Analysis: Will Your Security Infrastructure Be Determined By Your Cyberinsurance?
This post originally appeared on the Packet Pushers’ now-defunct Ignition site on October 1, 2019. Insurance companies that offer cyberinsurance policies are looking at ways to reduce their risk (and improve profit margins) by discounting for companies that deploy reviewed and approved technologies. Company executives will make decisions about the cost and value of […]
The post Analysis: Will Your Security Infrastructure Be Determined By Your Cyberinsurance? appeared first on Packet Pushers.
BYOCNI: Introducing Calico CNI for Azure AKS
Cloud-native applications running on Kubernetes rely on container network plugins to establish workload communication. While Azure Kubernetes Service (AKS) provides several supported networking options (kubenet and Azure CNI) that address the needs of most deployments, Microsoft recently introduced the ability to bring your own networking solution, called BYOCNI, to help users address more advanced networking requirements. This new feature enables AKS customers to run Calico networking on AKS.
This blog will walk you through some exciting capabilities you can unlock with Calico running in your AKS deployments.
Why use Calico networking on AKS?
Calico is the most widely adopted container networking and security solution for Kubernetes. Powering more than 100M containers across 2M+ nodes in 166 countries, Calico is supported across all major cloud providers and Kubernetes distributions. Calico gives you a choice of data planes, including eBPF, standard Linux networking, and Windows HNS-based workloads running in public clouds and/or on-prem, on a single node, or across a multi-thousand-node cluster. Whether you need to scale to thousands of microservices with eBPF, or add Windows workloads to your Kubernetes deployments, Calico has you covered.
Calico’s core design principles leverage cloud-native design best practices, combined with proven, standards-based network protocols trusted by Continue reading
Reading: The Case for a Mostly Open Internet
