtime threat defense to protect your workloads from security threats.
Image scanning and automatic blocking of high-risk images
The majority of images in CI/CD pipelines have vulnerabilities, misconfigurations, or both. An active cloud-native application protection platform (CNAPP) should scan, identify, and list vulnerabilities in container images based on databases such as NIST and NVD. The active CNAPP should then help teams build security policies to determine which images should be deployed or blocked based on several factors such as severity, last scan timestamp, and organizational exceptions. Given the sheer amount of vulnerabilities that appear daily, users will be easily overwhelmed if they have to address all existing vulnerabilities. Security teams will have to build a deploy/block criteria to prioritize vulnerabilities that they will address first—a workflow that is easy to start but difficult to manage and operate long-term. Hence, security teams should look for a security Continue reading
The mechanics of a sophisticated phishing scam and how we stopped it


Yesterday, August 8, 2022, Twilio shared that they’d been compromised by a targeted phishing attack. Around the same time as Twilio was attacked, we saw an attack with very similar characteristics also targeting Cloudflare’s employees. While individual employees did fall for the phishing messages, we were able to thwart the attack through our own use of Cloudflare One products, and physical security keys issued to every employee that are required to access all our applications.
We have confirmed that no Cloudflare systems were compromised. Our Cloudforce One threat intelligence team was able to perform additional analysis to further dissect the mechanism of the attack and gather critical evidence to assist in tracking down the attacker.
This was a sophisticated attack targeting employees and systems in such a way that we believe most organizations would be likely to be breached. Given that the attacker is targeting multiple organizations, we wanted to share here a rundown of exactly what we saw in order to help other companies recognize and mitigate this attack.
Targeted Text Messages
On July 20, 2022, the Cloudflare Security team received reports of employees receiving legitimate-looking text messages pointing to what appeared to be a Cloudflare Okta login Continue reading
DDoS detection with advanced real-time flow analytics
The diagram shows two high bandwidth flows of traffic to the Customer Network, the first (shown in blue) is a bulk transfer of data to a big data application, and the second (shown in red) is a distributed denial of service (DDoS) attack in which large numbers of compromised hosts attempt to flood the link connecting the Customer Network to the upstream Transit Provider. Industry standard sFlow telemetry from the customer router streams to an instance of the sFlow-RT real-time analytics engine which is programmed to detect (and mitigate) the DDoS attack.This article builds on the Docker testbed to demonstrate how advanced flow analytics can be used to separate the two types of traffic and detect the DDoS attack.
docker run --rm -d -e "COLLECTOR=host.docker.internal" -e "SAMPLING=100" \First, start a Host sFlow agent using the pre-built sflow/host-sflow image to generate the sFlow telemetry that would stream from the switches and routers in a production deployment.
--net=host -v /var/run/docker.sock:/var/run/docker.sock:ro \
--name=host-sflow sflow/host-sflow
setFlow('ddos_amplification', {
keys:'ipdestination,udpsourceport',
value: 'frames',
values: ['count:ipsource']
});
setThreshold('ddos_amplification', {
metric:'ddos_amplification',
value: 10000,
byFlow:true,
timeout: 2
});
setEventHandler(function(event) {
var [ipdestination,udpsourceport] = event.flowKey.split(',');
var [sourcecount] = event.values;
Continue reading
Introducing new Cloudflare for SaaS documentation


As a SaaS provider, you’re juggling many challenges while building your application, whether it’s custom domain support, protection from attacks, or maintaining an origin server. In 2021, we were proud to announce Cloudflare for SaaS for Everyone, which allows anyone to use Cloudflare to cover those challenges, so they can focus on other aspects of their business. This product has a variety of potential implementations; now, we are excited to announce a new section in our Developer Docs specifically devoted to Cloudflare for SaaS documentation to allow you take full advantage of its product suite.
Cloudflare for SaaS solution
You may remember, from our October 2021 blog post, all the ways that Cloudflare provides solutions for SaaS providers:
- Set up an origin server
- Encrypt your customers’ traffic
- Keep your customers online
- Boost the performance of global customers
- Support custom domains
- Protect against attacks and bots
- Scale for growth
- Provide insights and analytics
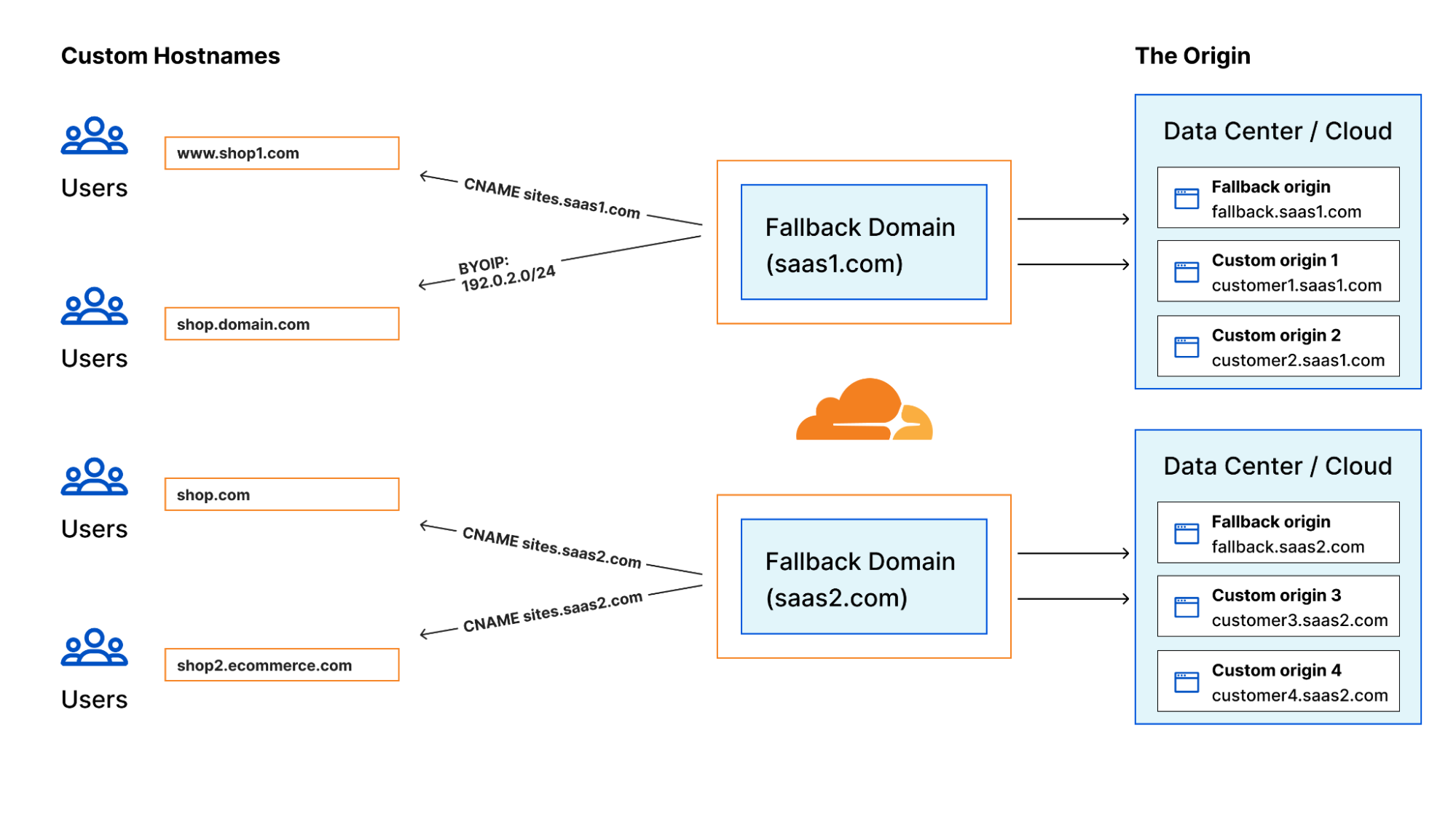
However, we received feedback from customers indicating confusion around actually using the capabilities of Cloudflare for SaaS because there are so many features! With the existing documentation, it wasn’t 100% clear how to enhance security and performance, or how to support custom domains. Now, we want Continue reading