This post originally appeared on the Packet Pushers’ Ignition site on January 14, 2020. There is a slow but steady trend for Governements’ to take back control of internet in their countries. For China the “great firewall” is now a rigid access control on content. Russia has been progressing changes to to be isolate itself […]
The post Reading: The Case for a Mostly Open Internet appeared first on Packet Pushers.
Kubernetes For Network Engineers: Lesson 2 – Services, Nodeports, And Load Balancers – Video
This lesson walks through the basics of reaching an application running in a Kubernetes pod. Instructor Michael Levan brings his background in system administration, software development, and DevOps to this series. He has Kubernetes experience as both a developer and infrastructure engineer. He’s also a consultant and Pluralsight author, and host of the “Kubernetes Unpacked” […]
The post Kubernetes For Network Engineers: Lesson 2 – Services, Nodeports, And Load Balancers – Video appeared first on Packet Pushers.
IPv6 Buzz 104: IPv6 For Redundancy When IPv4 Fails
In this IPv6 Buzz episode we talk about the benefit of IPv6 connectivity when IPv4 fails. We examine the types of IPv4 failures, how IPv6 behaves during IPv4 failure, application dependencies, and more.
The post IPv6 Buzz 104: IPv6 For Redundancy When IPv4 Fails appeared first on Packet Pushers.
IPv6 Buzz 104: IPv6 For Redundancy When IPv4 Fails
In this IPv6 Buzz episode we talk about the benefit of IPv6 connectivity when IPv4 fails. We examine the types of IPv4 failures, how IPv6 behaves during IPv4 failure, application dependencies, and more.Managed Transforms: templated HTTP header modifications
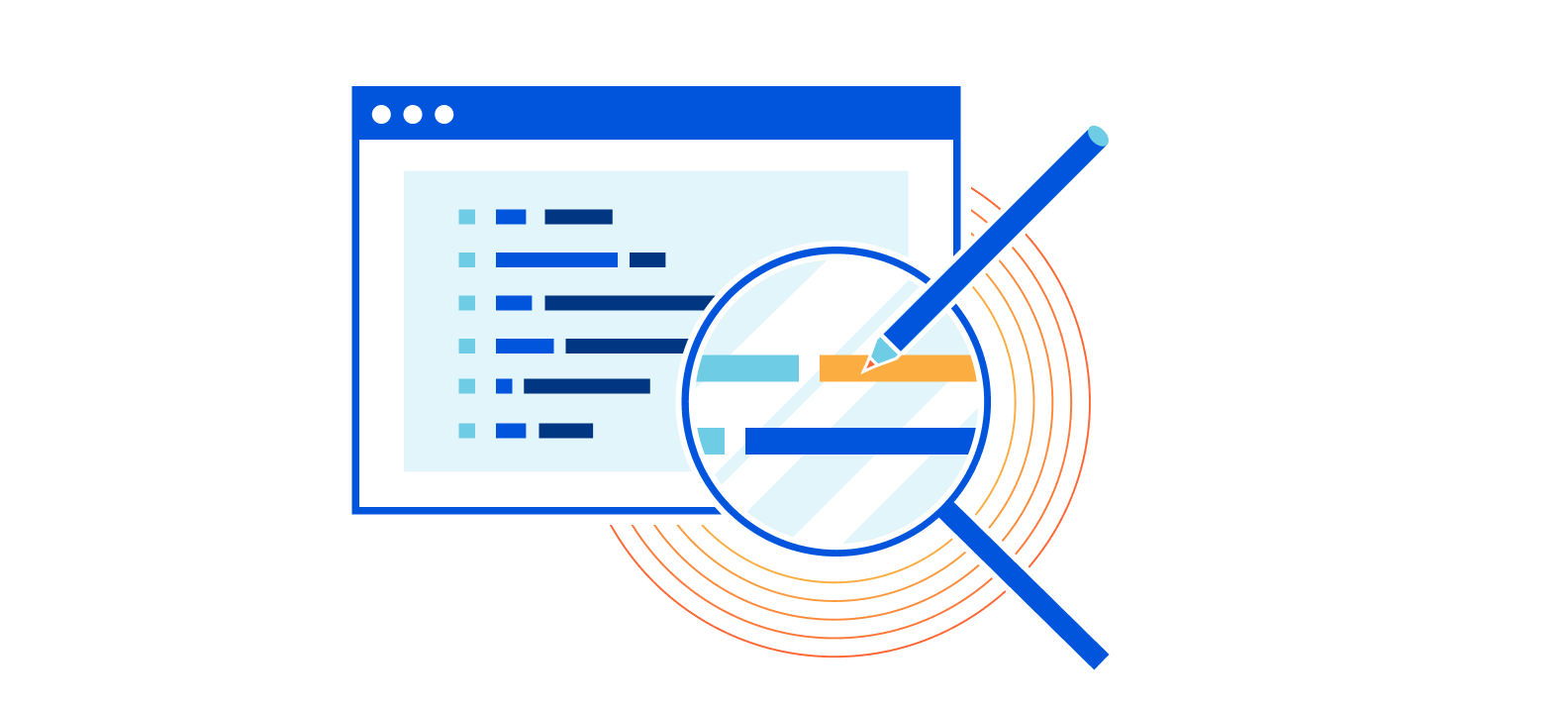
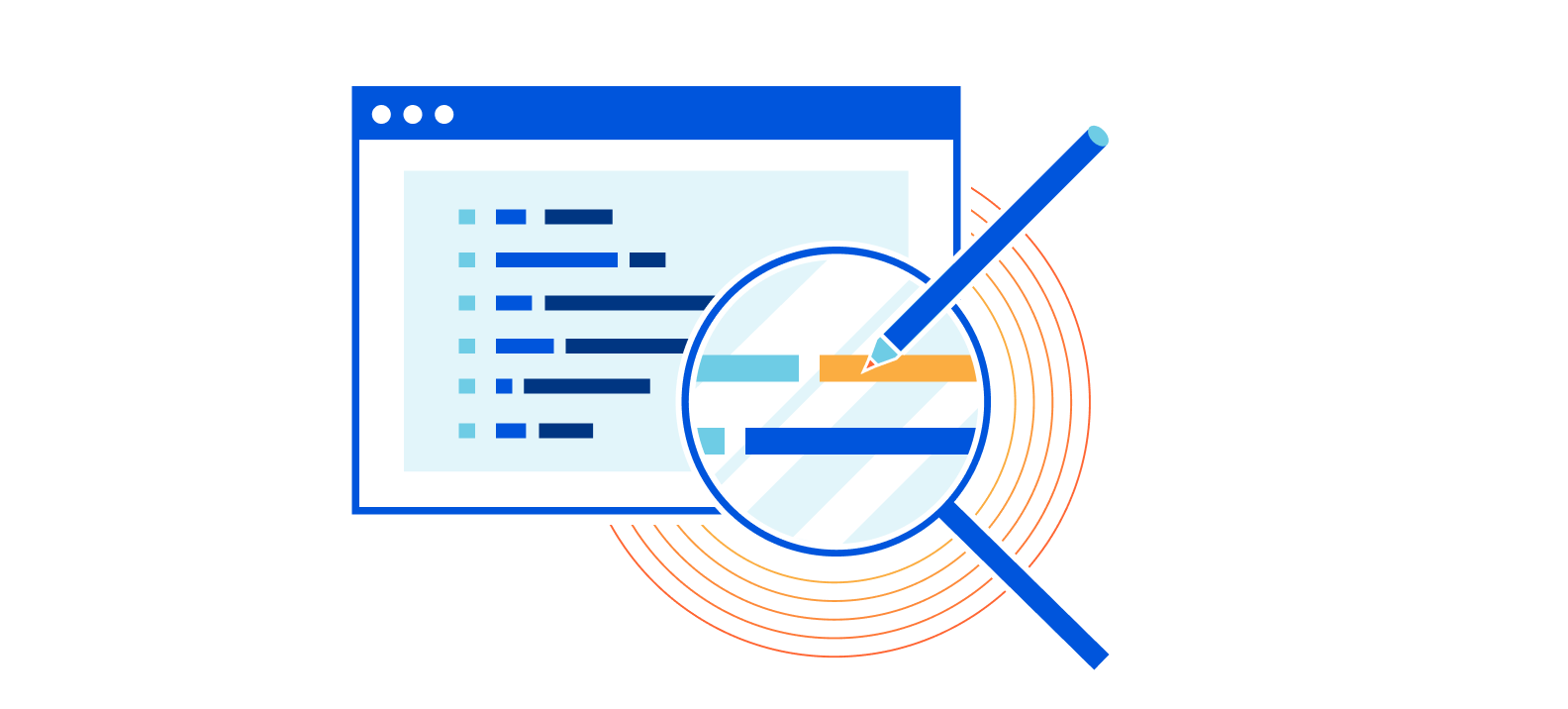
Managed Transforms is the next step on a journey to make HTTP header modification a trivial task for our customers. In early 2021 the only way for Cloudflare customers to modify HTTP headers was by writing a Cloudflare Worker. We heard from numerous customers who wanted a simpler way.
In June 2021 we introduced Transform Rules, giving customers a simple UI letting them specify what the custom HTTP header’s name and value is—either a static string (i.e. X-My-CDN: Cloudflare) or a dynamically populated value (i.e. X-Bot-Score: cf.bot_management.score).
This made the job much simpler, however there is still a good amount of thought required—with a number of potential drop-off points on the user journey. For example, in order to dynamically populate the bot score into the value of an HTTP request header, the user needs to know the correct field name. To find that they'll need to go to the documentation site, find the correct section, etc.
When we analyzed how our customers use Transform Rules we found a set of very common use cases in the data. Four of the top eight fields used were relating to bot management; customers wanting to have the Continue reading
Introducing the Two-Minute Toolkit Podcast
One expert. One topic. A two-minute conversation to offer expertise on a single point of discussion in enterprise IT strategy.Learning and development initiatives at Noction
The post Learning and development initiatives at Noction appeared first on Noction.
Cloud Notes: AWS IAM
AWS Identity and Access Management (IAM) provides access control for AWS users/applications to the various AWS services and resources. Features Available only in the Global region Globally resiliant service Always free service Account Types There are a number of account...continue reading
Juniper Apstra Part I – Introducing a true IBNS
With this post, we kick off a new series based on Juniper Apstra. This post serves as an introduction to Apstra - we’ll look at what a true IBN system is, how relational and graph databases are different (and why graph databases are ideal for network infrastructure), concluding with some general workflows in Apstra.
Telecom Industry Takes the Workforce Challenge to Staff Internet-for-All Broadband Rollout
Demand for skilled staff is sky high, but not supply, for the largest-ever U.S. infrastructure effort. Associations, carriers, and vendors look to fill the staffing gap as spending on fiber broadband climbs.Hedge 136: The IPv6 ULA Mess
IPv6’s designers built the concept of Unique Local Addresses, or ULAs, into the addressing architecture to make network address translation unnecessary for IPv6 deployments. As with many other plans of mice and men, however, the unintended consequences of what is a good idea tend to get in the way. Nick Buraglio joing Eyvonne Sharp, Tom Ammon, and Russ White to discuss the many problems of IPv6 ULA, why it isn’t practical in most network deployments, and the larger question of how standards bodies sometimes fail to consider the unintended consequences of a good idea.
Day Two Cloud 153: IaC With GPPL Or DSL? IDK
On Day Two Cloud we’ve had a lot of conversations about using infrastructure as code. We’ve looked at solutions like Ansible, Terraform, the AWS CDK, and Pulumi. Which begs the question, which IaC solution should you learn? A Domain Specific Language (DSL)? A General Purpose Programming Language (GPPL)? Something else? We discuss.Internet Explorer, we hardly knew ye

On May 19, 2021, a Microsoft blog post announced that “The future of Internet Explorer on Windows 10 is in Microsoft Edge” and that “the Internet Explorer 11 desktop application will be retired and go out of support on June 15, 2022, for certain versions of Windows 10.” According to an associated FAQ page, those “certain versions” include Windows 10 client SKUs and Windows 10 IoT. According to data from Statcounter, Windows 10 currently accounts for over 70% of desktop Windows market share on a global basis, so this “retirement” impacts a significant number of Windows systems around the world.
As the retirement date for Internet Explorer 11 has recently passed, we wanted to explore several related usage trends:
- Is there a visible indication that use is declining in preparation for its retirement?
- Where is Internet Explorer 11 still in the heaviest use?
- How does the use of Internet Explorer 11 compare to previous versions?
- How much Internet Explorer traffic is “likely human” vs. “likely automated”?
- How do Internet Explorer usage patterns compare with those of Microsoft Edge, its replacement?
The long goodbye
Publicly released in January 2020, and automatically rolled out to Windows users starting Continue reading